Cisco’s Recent Patches Reinforce the Value of Management for Security
%20Ciscos%20Recent%20Patches%20Reinforce%20the%20Value%20of%20Patch%20Management%20for%20Security.png)
In April 2023, Cisco issued security advisories for several of its products. While it’s normal for technology companies to release security patches for vulnerabilities, this instance stands out. Some of the vulnerabilities were super risky.
The patched Cisco products also included hardware, the ASR 5000 Series routers. The other impacted products included the Industrial Network Director (IND), Modeling Labs, and BroadWorks Network Server.
What’s extraordinary is that most security flaws were critical and required immediate fixes. The news essentially reiterates the importance of maintenance for security. Whether it’s hardware or the software running on it, maintenance and support are key to preventing malicious parties from exploiting vulnerabilities.
Cisco Patches Critical Security Flaws
Cisco’s ASR 5000 Series routers had critical vulnerabilities, mainly in StarOS, the OS for these routers, and other products. The vulnerability (CVE-2023-20046) results in privilege escalation with key-based SSH authentication.
Here’s what could happen if someone exploited this particular vulnerability of the routers:
An attacker can send an authentication request over SSH using an IP address linked with a high-privilege account. However, instead of providing the SSH key for that particular account, they could provide the SSH keys for a low-privilege account.
In other words, the system was accepting low-privilege SSH keys as high-privilege. Because of this weakness, anyone with low-privilege SSH keys could access things only reserved for high-privilege access.
Updating StarOS to the latest version with the security patch fixes this vulnerability, which is quite critical and exposes high-level access privileges.
The Cisco IND received two patches for its vulnerabilities, one of which was critical. The critical flaw CVE-2023-20036 impacted the web-based user interface. Exploiting this vulnerability, remote attackers could execute commands on the Windows OS with administrative rights. This is because of improper input validation when uploading Device Packs.
Modeling Labs, a network simulation tool, was also impacted by a similar critical vulnerability that could allow an attacker to get administrative access to the tool’s web interface.
Patch Management: An Important Piece in the Security Puzzle
Patch management refers to distributing and applying software updates, particularly fixing security vulnerabilities. These patches are essential for fixing the problem before it can be exploited.
Patches are distributed by hardware OEMs, OS, and software vendors, often soon after the vulnerability is identified. While OEMs and vendors can make the patches available, the responsibility to install and apply those patches falls on the customers.
Network equipment, OS, database management, and enterprise tools are often fixed with patches. For enterprises with a large IT footprint, there’s a clear need for processes regarding patch management. With many IT assets in use, it’s imperative to keep tabs on any announcements of patch releases.
Furthermore, patching the vulnerability isn’t the only option. Depending on the specific vulnerability, there may be workarounds, such as compensating controls.
Patch management is essentially a part of security management. However, it’s also intrinsically linked with IT asset management. Effective asset management is critical for identifying vulnerabilities and implementing solutions (including security patches).
Without an effective patch management system, enterprises risk being unaware of critical security vulnerabilities and not applying the patches in time to prevent exploitation.
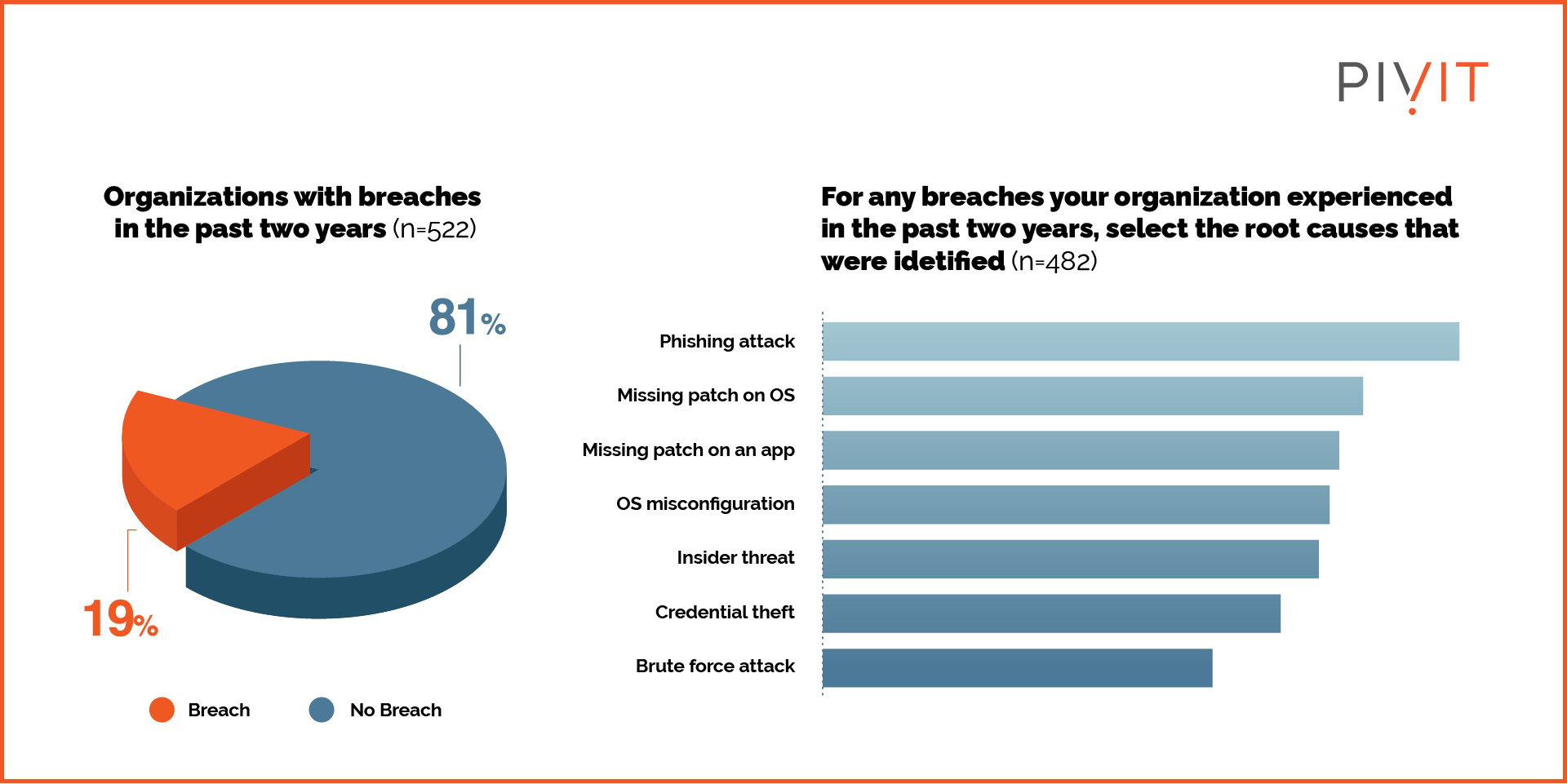
(Source: data)
According to a Ponemon Institute report, 57% of data breaches are attributed to poor patch management.
Steps to Implementing Effective Patch Management
While OEMs and vendors announce patches online and notify customers through email, you don’t want to take the chance of missing the announcement.
In a multi-vendor environment with assets obtained from multiple channels, you may not even be notified in time. Therefore, it’s imperative to be proactive with security patches.
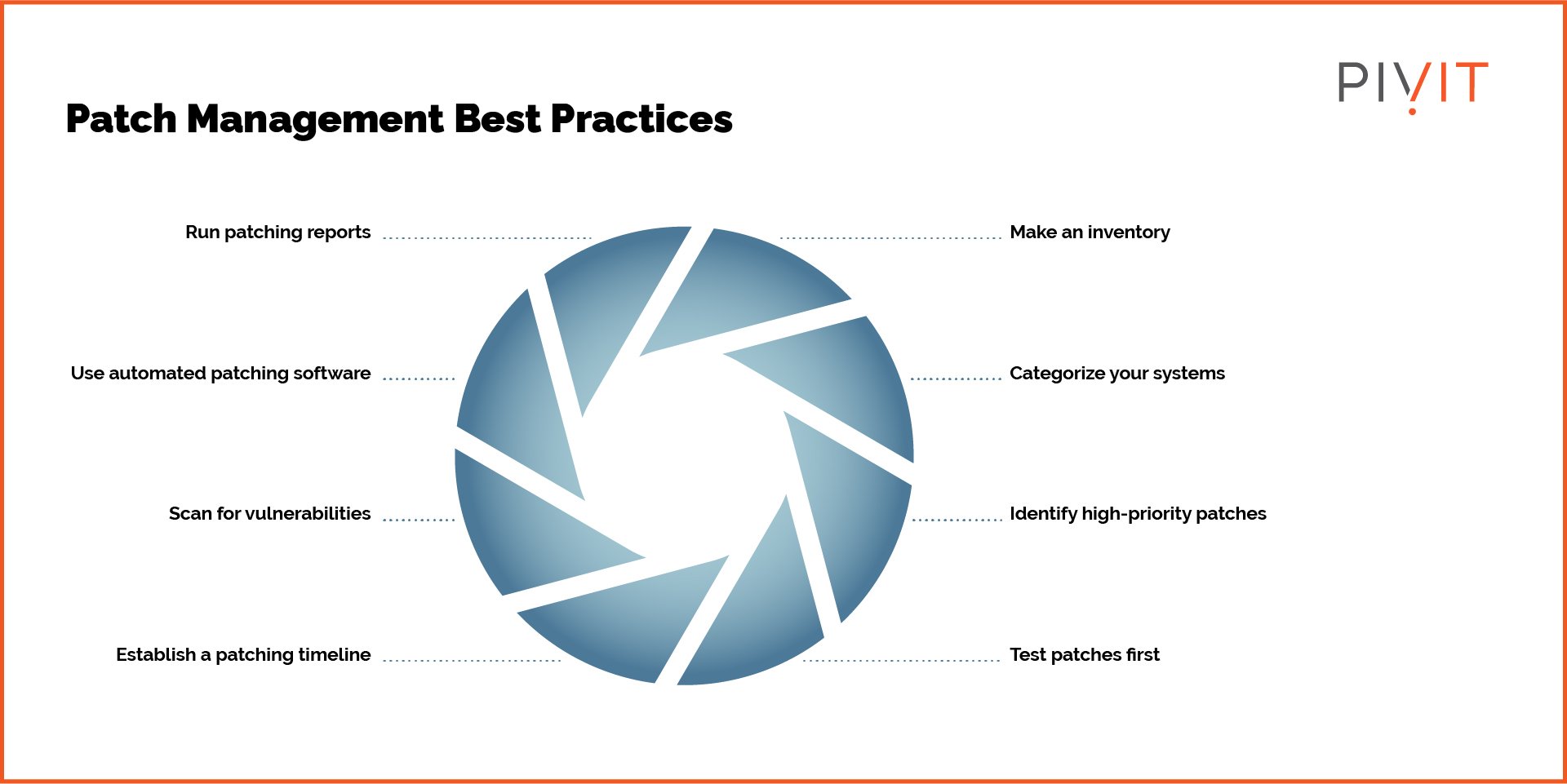
Here are the steps to effective patch management:
- Identify IT Assets: You need an inventory of your IT assets for increased visibility. An IT asset management solution can help identify all the hardware and software assets.
- Categorize by Priority: The next step is identifying the most critical assets for your network and operations. For instance, assets like servers, routers, switches, and network management software, are vital for transferring data and, therefore, high-priority assets. Giving priority to critical devices and tools for applying patches ensures these assets are always up to date.
- Create a Patch Management Policy: Define the process and policy for patch management. For instance, define which assets will be configured for automatic patch installs and which will require manual intervention. Also, define the roles of the people responsible for patching.
- Monitor for New Patches: Catalog each OEM and vendor in your enterprise infrastructure and find out the main pages on their websites for such alerts and announcements. Sign up for vendor alerts for prompt updates about the release. In simpler words, create a system for vulnerability/patch tracking.
- Implement and Test Patches: Whenever a security patch is released, implement it immediately and test the impacted asset to ensure it runs seamlessly. Test for the particular security vulnerability where possible to ensure the patch performs its job.
- Create Reports: Create monthly or quarterly reports for security patches implemented to report patch management to executives, especially those responsible for asset acquisition. These reports can shed light on the frequency of patches for each OEM.
Maintaining Legacy Hardware Is Just as Important
Most security patches are for software products, but there are also critical firmware patches for hardware. Hardware maintenance impacts overall infrastructure security.
The hardware that has not reached the end of support will continue to receive security patches for identified weaknesses. However, equipment that has reached the end of support from the OEM will usually not receive any more security patches. In such cases, enterprises must maintain the equipment with a third party.
Third-party maintenance (TPM) for legacy hardware can help identify and resolve security vulnerabilities even without official interference from the OEM.
As many enterprises continue to operate legacy equipment that has officially reached the end of service life (EOSL), TPM can be the alternative.
Vulnerability assessment, patch management, and hardware maintenance are crucial cybersecurity strategies for profound enterprise security.
The Takeaway
Cisco’s announcement of multiple patches for critical security vulnerabilities should inspire enterprises to adopt standardized patch management and maintain hardware with up-to-date support contracts.
If security vulnerabilities are not fixed in time, your enterprise infrastructure can be exposed to data breaches and malware. Such security incidents are not uncommon and can cause damages worth millions.
If your enterprise runs on legacy equipment no longer supported by the OEM, PivIT’s short-term maintenance can be a viable alternative. With cost-effective device maintenance, you can ensure that any vulnerabilities and faults are dealt with immediately.
Learn more about OneCall, the holistic IT maintenance solution for long-term and short-term needs.


