The Solutions Guide for Third-Party IT Maintenance and Compliance
%20The%20Solutions%20Guide%20for%20Third-Party%20IT%20Maintenance%20and%20Compliance.png)
We live in a data-driven age, where people and organizations produce over 1.145 trillion MB of data daily.
With cybersecurity attacks that steal confidential data becoming ever so common, the regulations pertaining to data security have become increasingly stringent.
Small and large businesses must adhere to their regions' data protection and privacy regulations. Data centers, in particular, must pass compliance certifications as they hold public and private data. Failing to comply with applicable compliance standards can result in penalties and irreparable reputational damage.
IT maintenance has a big role to play when it comes to data compliance.
In this article, we will discuss the following:
- Data protection regulations.
- The importance of those regulations.
- The role of maintenance, especially through third parties, for compliance.
Not the article you were looking for today? Try these out:
- Adding Field Services to Your IT Projects to Fill Gaps
- Want to Consolidate Your Data Centers? Here Are the Pros and Cons
- What Happens Behind the Scenes of Sparing Equipment with TPM
Understanding Data Compliance
Data compliance is a process that identifies and implements the appropriate governance for data protection.
Organizations must follow numerous regulations and standards to ensure the data they collect from people is secure.
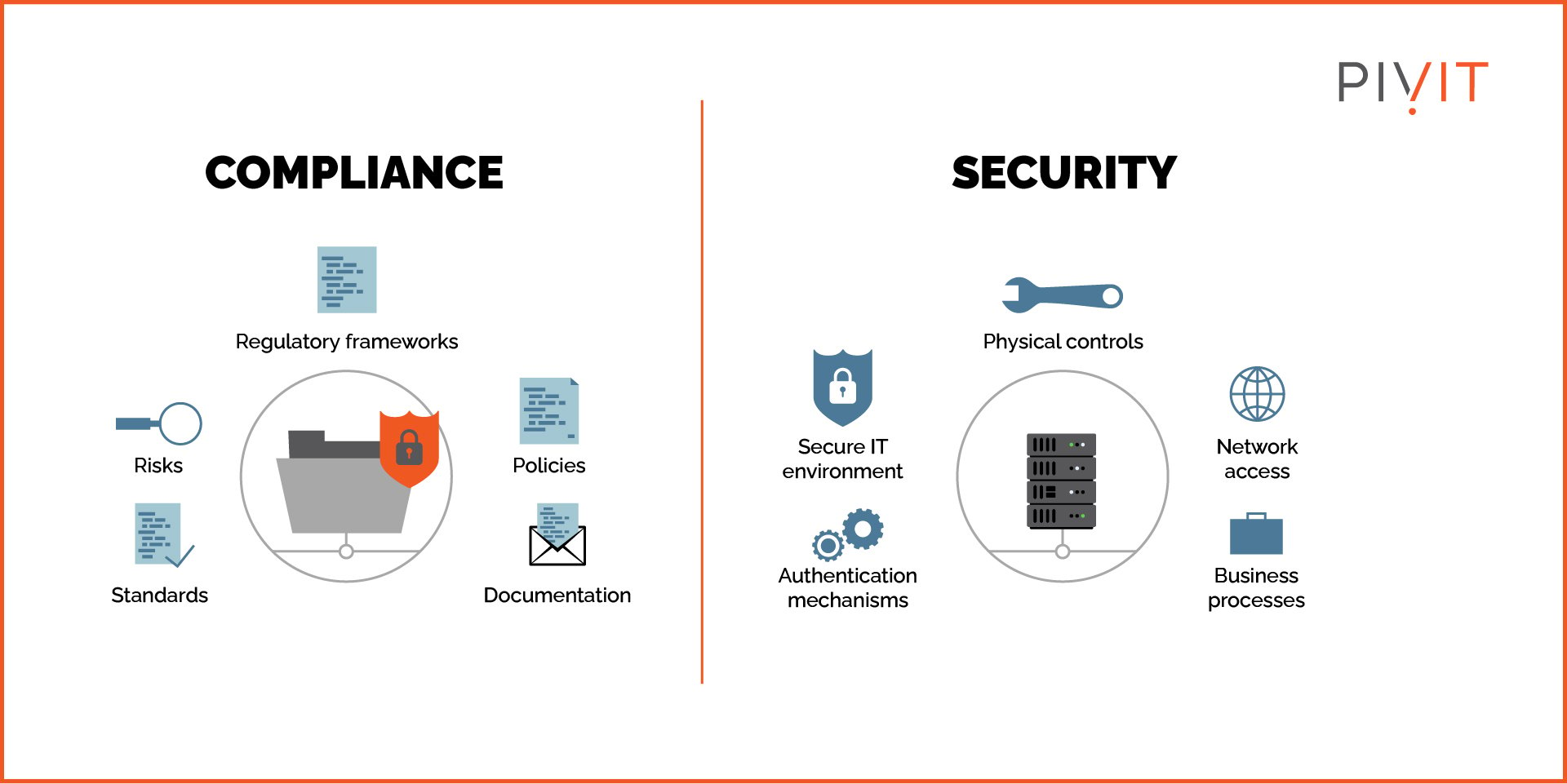
While organizations can voluntarily follow some security standards, regulations imposed by governments must be complied with. Different regulations or standards may apply depending on where the business operates, the industry it belongs to, and where the data it gets comes from.
For international organizations operating in different regions, it’s necessary to ensure compliance with all applicable regulations. Data protection and privacy regulations have become stricter due to rising data breaches.
Why Is Data Compliance Important?
Data protection standards and regulations obligate necessary security measures to protect customer data. So, in a way, complying with such regulations can help data centers and other organizations heighten their cyber security.
In case of a data breach incident, the organization may be fined by the regulatory body. And such fines can range anywhere from a few hundred thousand dollars to tens of millions.
In 2020, HIPAA non-compliance settlements amounted to over $13.5 million. The insurance company Anthem paid the most significant HIPAA settlement to date, $16 million, in 2018. These figures show that non-compliance can be costly.
Aside from penalties, non-compliance can also stain the reputation of the company. People are growing wary of their data and privacy, with most Americans in a Pew Research survey on privacy saying that they feel their data is less secure.
If an enterprise fails to protect consumer data, it can be quite challenging to gain customers' trust again.
Common Data Center Regulations
Data protection regulations and standards are essential for any enterprise handling data. However, data centers must comply with data regulations because their very business is built around data.
If a data center is breached, it can have a domino effect on all its clients as their data would get compromised. This is why identifying and complying with regulations is integral to overall network security for data centers.
Here are the most common certifications and regulations that may apply to data centers around the world:
ISO/IEC 27001:2013
The International Organization for Standardization’s ISO/IEC 27001 is an international standard that assesses how an organization protects private and sensitive data. An organization with ISO/IEC 27001 certification identifies risks and vulnerabilities and resolves them while also training employees to keep customer data secure.
SOC 2 Reports
A System and Organization Controls (SOC) 2 report evaluates a facility’s procedures and policies regarding data security, integrity, confidentiality, privacy, and availability. The report checks whether the organization meets the Statement on Standards for Attestation Engagements (SSAE) 18 requirements.
This report can be instrumental for evaluating the security measures of a data center and whether or not they meet the requirements as per SSAE 18.
There are two types of SOC 2 report audits. Type I checks the security effectiveness at a specific time, whereas Type II checks it for a period, typically six months to a year.
PCI DSS 4.0
The Payment Card Industry Data Security Standard, PCI DSS, is a control standard for electronic card payments. It’s applicable internationally to any entity that processes card payments and collects financial information. The standard ensures that consumer financial data is secure.
This certification requirement applies to data centers that store financial transaction information for any industry or business.
HIPAA
Health Insurance Portability and Accountability Act (HIPAA) is a compliance standard for protecting the personal health data of Americans. It applies to health providers and insurance companies to ensure that the personal data they collect from people is secure. This compliance standard applies to all data centers owned or used by companies in the healthcare industry.
GDPR
General Data Protection Regulation (GDPR), introduced by the European Union (EU) in 2018, has become the gold standard of regulations to protect consumer data. It’s also one of the strictest regulatory frameworks with high penalties.
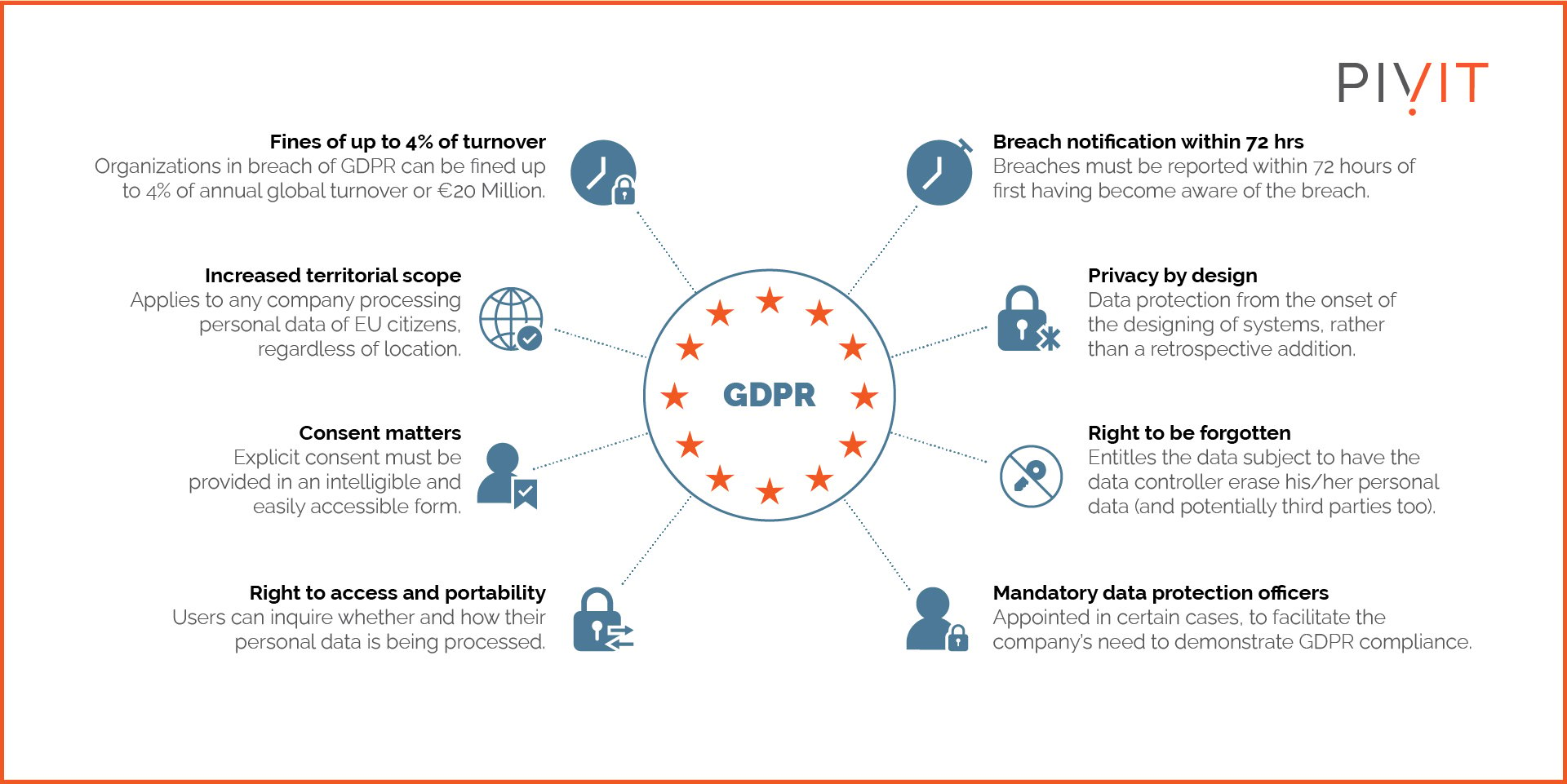
GDPR lists requirements that companies and their data centers must meet to ensure the safety of data of people from the EU and the UK. GDPR regulations also outline that companies must notify people when collecting data.
How Is Maintenance Relevant to Data Compliance?
Maintenance is intrinsically linked with data compliance, as a strong maintenance strategy is critical for better security.
Some common attack vectors are outdated equipment, old firmware, and weak or no security patches. A well-rounded maintenance strategy can help keep infrastructure up to date, backed with spares in case of failure. It also ensures that operating systems and firmware for hardware are up to date and that the correct configuration is applied.
While maintenance, whether provided by the original equipment manufacturer (OEM) or a third-party maintenance (TPM) provider, is not directly responsible for security, it can help address security concerns, especially concerning hardware.
Poorly maintained equipment is also poorly secured, raising the risk of attacks from malicious actors. A data center with subpar maintenance couldn’t get the necessary certification or meet regulatory requirements.
Third-Party Maintenance Providers’ Role in Data Centers
Data centers that rely on TPM providers must discuss compliance issues with their providers to ensure that both are on the same page. It is critical to work with a maintenance provider that values data compliance and understands its importance.
TPM providers are responsible for IT equipment maintenance and don’t provide security solutions or evaluations. However, their maintenance is part of the extensive security strategy ensuring data centers comply with data protection regulations.
One way to gauge whether a TPM provider considers data compliance necessary is to check whether it has any certifications or has had any incidents of non-compliance.
Trust OneCall for Maintenance
PivIT’s global maintenance service, OneCall, is a reliable solution for data centers looking to partner with a provider that values data protection and privacy. OneCall provides flexible maintenance solutions that ensure all critical equipment is in good shape and performs well.
In addition, the Sparing Integrity Program guarantees spares for critical equipment with quick service level agreements (SLAs). With a global mindset and quick logistics connections, OneCall is the answer for data centers operating globally and subject to different security regulations.
With OneCall as your maintenance partner, you can stay on top of essential hardware updates, achieve necessary security benchmarks, and comply with data protection regulations. Trust OneCall when it comes to this critical area of your business.


