Cisco ASA Firewall Active/Standby Configuration Guide (Part 1 – Overview)
-1.png)
A firewall is a primary device that is used to provide security features in a network, although other complimentary devices such as an Intrusion Prevention System (IPS), Cisco Email Security Appliance (ESA), Cisco Web Security Appliance (WSA), and Cisco Identity Services Engine (ISE) could also be used.
Ready to learn how to deploy this configuration? Jump to Part 2 here.
Even though most of the firewalls in production networks are Next-Generation (i.e., Cisco Firepower Next-Generation Firewall) because of the new features they support, using an older Cisco Adaptive Security Appliance (ASA) firewall will most definitely do its primary goal, which is providing the NAT services, creating communication sessions, and supporting routing capabilities.
Looking to compare firewalls?
Read the comparison blog of the Cisco ASA vs Fortinet Fortigate firewalls here
Because of the importance of the firewall and the dependence of the whole network on it, using a backup firewall is critical for uninterrupted network connectivity. Common concerns such as hardware issues, link/cable problems, or misconfiguration can all result in a non-operational network. Therefore, implementing a backup solution is the only way to ensure your network is always active and functional.
Want to learn more about backup best practices? Click here.
In this article, we will take a brief look at the benefits of the high-availability features that can be used on the Cisco ASA and focus on the Active/Standby failover, which is the most implemented deployment in networks today.

Looking for a firewall device? See our full overview of the Cisco ASA 5500 Series firewall or get in touch with us to find the perfect match for your network.
Need to quote a firewall?
Support for Several High-Availability Features
The Cisco ASA firewall supports several high-availability features that provide an interface, device-level redundancy, and (depending on the requirements and network deployment) one or the other will be the best fit:
- EtherChannel – A port link aggregation technology where a logical interface consisting of several grouped physical interfaces provides fault tolerance, load balancing, redundancy, and increased bandwidth.
- Redundant Interface – A pair of two physical interfaces (one active and one standby) operating as a backup for each other to provide interface-level redundancy.
- ASA Cluster – A feature that groups multiple Cisco ASA firewalls to operate a single logical firewall to achieve increased throughput and redundancy through all units.
- Two Failover Modes
- Active/Standby Failover: A pair of two Cisco ASAs in which one unit is active and forwards traffic while the other one is in a hot standby state and takes over when the primary unit fails.
- Active/Active Failover: A pair of two Cisco ASAs in which both units operate at the same time to provide load sharing and increased overall performance. When one of the units fails, the other one takes over and processes all network traffic.
Cisco ASA Active/Standby Failover Overview
A redundant device is needed to achieve uninterrupted network connectivity. The Active/Standby high-availability failover feature allows you to pair two security Cisco ASAs together, where one unit is active and forwards all traffic while at the same time the other one is in a hot standby state. See an example of an Active/Standby topology below.
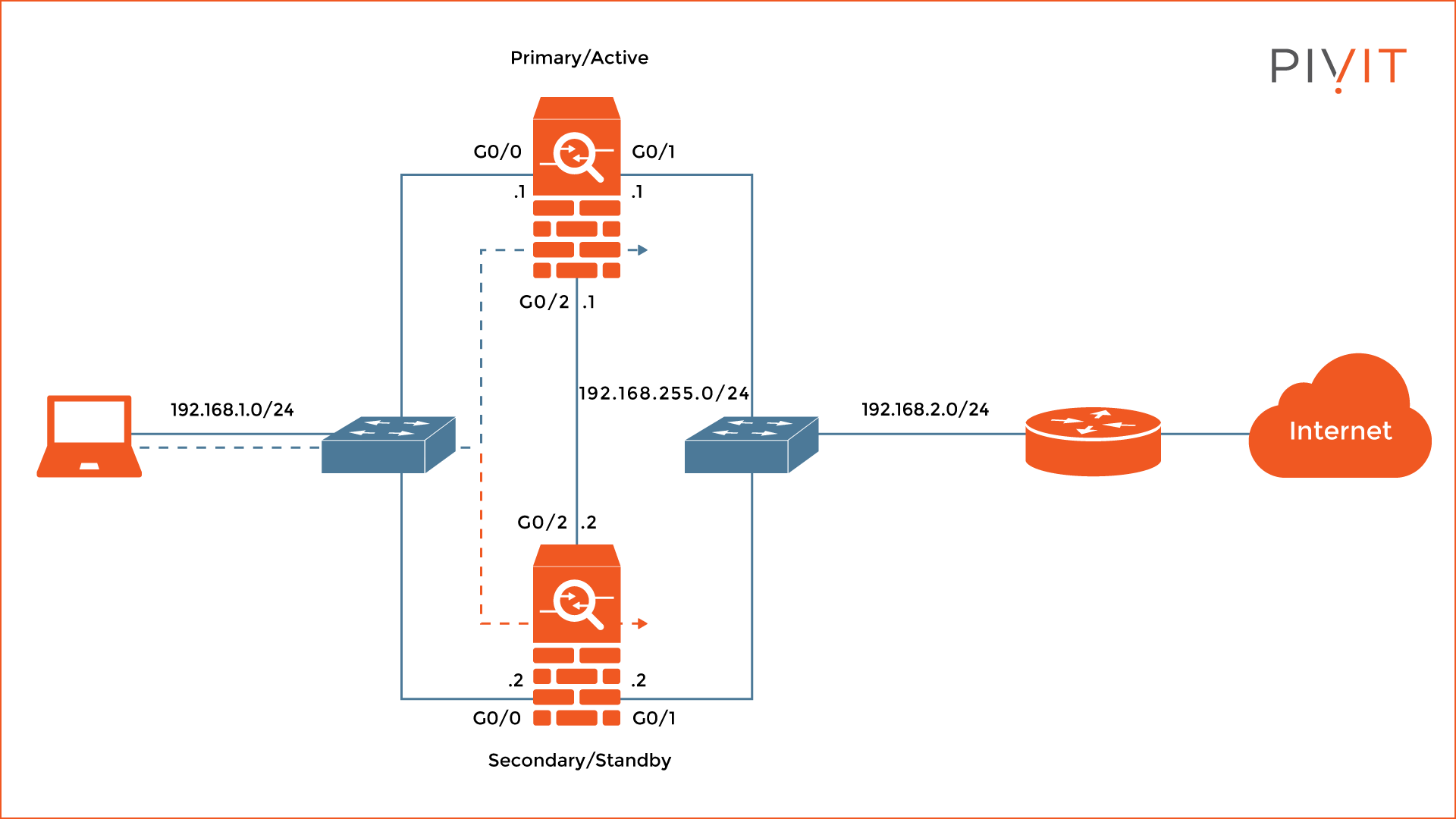
When the active unit fails the standby unit takes over the active role and continues forwarding the traffic. Therefore, if the Active/Standby failover feature is deployed and configured correctly on both firewalls, users will never experience any network connectivity issues during the switchover process of the ASAs.
In the Active/Standby configuration, there are two roles, primary and secondary, and they never change. One of the ASA firewalls is permanently designated as a primary unit, while the other one is a secondary unit. The reason for that is to establish the priority of both firewalls during the election process for active and standby units.
When the election process occurs (usually during the boot up), the primary unit always takes over the active role by default, while the secondary unit goes into a standby state.
The active ASA will then start processing all traffic while the standby ASA only monitors the active appliance for potential issues. Once something goes wrong with the active unit, the standby unit takes over and becomes the new active ASA in the Active/Standby pair.
At the end of the day, when a Cisco ASA boots and there is another ASA available, the primary one becomes active and the secondary goes into standby. However, this will not always be the case. On one hand, if there is already an active ASA in the pair, the ASA goes to standby directly.
On the other hand, if the ASA does not detect any other ASA during the process of selection, it becomes active no matter the role configured on that unit. Unfortunately, if the ASA detects another ASA after this event, then both firewalls will renegotiate the failover roles.
Limitations of the Cisco ASA Active/Standby Configuration
For the Active/Standby configuration to work, two security appliances must be connected through a dedicated failover link and (optionally) a stateful failover link.
However, even though all Cisco ASAs can be configured for Active/Standby failover, a few requirements must be checked for the failover to work on both firewalls. Some of the most important are:
- Identical hardware used
- Same number and type of interfaces available
- Same software version used
- Same licenses (features) installed
- The active/standby failover feature installed
- Same operating modes used
Supported Failover Deployment Options
When implementing Active/Standby failover on Cisco ASAs, there are two types of failover configurations supported. Even though both use similar approaches, they provide different results and can be used separately or at the same time. The failover deployment options are:
- Stateless Failover: This failover approach provides hardware redundancy only and nothing more, which can be quite problematic in certain scenarios. The standby ASA monitors the active ASA for potential issues such as power, interface, or SSM failure of the device and takes over the active role.
The problem with this approach is that all previously tracked connections on the active unit are lost and each client application that was previously operational must start a new connection through the newly selected Cisco ASA, just because they are not synchronized on the ASAs.
Such information is the connection table and the corresponding local host table, among other things used by the ASAs. Stateless failover is not the recommended failover option, however, requires fewer resources for the units.
- Stateful Failover: This failover approach complements the stateless failover functionality by providing additional information on top of the hardware information already used. When using stateful failover the octave unit continuously passes state information such as connection and localhost table data to the standby unit.
When a failover occurs, all the information is already available on the newly selected active ASA and there is no need for re-establishing connections. As a result, all end-user applications will continue working without any interruption or need for a reconnect.
Stateful failover is the recommended approach especially in cases when there are a lot of active end-user applications running in the background. A dedicated stateful link is a requirement to implement this failover.
Are lead times slowing you down and preventing you from getting the firewall hardware or services you require to protect your data center? Send us a request or connect with our Team in real-time using our chat feature. Know what you want but need help configuring your setup?
Two Types of Failover Interfaces on a Cisco ASA
Once the ASAs are configured in either stateless or stateful failover, they will start communicating failover information between themselves. The information exchanged between the units identifies the roles (primary or secondary), the power status of the units, and shares connection state information for uninterrupted switchover between them.
Based on the information required, two types of failover interfaces can be configured on the Cisco ASAs, each one sharing a different type of information. The failover interfaces are:
- LAN Failover Interface: In any Active/Standby failover deployment there is a requirement for a LAN failover interface over which critical information is shared for normal operation of the failover configuration. This information is used to determine the operating status of each unit, as well as to replicate and synchronize any configuration between both units in the pair.
In order to accomplish this, a dedicated ethernet interface must be used on each Cisco ASA, which will be used exclusively for passing failover information. The connection between these interfaces on the ASAs can either be a direct link or through a switch. - Stateful Failover Interface: This type of interface is more of an optional feature. However, its usage is recommended in a failover deployment. The reason for that is quite simple. Besides the hardware information shared, additional information is needed such as state information among other things on the standby unit.
Without this data, anytime a failover happens, all end-user applications must re-establish connections and there will be an interruption from the client’s point of view. The stateful failover interface can either be a dedicated interface or shared with any other interface including the LAN failover interface.
Although sharing a stateful failover interface with a LAN failover interface is a common approach, it is not recommended to share it with a traffic-passing interface. Some of the information exchanged over the stateful failover link is:
- Network Address Translation (NAT) table
- Address Resolution Protocol (ARP) table
- TCP connection table
- UDP connection table
- HTTP connection table
- MAC address table
To conclude, once the Active/Standby deployment is finished, both ASAs will be managed as a single logical unit. All that is needed afterward is to configure the active ASA that provides the management IP address, which will automatically replicate the configuration and all the changes made to the standby unit in the pair. Consequently, from the users’ point of view, there will not be any interrupted connectivity when something goes wrong with the active ASA and a switchover happens.
Protect your firewall hardware with PivIT's OneCall service. Get coverage tailored to your networks and have complete peace of mind knowing when something happens, it will be handled right away. View our OneCall offering here.
For more information regarding the configuration of the Active/Standby failover deployment, see Part 2 of this two-part series.
