Here’s How to Benefit From Using CDP and LLDP on Cisco Devices
%20(1).png)
Documentation about an enterprise network topology provides many benefits to IT engineers. Such documentation allows you to perform hardware and software upgrades and optimal tuning. But most importantly, it allows you to troubleshoot the network when issues arise.
However, when the existing documentation is not up to date (or if there is no documentation) you might find yourself quite limited in such situations. Before you can do anything else, you may have to learn the network topology first.
That’s not optimal if you’re in a situation where you need to troubleshoot network issues, especially considering the average cost of network downtime for businesses is $5,600 per minute, according to data calculated by Gartner in 2014.
The learning process of the network topology is not easy and can be done manually or automatically. While the manual approach works well in small networks, it is a cumbersome process in large enterprises.
Therefore, you need to use a dynamic discovery protocol to automatically discover the network devices and build the network topology diagram.
In this article, we will provide the following:
- An overview of CDP and LLDP protocols.
- An explanation of their functionalities and benefits.
- A look at security vulnerabilities and considerations.
- A breakdown of configuration steps and verification.
Not the overview you’re looking for? View some of our popular articles:
- Learn the Packet Delivery Process (Default Gateway and ARP)
- The Complete Solutions Guide to a Redundant Switched Topology
- The Importance of Layer 3 Redundancy: Understanding HSRP
Understanding the Benefits of Cisco Discovery Protocol
Cisco Discovery Protocol (CDP) provides information about directly connected Cisco devices, regardless of their type or functionality. CDP is a Layer 2 protocol enabled by default on all Cisco devices, such as switches, routers, or firewalls.
It periodically advertises its attributes to its neighbors by using a multicast address. As a result, CDP-enabled devices learn information about their neighbors by listening to the advertisements sent.
CDP allows you to quickly confirm the existing network topology documentation or update the network diagrams accordingly based on the exchanged CDP information. As a hello-based protocol, CDP sends hello (announcement) messages every 60 seconds out of every interface by default, which are later stored by the neighbors in a table with a hold time of three minutes.
Besides exchanging information about directly connected Cisco devices, CDP also provides extra benefits. It is very useful for network troubleshooting, especially when management software tools can utilize the data exchanged to map out topological connectivity.
At the same time, CDP automates VoIP deployments. It allows the voice VLAN to automatically be assigned to Cisco IP phones, which results in less manual configuration.
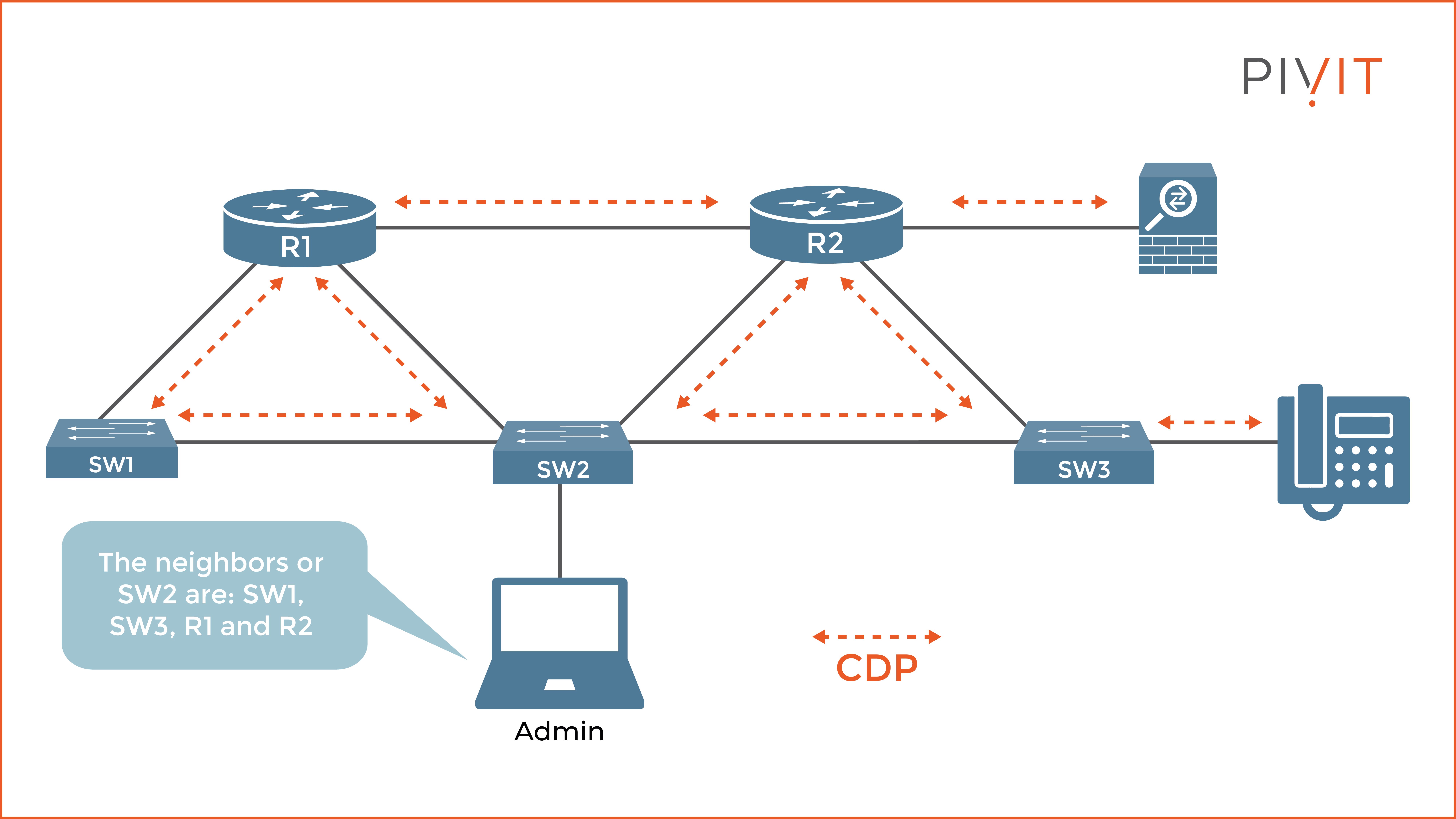
You can see in the image above how CDP exchanges information between directly connected CDP-enabled devices. The administrator is connected through the console port to SW2. Based on the CDP messages received, it knows that SW1, SW3, R1, and R2 are directly connected to SW2.
Keep in mind that CDP provides information only for directly connected Cisco devices. If you want to get information about the Cisco ASA firewall connected to R2, you first need to remotely connect (SSH or Telnet) from SW2 to R2 and learn about R2’s neighbors.
The information exchanged in the CDP messages includes:
- Device identifier: Neighbor’s hostname.
- Port identifier: Local interface and neighbor’s interface.
- Capabilities: Supported features.
- Platform: The hardware platform of the neighboring device.
- Address list: Layer 3 address (usually IP).
- Operating system: Neighbor’s operating system.
If you find this content useful, subscribe to our mailing list and comment with your feedback below. Need information or configuration instructions for a specific Cisco device? Let us know!
How to Configure CDP
CDP is enabled on each Cisco device by default, but you can disable it (or enable it) globally from global configuration mode or on a port-by-port basis (interface mode).
You can use the following commands to disable CDP globally or on a specific interface:

To view CDP information about the neighbors, you need to use the "show cdp" command. It offers multiple options, so you should use the one that best suits your requirements. The following output shows the available options:

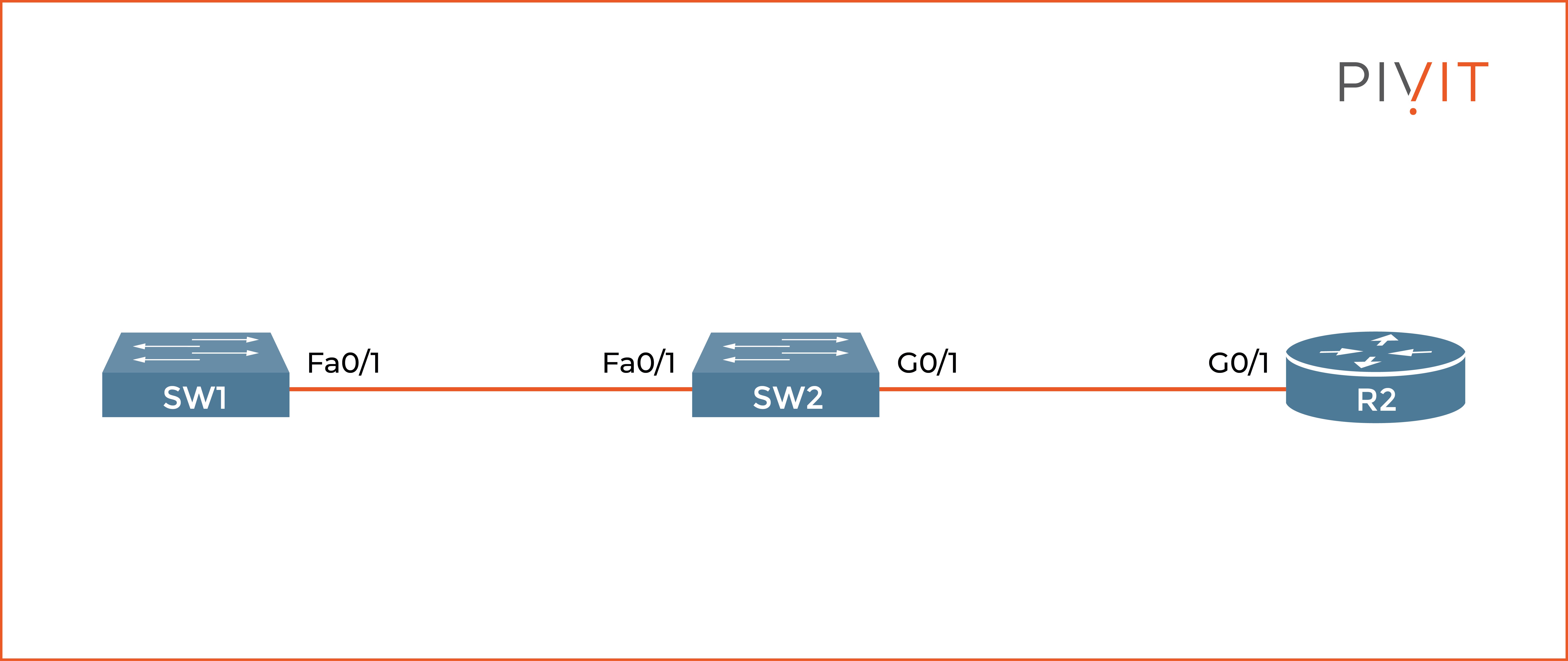
The command "show cdp neighbors" is the most commonly used because it provides basic information about the neighbors. If you need extra information, such as the IP address of the neighbor or the operating system used, you can add the “detail” argument at the end of the command.
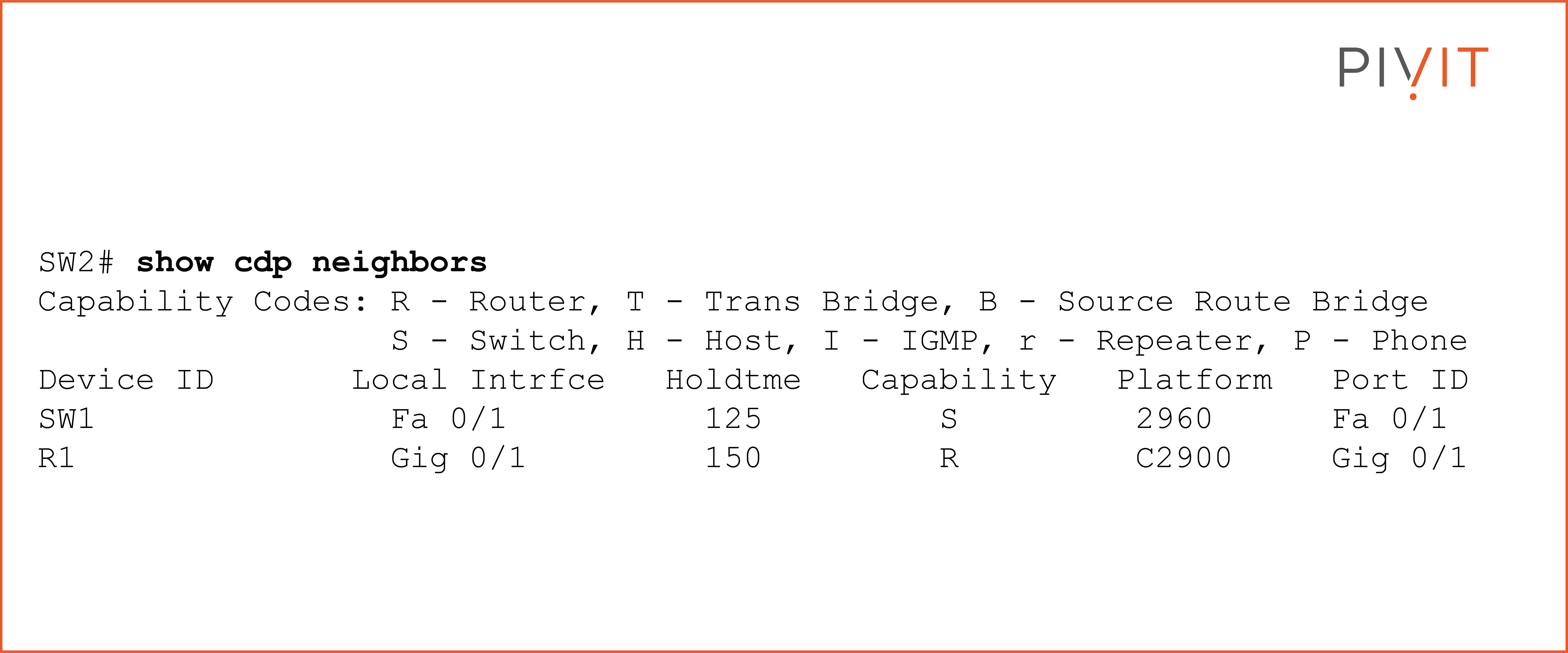
Based on the output above, you can see that SW2 has two neighbors, SW1 and R1. It uses FastEthernet0/1 to reach SW1, which also uses the same interface to connect to SW2. The platform used on SW1 is 2960, and the capability of “S” identifies the devices as a switch.
The hold time parameter (“holdtme”) counts down from 180 seconds and never goes below 120 seconds if CDP messages are constant.
However, when SW2 does not get a CDP message in three minutes (three missed hello messages), it assumes the neighbor is down and discards it from the table. The same approach applies to reading the output for neighbor R1.
_________________
Gain access to engineers around the globe utilizing EXTEND | SmartHands to access your infrastructure locally without ever leaving your desk. They take on a range of responsibilities to extend your IT team, without the added overhead of hiring a full-time engineer.
_________________
Implementing Link Layer Discovery Protocol
Because CDP is a Cisco proprietary protocol, you cannot use it for discovering non-Cisco devices. Therefore, you must use the Link Layer Discovery Protocol (LLDP) when you have a mixed network environment.
It is a standard protocol, and just like the CDP protocol, it runs over the data link layer (Layer 2) and offers the same capabilities.
LLDP is disabled by default on Cisco devices, but you can enable it when required to share information with non-Cisco devices. Because LLDP is a newer protocol than CDP, it provides more information.
This is achieved using a set of attributes containing type, length, and value (TLV) descriptions. Some of the TLVs advertised by LLDP are the system name, system capabilities, and management address.
However, using LLDP is a little different than using CDP on Cisco devices. You cannot enable or disable it on any interface until the protocol is globally enabled. Moreover, it is only supported on physical interfaces and can discover up to one device per port.
How to Configure LLDP
Configuring LLDP is very similar to configuring CDP.
First, you must enable it globally using the "lldp run" command. After that, you can enable or disable it on an interface in the inbound (receive) or outbound (transmit) direction using the "lldp receive" and "lldp transmit" commands.
The "show lldp neighbors" command is very similar to the "show cdp neighbor" command and provides the same output.
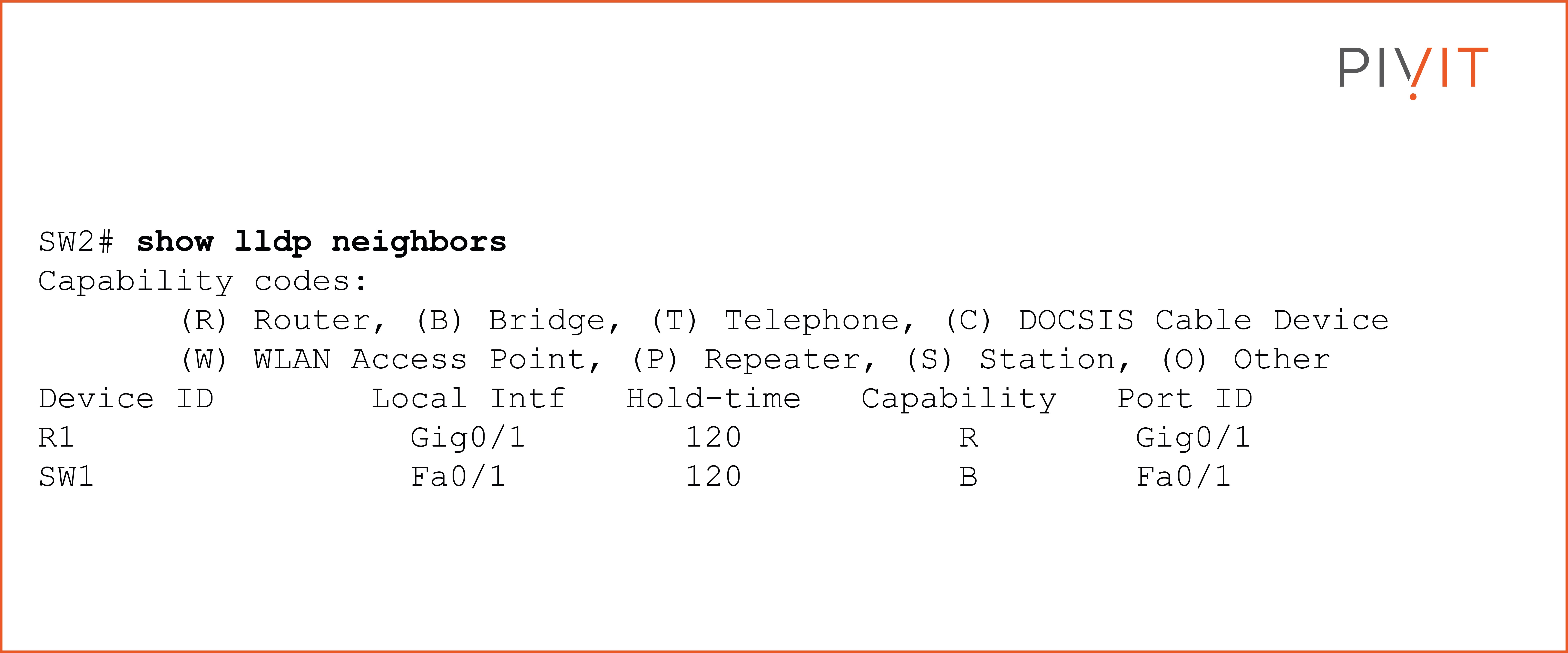
As you can see in the output above, the provided information is similar to the one from the CDP’s output. Keep in mind that the LLDP hold time is 120 seconds by default, and the packets are sent every 30 seconds.
If needed, you can always change these settings, just like with CDP.
Be Aware of Vulnerabilities of Discovery Protocols
Although discovery protocols are extremely useful, you should also be aware of their vulnerabilities. The information that they exchange is transmitted in clear text and is unauthenticated.
As a result, an attacker can easily utilize the exchanged advertisements and collect information about the network devices simply by using a packet sniffer such as Wireshark. Once the model number and the operating system version are known, the attacker can start exploiting the vulnerabilities of the devices based on the published vulnerabilities associated with learned information.
In VoIP deployments, attackers can also spoof CDP advertisements pretending to be an IP phone. This would allow the attacker to access the voice VLAN and obtain the highest possible privileges to send data into the network.
Therefore, it is essential to understand on which devices and on which interfaces you need the CDP and LLDP protocols running.
Once you establish that, you should disable these protocols where they are not needed, especially on interfaces connecting to partner devices or ISP routers.
The Double-Edged Sword Protocols
Although the discovery protocols, with their capabilities and features, provide many benefits, they can also make your network vulnerable to attacks when you do not correctly approach them.
Therefore, you should always decide whether the convenience and network discovery automation that CDP and LLDP bring to your network deployment is greater than the security risk that comes with their implementation.
The best way to protect against CDP and LLDP unintentionally sharing sensitive information with attackers is by ensuring that these discovery protocols are running only on the network devices and interfaces where they are supposed to.
Keeping that in mind, there’s no denying that CDP and LLDP provide material benefits when it comes to efficiently building your network topology diagram — and with this guide in your back pocket, you’ll be ready to start configuring when the need arises.
Send us a request or connect with our Team in real-time using our chat feature. Know what you want but need help configuring your network setup?

