Must-Have Port Security: Simple but Efficient Layer 2 Protection
%20(1).png)
A switch port is the main entrance into a network and should have adequate security to combat potential threats. A large network could have thousands of access ports distributed across a campus or building. Are all your ports, used and unused, protected from unauthorized access?
When configuring switches, it is recommended that all ports be secured before being deployed for production use in the network. Usually, the unused ports are configured in access mode, placed in an isolated VLAN, and shut down as a security measure. On the contrary, used ports can be secured by implementing the port security feature.
Download the guide and refer back to it at any time!
In this article, we provide the following:
- an overview of the port security feature,
- the benefits of the port security feature,
- and the configuration steps to deploy the basic functionality of the port security feature.
View some of our other security articles:
- NGFWs: Fortinet FortiGate vs. Juniper SRX Series Services Gateways
- A Must-Have Guide - Risk-Free: Protect Against VLAN and STP Attacks
- Fundamental Firewall Technology Principles: What Is a Firewall?
Port Security Overview
Port security is a Layer 2 security feature that can be implemented on each port on a switch to filter out incoming frames based on the MAC addresses of the connecting devices. As a result, frames are accepted only from secure MAC addresses, allowing only legitimate devices to access the network, while all other devices are denied.
Port security provides not just a simple MAC address filtering based on which end devices are permitted or denied but also helps control a network's unauthorized expansion. Additionally, it can be a very effective method for protecting against MAC address table flooding attacks.
The Default Behavior of Switches
Port security is not enabled by default on Cisco switches. The feature must be enabled individually on each desired interface since it cannot be enabled globally on the switch.
Once the port security feature is enabled, a maximum of one MAC address is allowed per port, and the port shuts down when a violation occurs. However, the default behavior can be modified, and different criteria can be defined, such as setting up a new limit for maximum MAC addresses, designating specific MAC addresses to be permitted, and changing the violation action.
_________________
Hardware Options For You
We make it easy for you to find the switches that support the port security feature. Click below for hardware options or reach out to us and share the project you are currently working on.
_________________
Learning MAC Addresses
MAC addresses that are allowed by the port security feature are stored in the secure MAC address table. Depending on how they are learned, some can be saved for use after a reload, while others are discarded. The three types of secure MAC addresses are:
- Static Secure MAC Address: This type of MAC address is manually defined on the switch and stored in the secure MAC address table. Because the MAC address is available in the switch's running configuration, it can also be saved in the startup-config and, therefore, be available for use after a reload.
- Dynamic Secure MAC Address: This MAC address is dynamically learned on the switch after a device connects to the switch port. By default, the port security feature allows only a single MAC address unless this value is changed to a higher number. Dynamic secure MAC addresses are not stored in the running-config, so they are discarded after a reload. This approach is recommended when the number of MAC addresses allowed on a port is more important compared to which specific MAC addresses are permitted.
- Sticky Secure MAC Address: A sticky MAC address combines static and dynamic MAC addresses. This method allows MAC addresses to be learned dynamically just like the dynamic secure MAC addresses but is added in the running-config like when configuring the static secure MAC addresses. As a result, MAC addresses can be saved (running-config into startup-config) and reused after the switch is reloaded instead of relearning.
How Port Security Works
When a frame is received on a switch port with port security enabled, the source MAC address inside the Layer 2 header of the frame is checked against the available MAC addresses in the secure MAC address table. If an entry is matched, the frame is permitted, and the switch continues with the processing. Otherwise, the frame is denied.
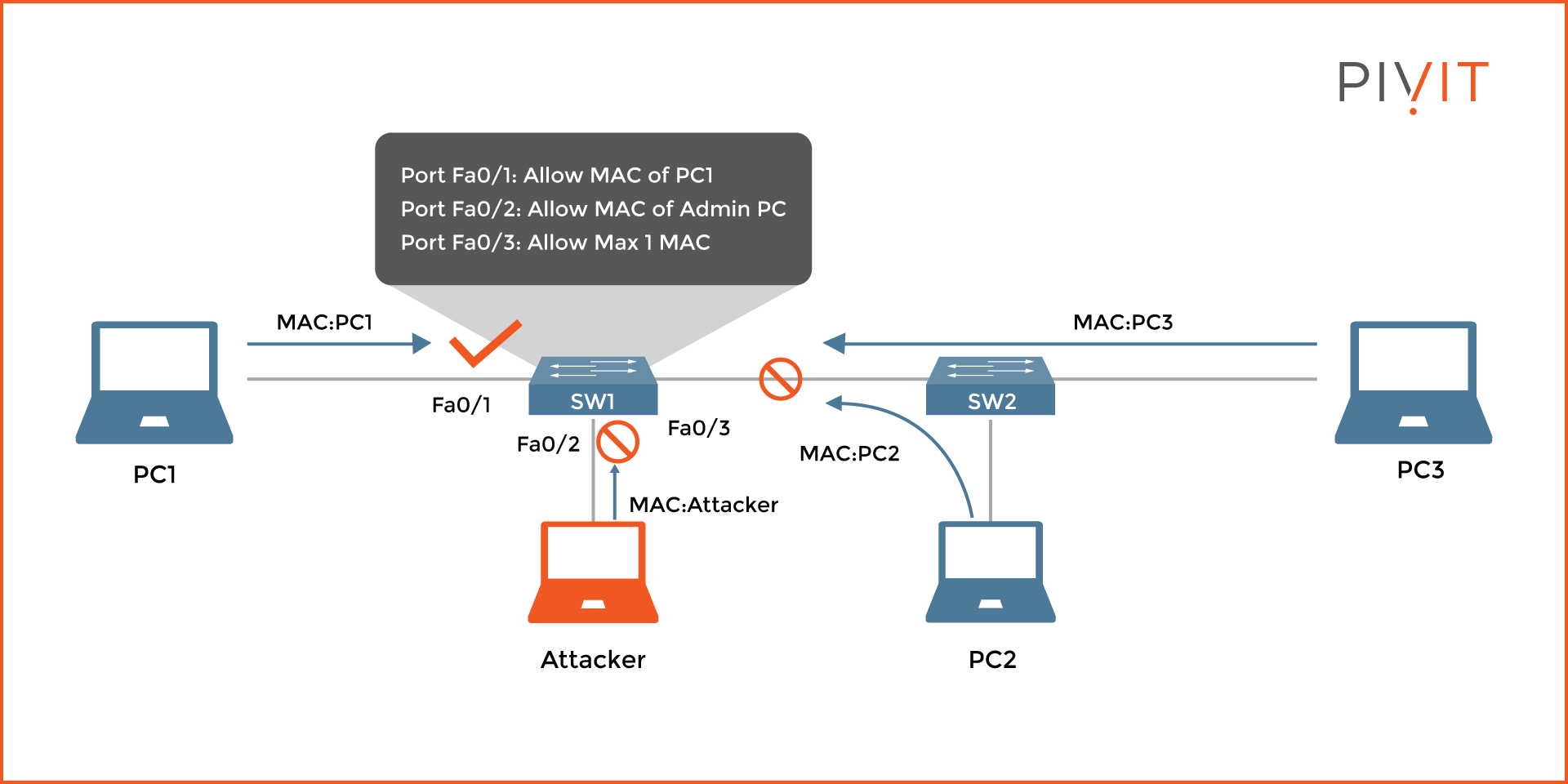
As you can see in the image above, port security is enabled on each interface on switch SW1. However, an attacker's PC has been added to interface FastEthernet0/2 instead of an allowed Admin PC. Traffic on interface FastEthernet0/1 is allowed because the MAC address of PC1 is permitted, while everything else is denied on the other two interfaces.
The reason is that the MAC address of the Attacker is not recognized on interface FastEthernet0/2, where only a MAC address of an Admin PC was allowed. Additionally, the number of MAC addresses connected on interface FastEthernet0/3 is higher than the maximum allowance of one, which causes the port to go down.
Security Violations
Each time there is a violation, the switch does not accept the receiving frames. A security violation can happen in several situations, such as:
- When the receiving frame contains a source MAC address that is different than the allowed one on that interface.
- When the receiving frame contains a source MAC address that is different from the allowed one on that interface, and the maximum number of allowed MAC addresses on that interface is already reached.
- When the total number of MAC addresses connected to the port has reached the maximum limit.
- When the frame originates from a secure MAC address arrives at a different interface in the same VLAN as the interface on which the MAC address is secured.
Violation Actions
For each violation, appropriate action is taken on the interface where the port security feature is enabled. Based on the configured violation mode, one of the three available actions can be defined:
- Shutdown: This is the default action. Once the port is logically disabled and the offending frame is dropped, it can be manually or automatically enabled using the error-disabled recovery functionality. The action increments the violation count number and allows sending SMTP or Syslog messages.
- Restrict: This is a less severe action, and instead of shutting down the port, it stays active but drops the offending frame. When executed, the violation count number increases, and SMTP and Syslog messages can be generated (if configured).
- Protect: This action is the simplest, and only the offending frame is dropped. There is no support for SMTP and Syslog messages, and the violation count number is not incremented. In most cases, it is recommended to avoid this action and use the "Shutdown" or "Restrict" action instead for maximum protection.
_________________
Do you have older switches that are coming up on their end-of-sale date? Roll those right onto our OneCall maintenance strategy, where you get dedicated spares so you can protect your critical infrastructure.
Port Security Configuration Example
The image below shows an example topology, which will be used to illustrate the configuration of port security on a switch.
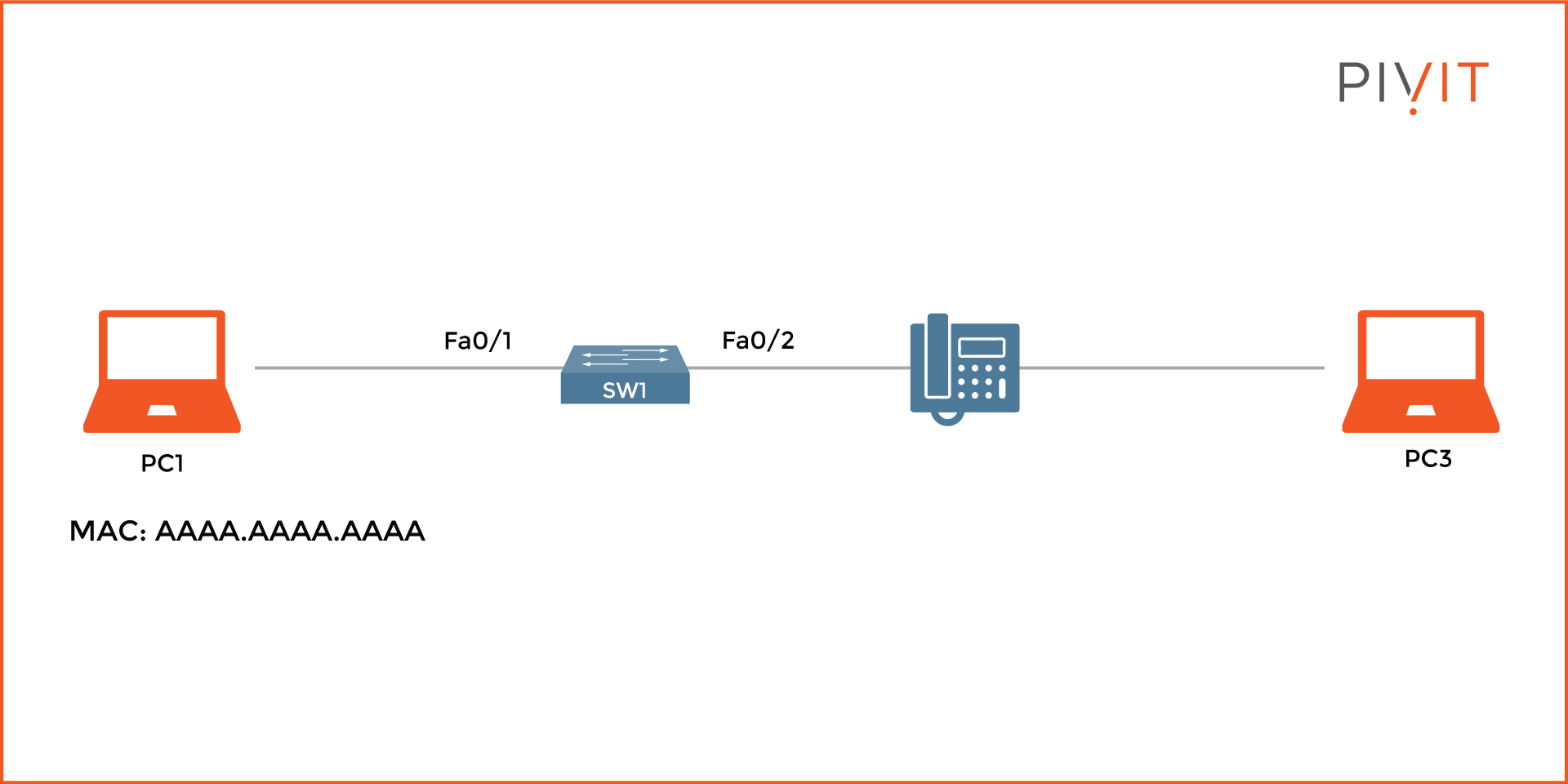
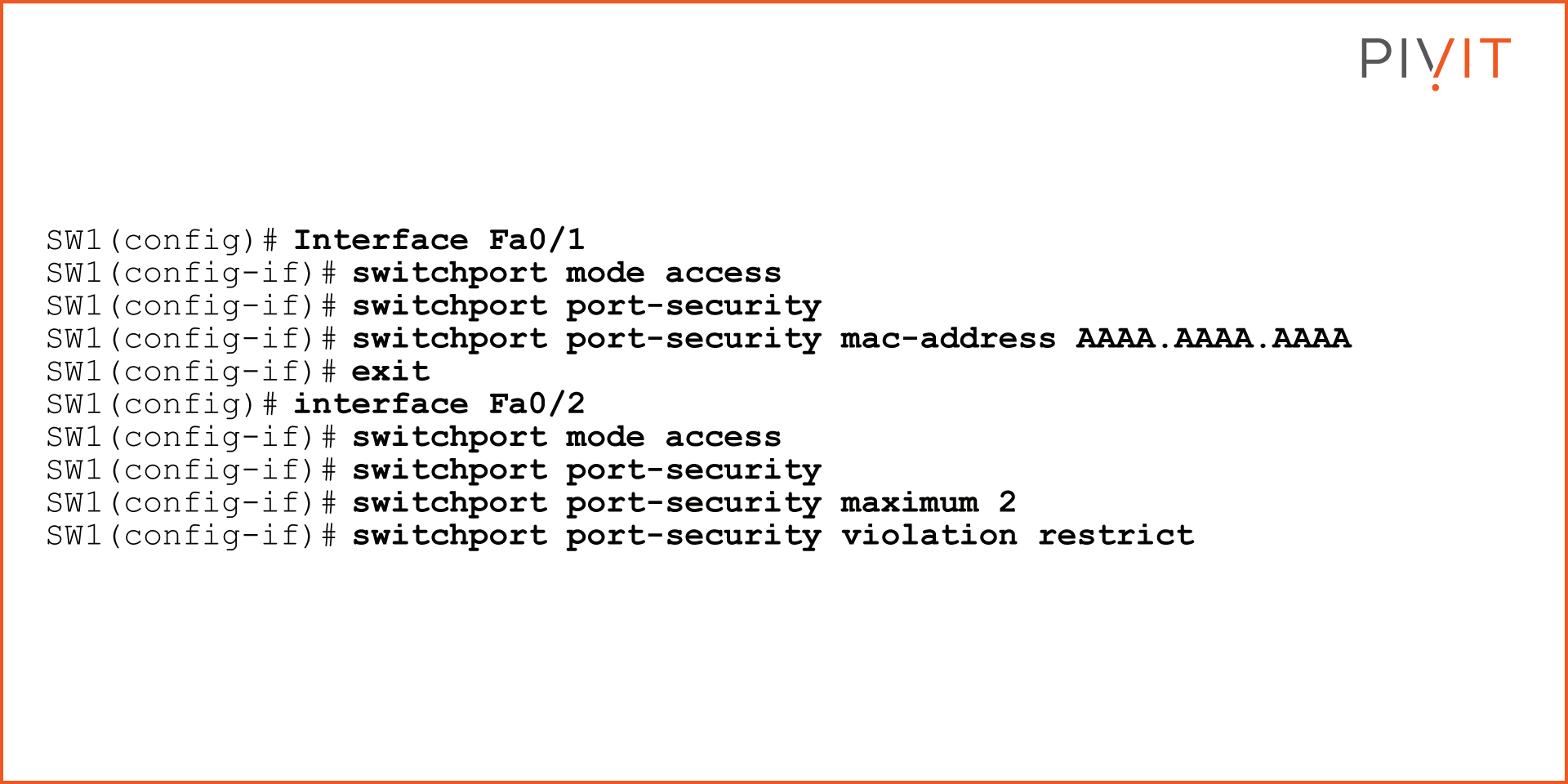
The goal is to enable port security on both interfaces on SW1. On interface FastEthernet0/1, only the MAC address of PC1 should be allowed, and the "shutdown" action should be applied in case of a violation.
On interface FastEthernet0/2, a maximum limit of two MAC addresses should be permitted (MAC addresses of the IP phone and PC3), and the violation action of "restrict" should be applied. See the commands below to configure this setup:
To verify that the security feature is configured correctly, use the "show port-security" command for the port security-enabled interfaces. The output below is for interface FastEthernet0/1:

Get All the Help You Need With Configurations
Even though there are several other more advanced features for providing the same level of Layer 2 security, the port security feature is still one of the most commonly applied in networks today. This is mainly due to its simplicity, the benefits it provides without any unexpected behavior, and the lower costs of implementing it.
We know teams can sometimes be stretched thin and don't always have the resources or headcount to configure your gear at the speed you'd like.
PivIT's EXTEND offering can step in to augment your team and remote in to configure your gear with expert-level engineers (SmartHands | EXTEND). If you need someone on-site, we have field services ready at a moment's notice. Get your switches protected today!


