The 2023 Guide for Everything Related to the AAA Framework
.png)
Not all users have the same or full access to the network. Different types of users are provided with an appropriate level of authority and access to protect the integrity and usability of the data and the network.
It is accomplished by using different methods for identifying the users before they are allowed to do anything, and based on their privileges being provided corresponding access to internal resources. Last but not least, each action performed by users should be “recorded” and saved as a log, so there is evidence of everything that has been done.
In this article, we will provide the following:
- An overview of the AAA solution,
- Find out what AAA stands for,
- Get familiar with the three main services, and
- Compare local AAA with centralized or external AAA.
Not the article you are looking for? View our other popular articles:
- It's About Time – The Importance of NTP for Networks
- A Better Way to Buy Servers to Retrieve Data Instantly
- Must-Have Port Security: Simple but Efficient Layer 2 Protection
AAA Overview
In enterprise networks, only authenticated users can access specific network devices or use some services unless authentication is not required.
In a small network, local authentication is suitable, which means each device is responsible for authenticating the users against the credentials in their local database. However, things can get out of control when the network grows; and the number of network devices increases.
For example, a request for adding a new user account reflects on adding the new account on all network devices, which provides extra complexity and a possibility for misconfiguration. And on the flip side, when you add a new network device to the network, you have to add all existing user accounts from existing databases to the local database of the new device.
However, authentication is not the only part of the process. Additional services such as authorization and accounting must be used for each user trying to access network devices or resources in the enterprise.
This is the moment when AAA comes to play as a perfect solution. AAA stands for authentication, authorization, and accounting, where each service has a different responsibility.
Authentication is about determining the users’ identities, authorization is about defining the privileges they get after successful authentication, and accounting keeps track of what those individual users have done.
AAA in Action
The way the AAA process works is straightforward.
During an authentication process, the user is challenged to identify themselves and provide any proof of identity. The most common form of user authentication is a combination of username and password, but it can also be a digital certificate or a fingerprint.
After successful authentication, the user is authorized to perform what privileges assigned to them allow them to do. Based on predefined privileges, like the department where the user belongs, the user’s location, or the device type used, the user may be allowed or denied access to certain resources.
The last part is accounting, or keeping logs of everything any user has done. It means keeping details of the session such as dates and times, users’ IP addresses, accessed resources, configuration commands entered on network devices, and so on.
Local vs. Centralized Deployment
When implementing AAA, the data required for the services to run can be stored locally or centrally.
You can use the local database on each network device, where all AAA authentication and authorization data is stored (as shown in the image below). It is best for small networks or branch offices, implementation-wise and cost-wise.
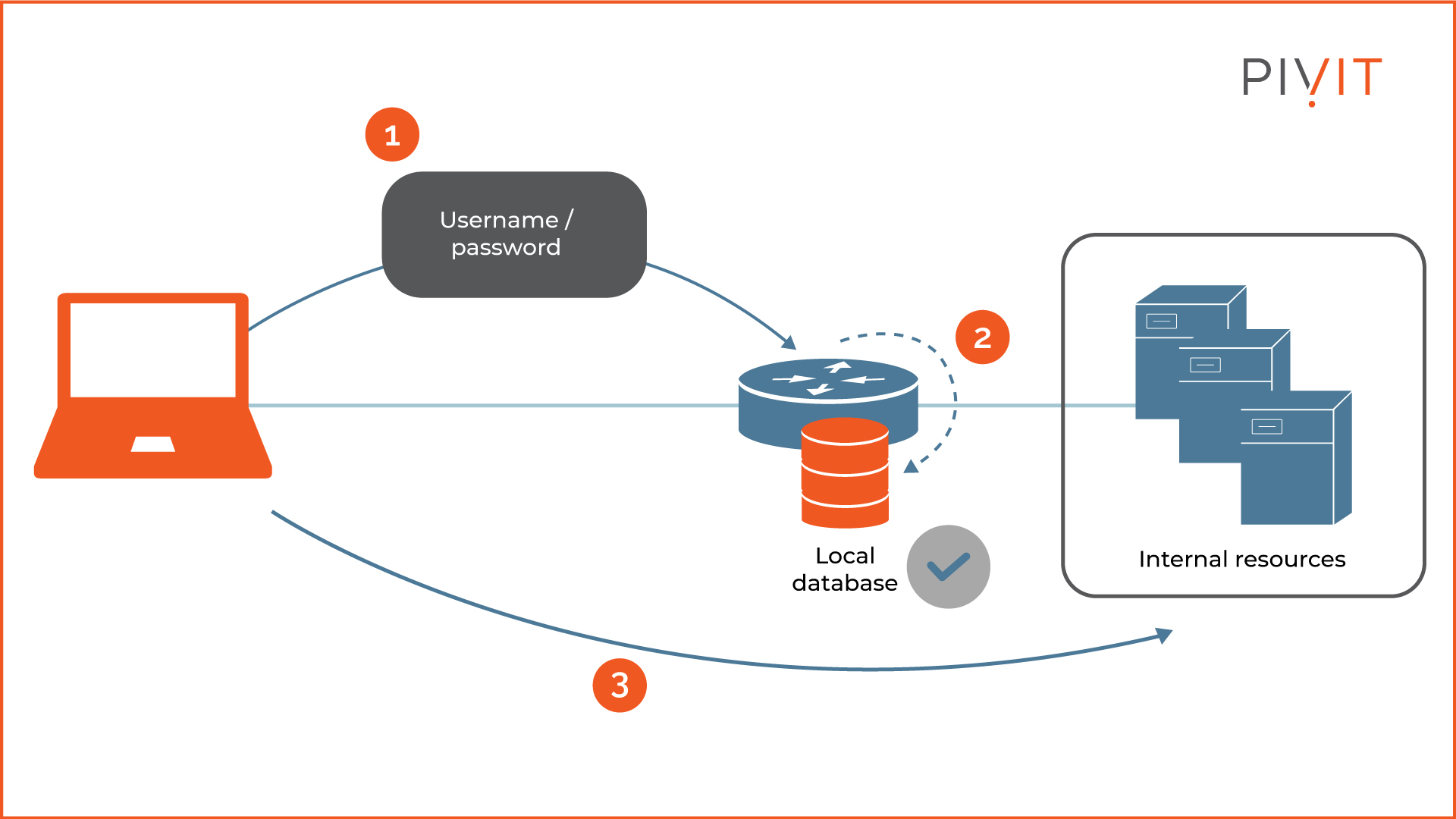
But, the local AAA database does not scale well in large and complex networks.
When there is a need for a change, like updating a password or adding a new user, that change must be performed individually on each network device. It becomes a huge problem when thousands of devices are affected in the network.
_________________
Tired of your maintenance creating new problems instead of solving them? Try PivIT’s OneHub software to aggregate all your IT assets and maintenance contracts – for free – to make management simple.
_________________
On top of that, the local AAA does not support accounting, which is a crucial part of the AAA process.
Centralized AAA is preferred over local AAA, except for small network deployments like branch offices.
With centralized AAA, all authentication requests are relayed to an external server (as shown in the image below) which permits or denies the users according to its user database by instructing network devices to take appropriate action.
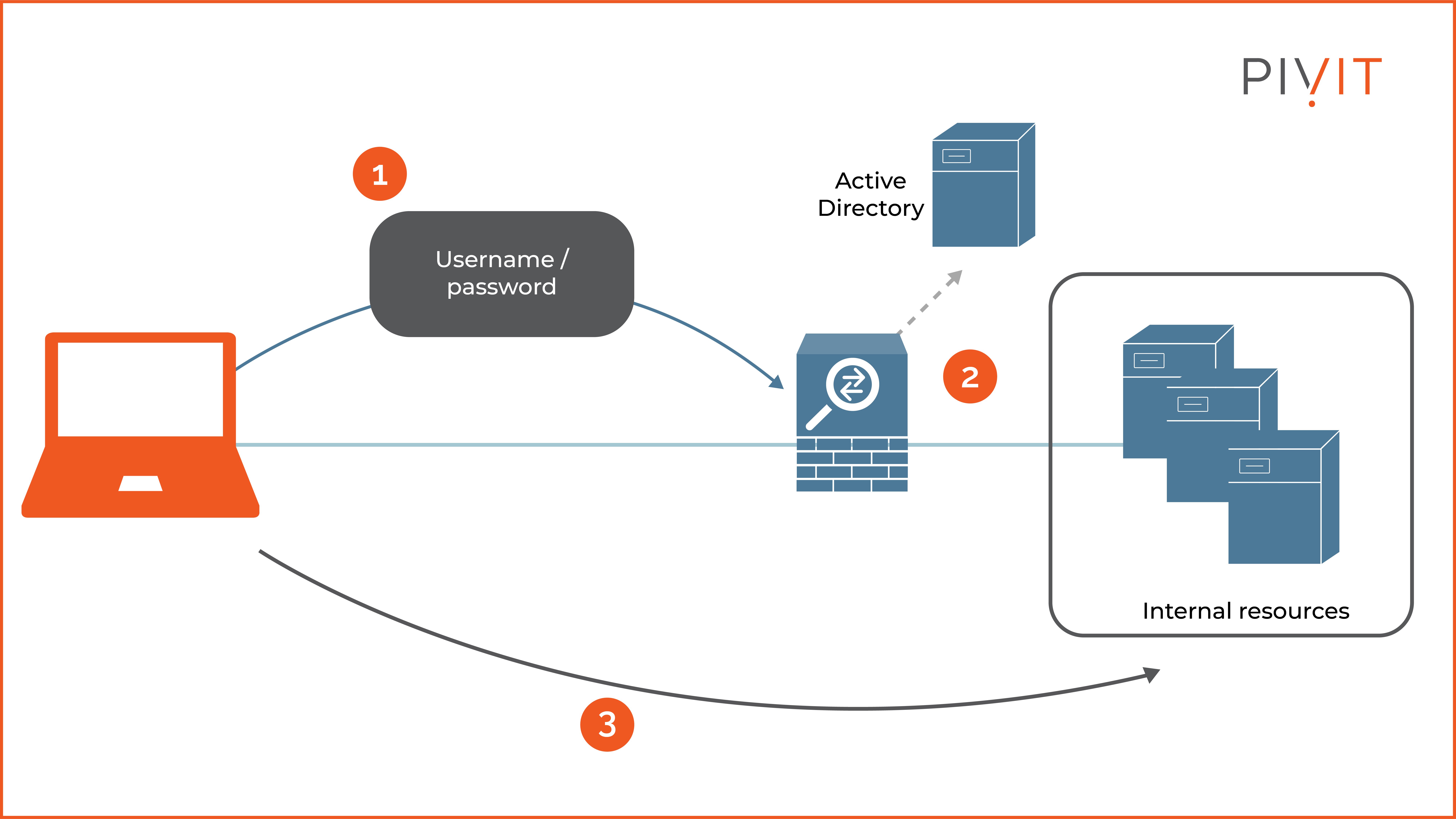
Moreover, the overall configuration and maintenance are more manageable, meaning authentication and authorization data are managed centrally on a single server and then made available to all network devices that need it. Therefore, when a change is required, it is only performed on a centralized server and then automatically inherited by the affected devices in the network.
Because an external server is used for storing accounting records, accounting is not an issue like the local AAA approach.
Remember, even though a centralized AAA system can independently maintain databases for the services, it is common to use an existing user repository such as Active Directory when one is available in the network. This way, you can rely on existing data instead of building the databases from scratch.
AAA Protocols
When using centralized AAA, everything is based on the external server where authentication, authorization, and accounting processes occur. For this approach to work, network devices need to use a protocol to exchange AAA data with external servers.
The two popular and commonly implemented AAA protocols for external AAA services are RADIUS and TACACS+.
RADIUS
RADIUS stands for Remote Authentication Dial-In User Service and is a standard protocol that relies on the UDP protocol for providing AAA services.
Because the RADIUS protocol combines authentication and authorization in a single service:
- It listens on UDP port 1812 for authentication and authorization data and,
- It listens on UDP port 1813 for accounting data.
Although it obscures the passwords that are exchanged, it does not provide any other level of protection, so the rest of the data is sent in clear text.
The RADIUS protocol is best suited for network access requirements, such as providing access to users to different parts of the enterprise network or available services.
TACACS+
TACACS+ is a Cisco proprietary protocol with a similar role to the RADIUS protocol but uses a slightly different approach and is more secure.
TACACS+ separates the authentication and authorization as different services. This protocol uses the TCP protocol and listens on port 49.
One of the advantages of using TACACS+ is the support for encrypting all data that is exchanged between the TACACS+ clients and the server. It is suitable for administrative access, such as accessing and configuring a device.
Integrating Existing Systems
Although you can rely on individual RADIUS and TACACS+ implementations, the AAA servers may additionally consult other systems for certain information.
It is recommended to utilize an existing repository in the organization that contains the data required for the authentication or authorization services instead of implementing the same thing from scratch.
For example, suppose your organization already uses a user ID repository such as Active Directory or LDAP. In that case, you can benefit by integrating that into the AAA system (as shown in the image below).
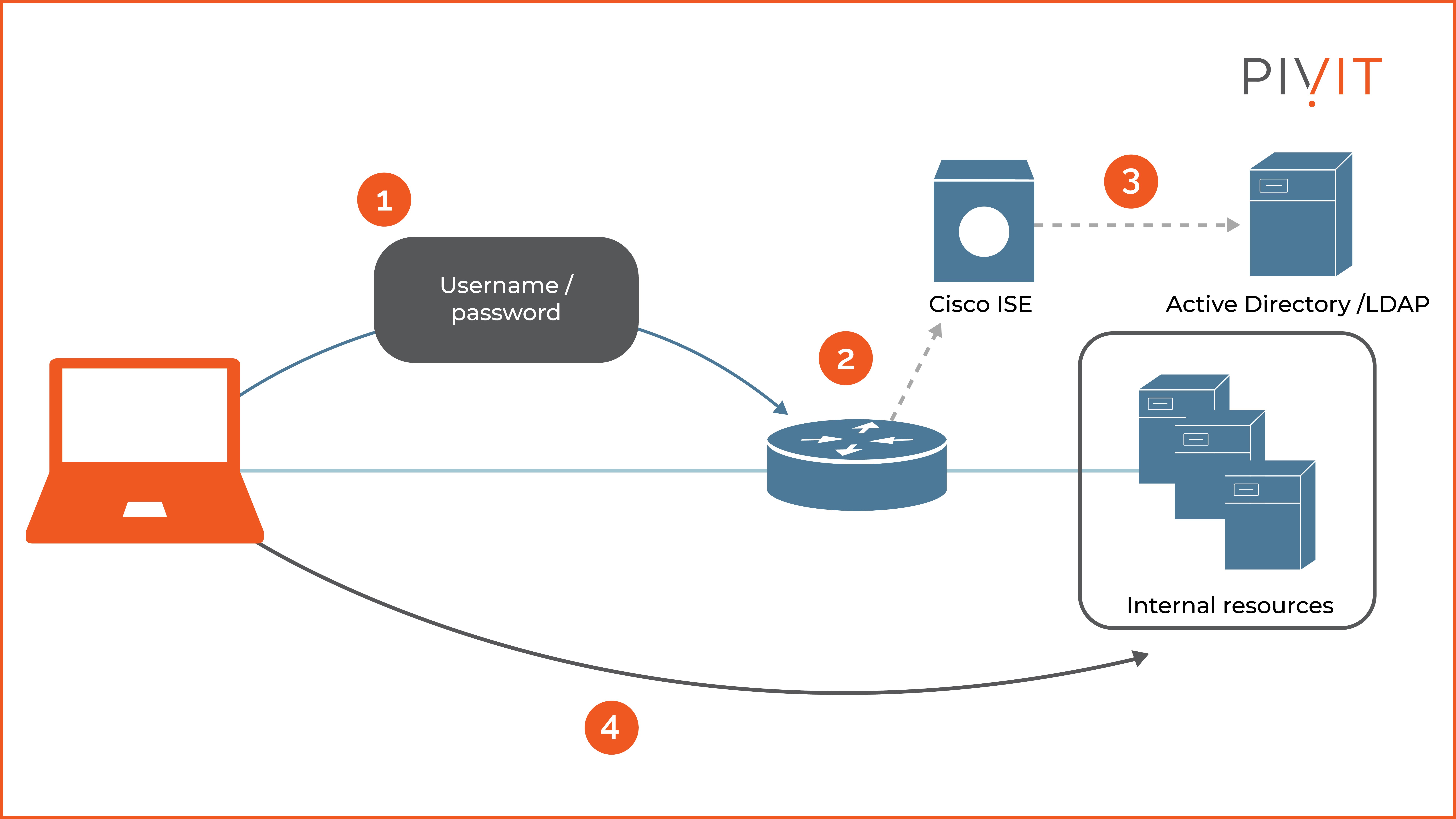
Cisco offers Cisco Identity Services Engine (ISE) as a AAA server, a next-generation identity management system with several additional integrated features such as profiling, posture, BYOD, and centralized web authentication.
On top of that, it supports RADIUS and TACACS+ services and can provide network and administrative access simultaneously.
Get a PivIT Engineer to Help You Out
Although implementing AAA sounds like an easy task, it is a very complex process.
It relies on many independent systems working together to successfully provide authentication, authorization, and accounting services in the enterprise network.
Therefore, it is critical to understand the benefits of each solution as well as the limitations that come with it so you can implement the most appropriate AAA deployment in your network.
Still unsure of how all of this works? PivIT's EXTEND offering can step in to augment your team and remote in to configure your gear with expert-level engineers (SmartHands | EXTEND). If you need someone on-site, we have field services ready at a moment's notice.
Subscribe to our newsletter so you don’t miss out on any future updates!


