Back to the Basics: Cisco ASA Firewall Configuration Guide
.png)
It's always good to get a refresher once in a while! Especially when Cisco has developed their line-up of next-generation firewalls.
Cisco's most recent improvements to their next-generation firewall family are the ASA 5506-X, 5508-X, 5516-X, and 5585-X with FirePOWER modules. The new "X" product offering consolidates businesses while driving Next-Generation Intrusion Prevention System (NGIPS) innovations. Additionally, this brings Application Visibility and Control (AVC), Advanced Malware Protection (AMP), and URL Filtering to your network.
Today, in the Cisco ASA 5506-X model, we will cover the ASA firewall configuration step-by-step, for your typical business organization.

The following illustration is the system topology that the Cisco ASA 5506-X model depends on. We will cover how to design a fundamental ACL (Access Control List), Network Address Translation (NAT), and a basic demilitarized (DMZ) arrangement facilitating a WWW server. The gear utilized in this configuration is the Cisco ASA 5506-X with FirePOWER module, running code 9.5(2).
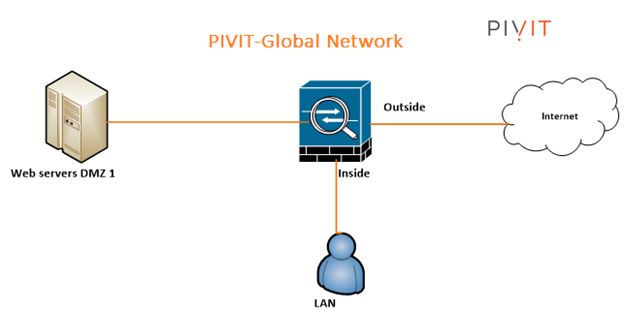
Putting it To Practice: ASA 5506-X Configuration
Network Requirements
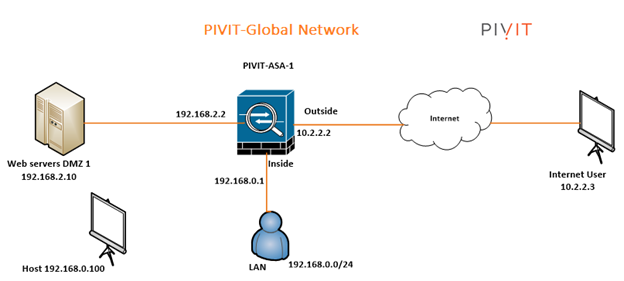
In a run-of-the-mill business condition, the system involves three sections, namely, – Internet, client LAN or alternatively, a DMZ Network. The DMZ Network is utilized to have publicly open servers, for example, a web server, an Email server, etc. The Cisco ASA goes about as a Firewall, just as an Internet passage.
Here are a few additional points to note:
- LAN users and Web Servers all have Internet access.
- LAN users have full access to the Web Server network segment DMZ 1 but DMZ 1 does not have any access to the LAN.
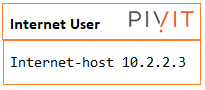
- Anyone on the Internet can access the Web Server via a public NAT IP address over HTTP(S).
- All other traffic is denied unless explicitly allowed.
Updating ASA Software and ASDM Code
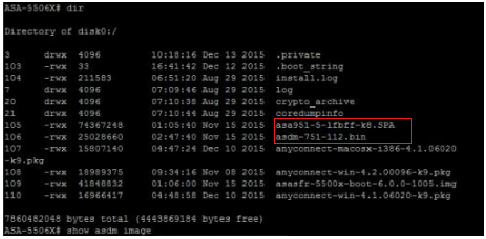
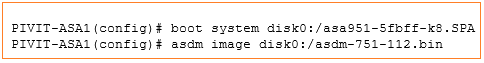
Set the system to boot to the new image and configure the ASDM image to be used.
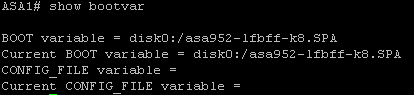
Write to memory and verify the bootvar is set correctly. Reboot the system to load the new image.
Security Levels on Cisco ASA Firewall
Prior to the setup, addressing how Cisco ASAs work in a staggered security structure is key as the model is designed to help you handle network traffic in a way that complies with your organization's security policy. Fully understanding the security structure helps you see the end goal and gain each benefit with the ASA Firewall.
As a matter of course, traffic going from a lower to higher security level is denied. This can be superseded by an ACL applied to that lower security interface. Likewise, the ASA will permit traffic from a higher security level moving down security interfaces. This conduct can be abrogated with an ACL. The security levels are characterized by numbers in the range of 0 and 100. The untrusted systems, the Internet for example, is characterized with a 0. The most secure systems are characterized with a 100. In our model we placed security levels as follow: LAN = 100, DMZ1 = 50 and outside = 0.
LAN is considered the most secured network. It not only hosts internal user workstations, but also mission-critical production servers. LAN users can reach other networks. However, no inbound access is allowed from any other networks unless explicitly allowed.
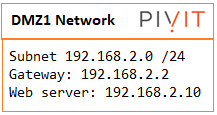
As a quick example, the DMZ1 hosts public-facing web servers. Anyone on the Internet can reach the servers on TCP port 80 for HTTP. The design idea here is that we don’t allow any possibilities of compromising the LAN. All “inbound” access to the LAN is denied unless the connection is initiated from the inside hosts. Servers in DMZ1 serve Internet web traffic and internal user traffic from the LAN.
PivIT Global Network Design and IP Assignment
The last piece, before we dive into the configuration, is the specific design we've used on a PivIT Global Network with the IP Assignment. For simplicity, we assume the SOHO network has less than 200 users and does not have a layer switch on the LAN. All user and server traffic point to the ASA as their default gateway to the Internet. We assign each network segment a /24 (255.255.255.0) subnet mask.

Cisco ASA 5506-X Configuration
The 7-step process guides you through the configuration with a PivIT Network as an example. As you've seen from above, there is explanatory text, diagrams, and procedures in each step to help you navigate the user interface, maximize the performance, and troubleshoot complications. Reach out to PivIT with any questions or more information on the Cisco ASA 5506-X configuration!
About PivIT Global
Leave a comment, question, or concern below. We created the Tech Corner to connect with you on configuration guides product discussions, product comparisons, and provide you with information about the industry. Subscribe to the Tech Corner today!
