RADIUS vs. TACACS+: Which AAA Protocol Should You Choose?

Authenticating users before providing them with access to network resources is nothing new.
Providing access to the wrong individual can be fatal for businesses: worldwide cybercrime has cost businesses $5.2 trillion within five years.
So it’s a standard security recommendation for organizations to authenticate the employees and get corresponding authorization based on their account privileges.
In the end, generated logs get stored for evidence of each action they perform, which can also come in handy in troubleshooting scenarios.
The best method to achieve such goals is by using AAA. Because local AAA does not scale well in large and complex enterprise networks, centralized AAA is the preferred option. The AAA protocols that you can use are RADIUS and TACACS+. Based on your requirements, you can use either one or both simultaneously.
Download the guide and refer back to it at any time!
This article will provide the following:
- An overview of the AAA framework.
- An understanding of the capabilities and functionalities of the RADIUS and TACACS+ protocols.
- A comparison between RADIUS and TACACS+.
Not the information you’re looking for today? View some of our popular articles:
- The Essentials of ARP Protocol & How To Protect Against Spoofing Attacks
- Must-Have Port Security: Simple but Efficient Layer 2 Protection
- The Ultimate Guide to DHCP Spoofing and Starvation Attacks
Understanding AAA Framework
AAA is an architectural framework that provides a simple way to enforce network access control policy on network devices. AAA stands for authentication, authorization, and accounting, and each service is responsible for performing different actions.
The questions that AAA tries to answer for each user or device are:
- Authentication: Who are you?
- Authorization: What are you allowed to do?
- Accounting: What did you do?
Authentication is all about determining the users’ identities. Authorization is about defining the privileges they get after successful authentication, and accounting keeps track of what those individual users have done before.
Local AAA is the preferred solution in small networks, such as branch offices, where the number of users is small and changes rarely happen. However, there are better approaches than using the local database of the devices for AAA services for large enterprises with hundreds or even thousands of users.
In such a case, centralized AAA is the better option, provides flexibility, and allows you to continue using the existing user ID repository, such as an Active Directory, when there is one.
Using AAA provides many benefits, including scalability, redundancy, increased flexibility, support for standardized and proprietary authentication methods, and granular control of access configuration.
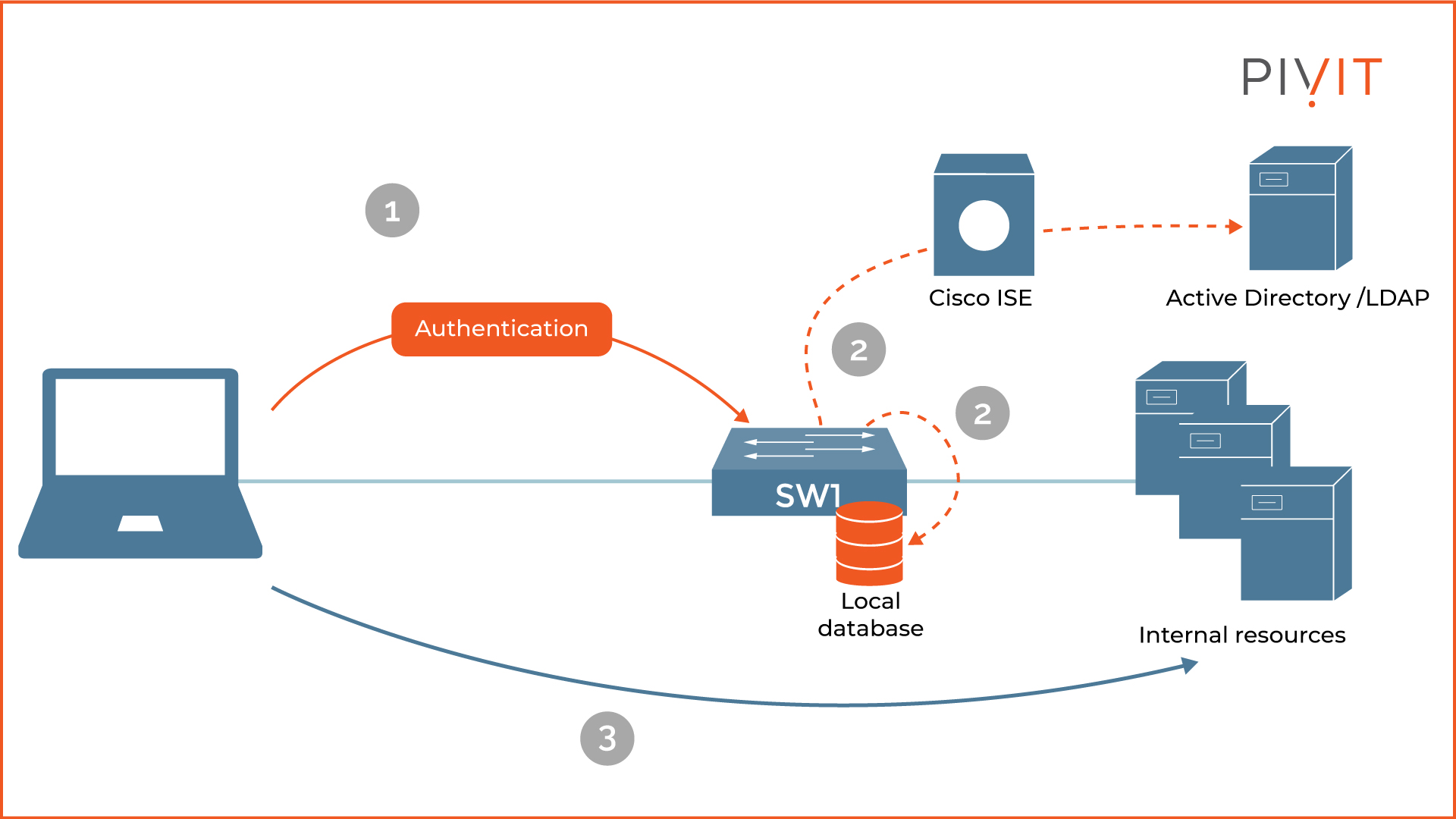
As you can see in the image above, the AAA process is straightforward to understand.
During the authentication process, the user must identify themselves, and their provided credentials get checked against the local database of the switch or an external AAA server, such as Cisco ISE.
Optionally, Cisco ISE can forward those to Active Directory or LDAP server. After successful authentication, the user is accordingly authorized based on a configured policy, and every action performed is logged afterward.
_________________
Get help choosing the best switch for your network by speaking with our specialists.
_________________
Understanding the AAA Protocols
When using centralized AAA, network devices such as switches, routers, firewalls, or access points, also known as network access servers (NASs), must use a protocol to exchange AAA data with external servers.
The two most popular AAA protocols for external AAA services commonly implemented in today’s networks are RADIUS and TACACS+, and both use a client-server model.
The client-server model represents a simple communication process between the NAS and a server. After a user or machine sends a request to the NAS, it is forwarded to the external AAA server for verification through RADIUS or TACACS+. Access to protected resources or device CLI is granted to the user if authentication is successful.
AAA has two main roles in networking — providing network access and device administration.
In the case of providing network access, the user or device is allowed to access the protected resources, such as email or web server, only after successful authentication. Device administration means providing the user access to the device’s CLI through the console port or remotely by Telnet and SSH after successful authentication.
The main difference between the two roles is that network access is static, meaning after privileges are granted (authorized after successful authentication), nothing changes afterward.
On the other hand, device administration is dynamic and verifies each request by the user. It allows actions (such as configuring commands through the CLI) only if they are explicitly allowed or authorized by the external AAA server.
An Overview of RADIUS
RADIUS stands for Remote Authentication Dial-In User Service and is a fully open standard protocol that relies on the UDP protocol for providing AAA services.
Over the years, RADIUS has become the de facto standard for network access. Its flexible framework enables vendors to define their Vendor Specific Attributes (VSAs) according to their needs and not rely only on the standard dictionaries.
Because the RADIUS protocol combines authentication and authorization in a single service, it listens on UDP port 1812 for authentication and authorization data. For accounting services, it listens on UDP port 1813.
Besides encrypting the password portion of the RADIUS packet header, it does not provide any other level of protection, so the rest of the data sent between the NAS and RADIUS server is unsecured.
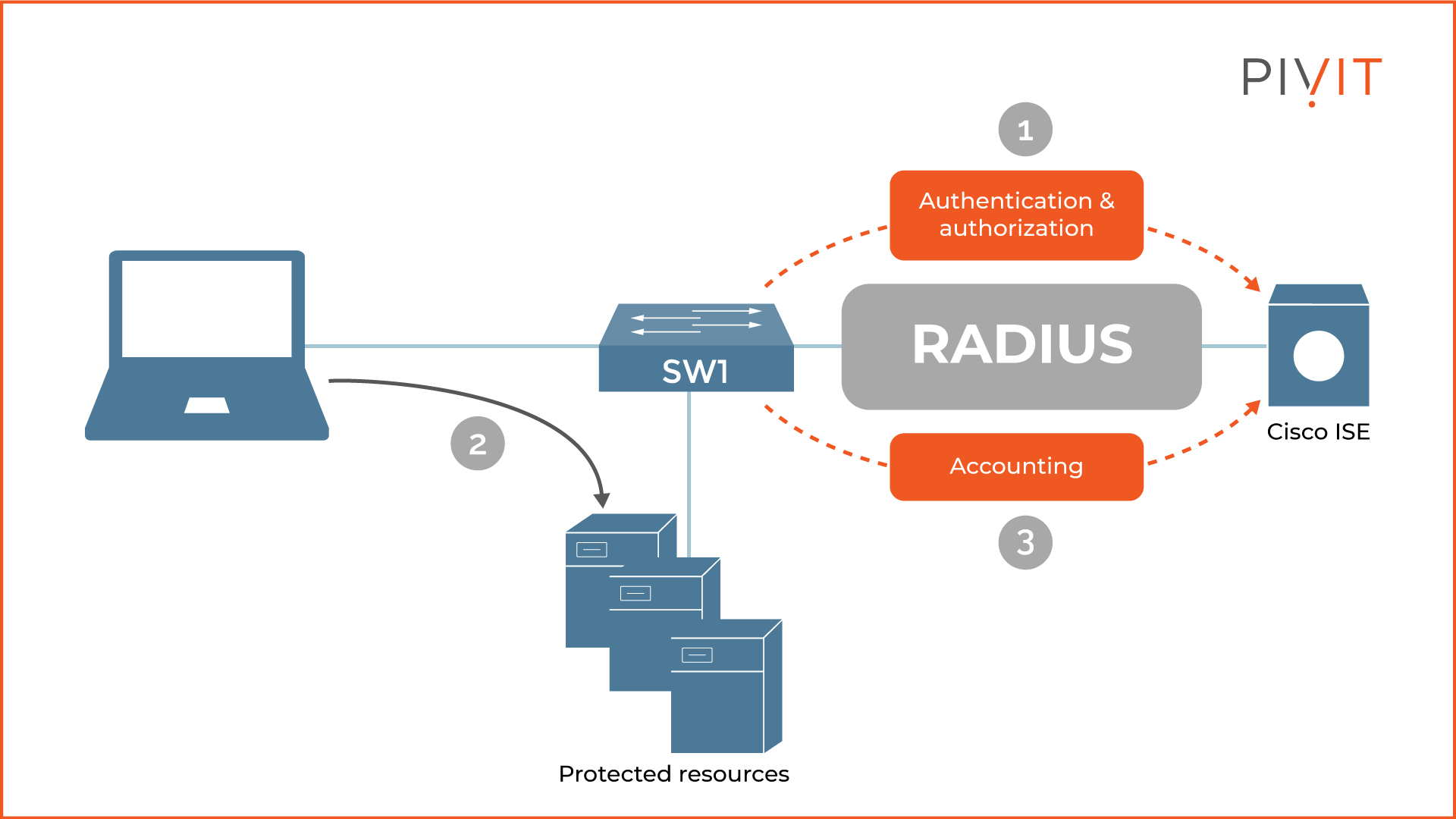
As you can see in the image above, the RADIUS’s structure contains three components: the NAS, the server, and the database (or, in our case, the switch) and Cisco ISE with its database.
After the user sends the credentials, the NAS (switch) forwards them as a RADIUS Request message to the RADIUS server (Cisco ISE). Then, the RADIUS server replies with one of the three possible responses:
- Access-Accept: Representing successful authentication, after which the authorization service takes place.
- Access-Reject: Unsuccessful authentication. The user’s access gets denied.
- Access-Challenge: The server requests additional data from the user, such as a secondary password, PIN, or token card.
In the end, the accounting service keeps a log of each user's action.
Cisco Identities Services Engine (ISE) is not just a RADIUS server from Cisco but a policy management and control platform for wired, wireless, and VPN connections that provides end users and devices secure network access.
_________________
Don't let unreasonable lead times stop you from getting the switches you need. PivIT gives you the freedom to choose from an extensive network of OEM partnerships, maximize your budget, and create a strategy to keep your network scalable.
_________________
An Overview of TACACS+
TACACS+ is a Cisco proprietary protocol with similar capabilities to the RADIUS protocol but uses a bit of a different approach and is more secure. In contrast to the RADIUS protocol, TACACS+ separates authentication and authorization functionalities into other services instead of combining them.
Because TACACS+ uses the TCP protocol and listens on port 49, the transport protocol ensures reliability. One of the advantages of using TACACS+ is the support to encrypt the entire TACACS+ packet, which provides secure communication between NAS and the TACACS+ server.
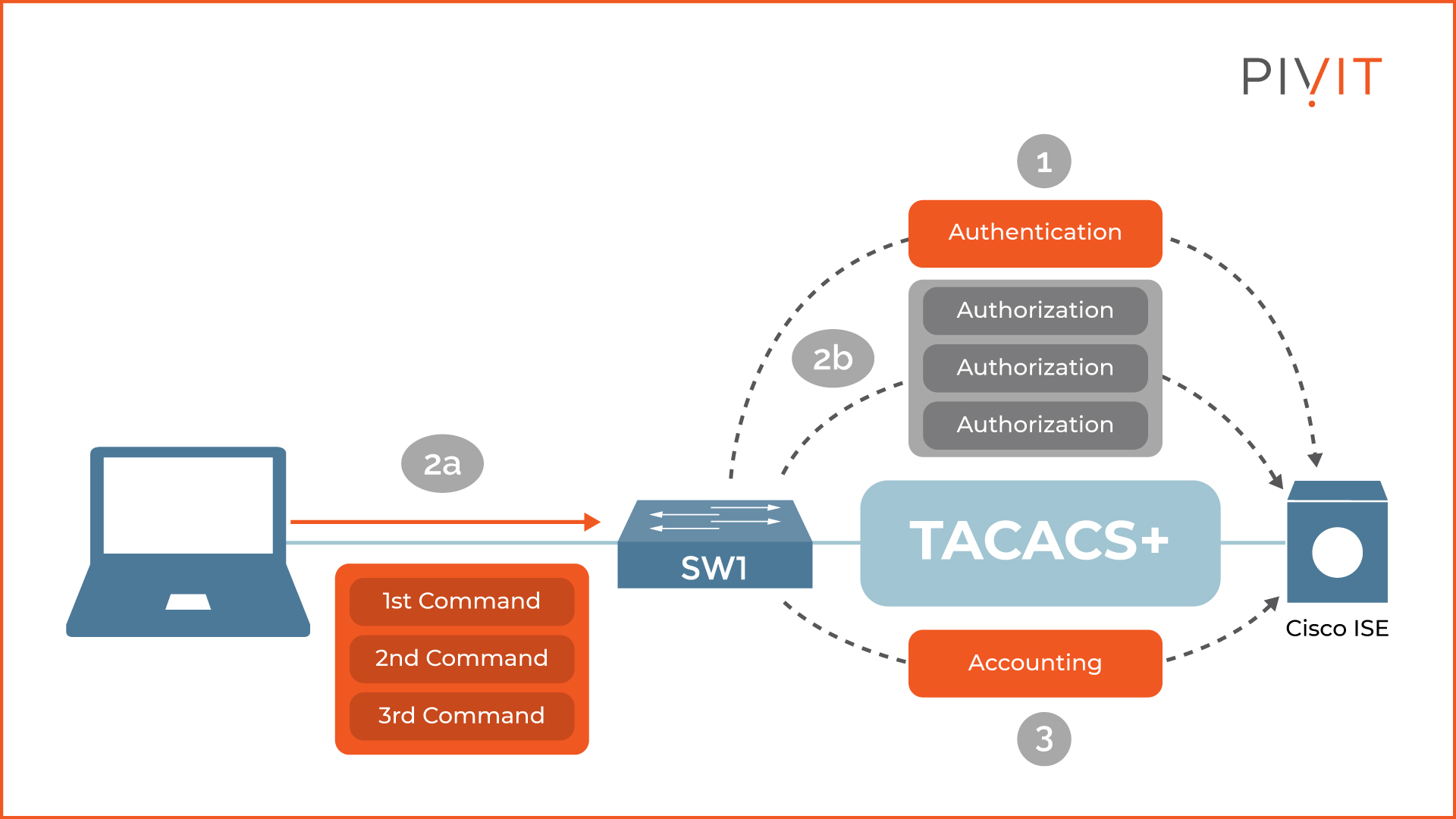
As you can see in the image above, the TACACS+ communication between the NAS (switch) and the TACACS+ server (Cisco ISE) starts after they establish a TCP connection. Then, the switch sends the user credentials to Cisco ISE. If the credentials are valid, Cisco ISE replies with an Accept message and otherwise with a Reject message.
Afterward, for each user request (that is, each configuration command that the user tries to enter), Cisco ISE checks the locally configured policy and replies with an Accept or Reject message based on the result. In the end, the accounting service keeps a log of each action (configuration command) performed by the user.
TACACS+ is best suited for administrative access, such as accessing and configuring a network device. After the administrator accesses a network device via HTTPS, SSH or Telnet, the user credentials are forwarded to the AAA server using the TACACS+ protocol. After successful authentication, each user's command must be authorized against the set of allowed commands.
Cisco ISE can be used as a TACACS+ server. It will enable you to define a set of commands that only selected users can apply on the network device.
A Comparison of RADIUS vs. TACACS+
Comparing the RADIUS and TACACS+ protocols is like comparing apples to oranges. Though they are both fruits, they taste different, grow differently, and have distinctive physical characteristics.
The same applies to the AAA protocols.
Although their purpose is to provide AAA functionality, they operate differently and are best suited for different AAA roles.
The following table summarizes the differences between the RADIUS and TACACS+ protocols.
| Feature |
RADIUS |
TACACS+ |
|
Developed |
Industry-standard |
Cisco proprietary |
|
Primary use |
Network access |
Device administration |
|
AAA support |
Combines authentication and authorization in a single process and separates accounting |
Separates authentication, authorization, and accounting |
|
Protocol and ports |
UDP ports 1812 and 1813 |
TCP port 49 |
|
Security |
Encrypts the password only |
Encrypts the entire packet |
And the Better AAA Protocol for Your Network Is?
Well, both. It’s as simple as that.
Each of these two protocols is beneficial and is a perfect option for achieving different AAA goals. RADIUS is the obvious choice for network access services, while TACACS+ is the better option for device administration.
Therefore, you can implement one or another (or both of them simultaneously) when requirements demand. Use this guide to determine your needs and which AAA protocol can benefit you the most.


