5 Best Practices for Data Protection in Data Centers in 2023
%205%20Best%20Practices%20for%20Data%20Protection%20in%20Data%20Centers%20in%202023.png)
In a period marked by economic uncertainty, you’d expect the biggest concern for IT leaders would be higher costs. However, that’s not the case. According to Rackspace Technology research with 1,420 IT leaders, cybersecurity remains the top concern. And rightly so, as the ransomware threat only seems to grow stronger.
Data centers are a frequent target of ransomware attacks because data holds power. So it goes without saying that data centers, regardless of niche or size, need to beef up data security.
In 2022, over 493 million ransomware attacks were detected worldwide, lower than the all-time high of 623 million in 2021. Nevertheless, the cost of ransomware can be crippling. The IBM Cost of Data Breach report puts the average data breach cost at $4.35 million.
This article presents tried and tested practices for reliable data protection that data centers can adopt.
5 Data Protection Best Practices for Data Centers
The following five practices will help improve digital security for data. However, it’s equally important to ensure the physical safety of your on-premise data center.
Implement Isolated Backup Environments
While securing data is crucial, protecting backups is arguably even more important. If your backup is compromised, there’s no coming back. Attackers know that data centers have backups and try targeting backup data to block access. Therefore, it’s imperative that your backup environments are separate.
Your backup is your last line of defense, and as such, it should be inaccessible to anyone who gets into your main storage. The backup environment should be completely isolated with unique credentials and authentication protocols.
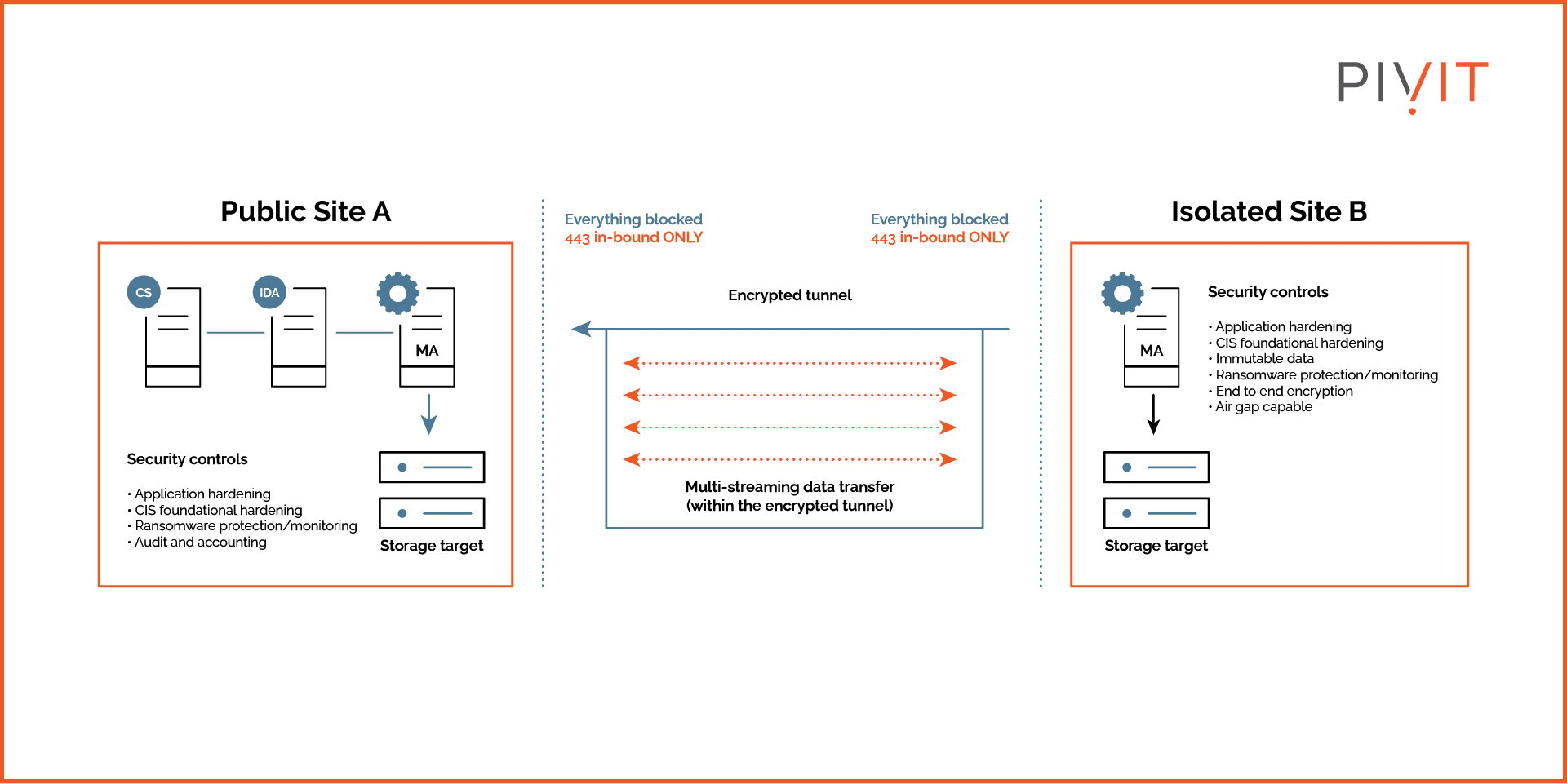
Isolating backup makes it difficult for the attacker to infiltrate the backup system to entrap the enterprise.
Furthermore, it helps immensely if the backup data is immutable. Such backups cannot be modified or deleted. Immutable security backups are fully managed, end-to-end solutions that not only create a gap between the production and backup environments but also prevent modifications to the backup should that gap be bridged.
Simply backing up data locally isn’t enough to protect it from attackers. Plus, isolated backups can make data recovery easier and faster.
Proactively Discover Anomalies With Threat Hunting
When attackers breach a network with compromised credentials or through another vulnerability, it can take weeks or months before they attack data. They use the time to move around and explore the systems, gradually planning the big attack.
What if they could be stopped in their tracks? That’s where threat hunting comes in. It’s the practice of searching for and identifying unknown and ongoing threats. It’s a proactive approach that can help discover and remediate the sophisticated threats that make it past tier 1 and tier 2 security layers.
Typically, data centers hosting highly sensitive data employ threat hunting. But with ransomware attacks becoming sophisticated and deeply penetrative, all data centers should undertake this security practice.
Threat hunting builds upon the existing security systems, especially the automated ones that collect the data. That data is then analyzed by other tools and humans to identify abnormalities. But what makes threat hunting even more influential is that it doesn’t just tell you something is wrong but can also tell you when it went wrong.
Create a Foolproof Data Policy
A data protection or governance policy helps mitigate internal and external threats. A comprehensive data policy defines who can access what data at what time and for how long. The more detailed the policy is, the more control you have over data access.
More often than not, unauthorized access leads to invasive attacks. The 2023 Thales Data Threat Report found that most cloud data breaches resulted from human errors. A strong data policy can prevent such errors from costing data centers millions.
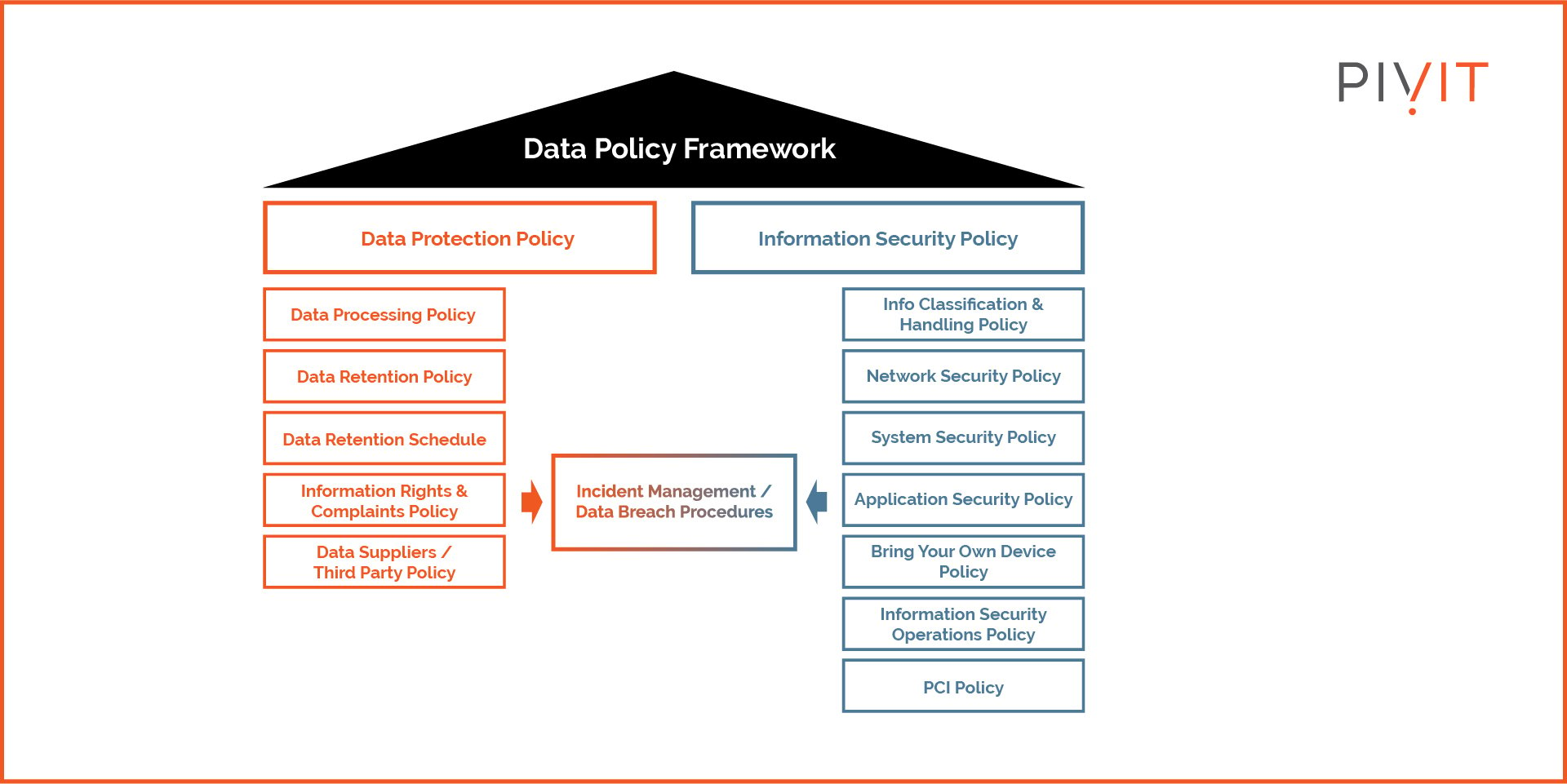
Moreover, data policy doesn’t just enhance data security, it also defines data usage, which is directly linked to privacy regulations. With the policy putting the regulations in black and white, it’s easier for security teams to implement the right access and transfer restrictions to prevent non-compliance with applicable regulations.
Manage and Review Access Controls
Implement thorough access controls based on the principle of least privilege. In other words, data access should be limited to the extent of necessity to perform the job. Managing and periodically reviewing access controls is critical for data security.
Access controls ensure that only authorized personnel and applications can access sensitive data. While these controls alone may not prevent attacks, they minimize the chances greatly.
The access can be based on a well-defined framework, which, in turn, is based on your data policy. These controls need to be granular. For instance, role-based access control (RBAC) is widely used in organizations to allow only select users to write or retrieve certain data. This is based on the user’s job or clearance level. It ensures that no one besides them can touch the data, even from inside the enterprise.
More importantly, access control should be monitored and reviewed regularly. For example, accessing certain data may be temporary for performing a specific job. Once that job is done, the user’s privileges should be rolled back to their previous level. This can only be done if the access control is reviewed periodically and updated.
Invest in Security-Focused Hardware
Equipment manufacturers are designing hardware with built-in security features to address the rising cyber threats. This does not eliminate the need for dedicated security solutions.
However, adding such devices to your architecture can bolster security and add another layer of authentication and threat detection. Such security features prevent hardware exploitation and firmware modification.
For example, the Cisco 4000 Series Integrated Services Routers have multiple security features, including Dynamic Multipoint VPN, intrusion prevention, and zone-based firewalls.
Similarly, investing in storage options with advanced security features can offer protection from attacks that make it to the stored data. Hardware-based encryption has proven monumental in protecting data from threats like malware and ransomware. With encryption keys isolated from the host, attackers can’t decrypt data even if they somehow get access to it.
So the next time your data center hardware is up for a refresh, make security a critical criterion for selecting the replacement.
Procure With PivIT
Whether looking for a next-gen firewall or server, PivIT can be the go-to for procuring equipment that prioritizes data security. At the end of the day, your data is only as secure as your infrastructure. In addition to investing in reliable software-based security solutions, it’s also important to maintain and refresh equipment to prevent exploitation at the hardware level.
PivIT offers diverse hardware options for data centers from leading manufacturers. Learn more about infrastructure procurement with PivIT!


