Remote Access Clientless VPN: What You Need To Know
.png)
It’s a striking prediction: Kate Lister, president of Global Workplace Analytics, estimates that by 2025, around 70 percent of the workforce will work remotely at least five days per month.
Such a figure would have huge implications for how the workplace functions. And though that date is still years away, it’s not uncommon for employees and clients to require access to your resources, no matter where they are or what they’re working on.
Despite that, the security of your resources remains paramount. So, how can you empower secure remote access, using only a browser, while still retaining a focus on security?
A clientless VPN solution could be the answer. Such an option provides browser-based access to resources located behind the VPN gateway on the other side of the protected tunnel.
Instead of using a pre-installed VPN client such as Cisco AnyConnect on the host device, this solution empowers users to access web-based applications, FTP servers, and CIFS file shares simply by using a Transport Layer Security (TLS)-enabled browser.
On top of that, by using application plug-ins, smart tunnels, and port forwarding, users can access almost any application and service that uses static TCP ports.
In this article, we will:
- Provide an overview of clientless remote access VPN technology.
- Discuss its benefits and limitations.
- Learn the basics and familiarize you with TLS protocol.
- Take a look at the clientless web portal.
- Find out more about recommended implementation steps for a clientless VPN implementation on a Cisco ASA firewall by using the ASDM management tool.
Looking for more ways to optimize security in your organization? Try these articles:
- Must-Have Port Security: Simple but Effective Layer 2 Protection
- Your Best Security System: Cisco ASA vs. Fortinet FortiGate
- A Must-Have Guide - Risk-Free: Protect Against VLAN and STP Attacks
An Overview of Clientless VPN
Cisco clientless TLS VPNs allow organizations to provide secure remote access to protected network resources in the headquarters, even when the remote user device is not managed or has no VPN client installed. In other words, it provides the simplest way for users to access mainly web-based (and some non-web-based) applications over a web browser.
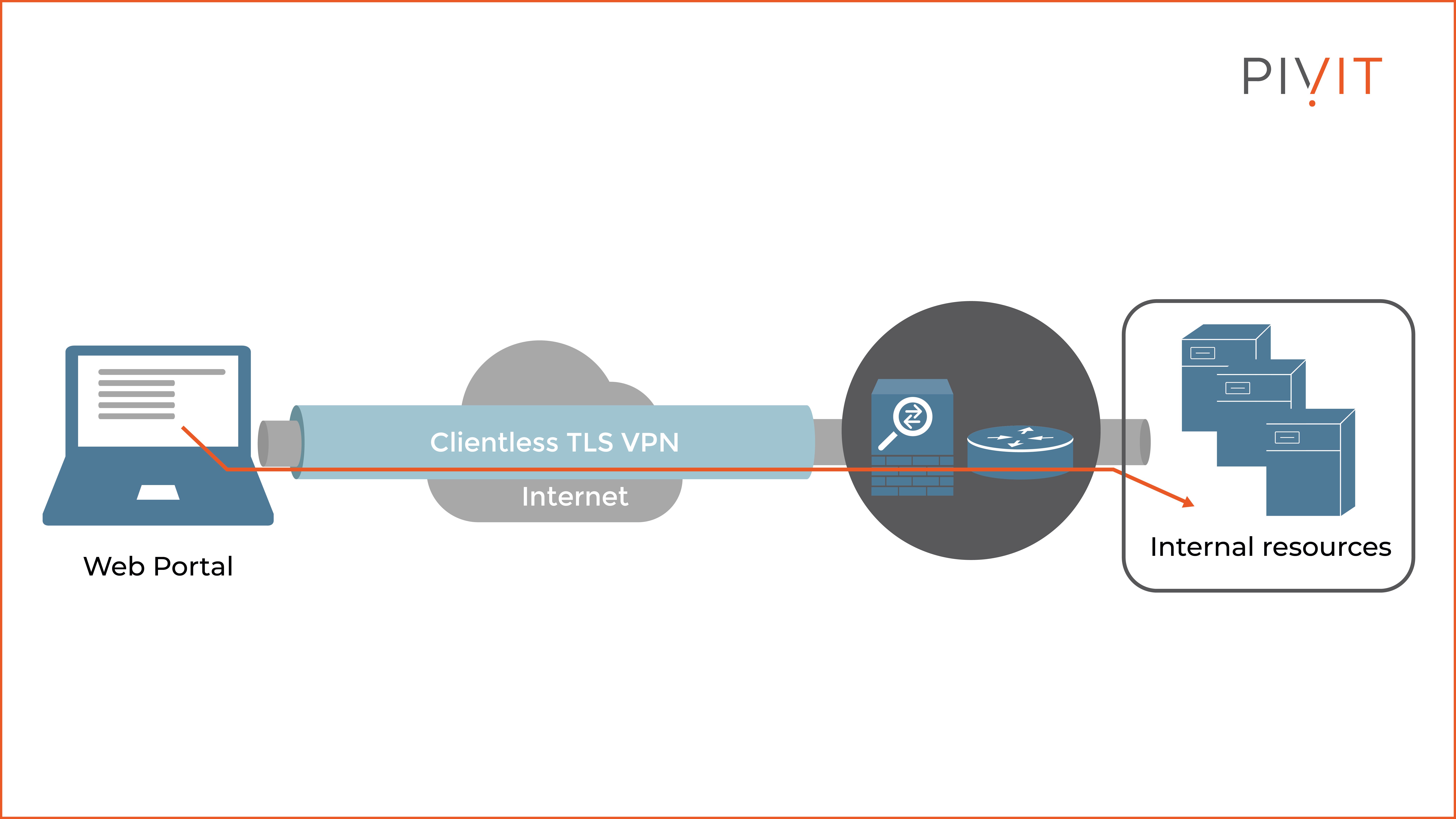
The way it works is quite simple. Remote users use only a web browser to establish a TLS VPN connection (tunnel) with the VPN gateway — which usually is a Cisco ASA firewall, but can also be a Cisco router. The VPN gateway that acts as a proxy between the remote user and protected resources is responsible for the overall VPN permissions, such as services allowed, bookmarks available, et cetera.
Keep in mind that the Cisco Firepower NGFW firewall doesn’t support clientless VPN deployment at the time of writing. After successful bidirectional authentication, the VPN gateway presents the user with a web portal through which they can access only those services for which permissions are provided.
Even though the clientless VPN solution is easier to deploy, it provides only limited access, which is the opposite of the full access supported by the Cisco AnyConnect VPN solution. Therefore, whether to use a clientless VPN primarily depends on the type of users that need to access the protected resources behind the VPN gateway.
Typical use cases include internet kiosks and business partners that require access only to a specific set of services and resources in general, which works perfectly with the clientless VPN limitation. This also protects against unwanted access being provided to the wrong users.
Accessing Resources Remotely
Because clientless TLS VPNs do not provide full access like Cisco AnyConnect VPNs do, the VPN gateway that acts as a proxy must be appropriately configured to allow the set of applications required by remote users to be operational. There are several different methods to accomplish that:
- URL and CIFS: With a minimal configuration on the VPN getaway, users can access resources using pre-configured bookmarks. These bookmarks allow users to access pre-configured web pages or file shares. In addition, users can also use manual URL entries.
- Application plug-ins: Application plug-ins, also referred to as thin-client connections, support well-known applications such as SSH, Telnet, VNC, and RDP, among others. Though this is recommended, newer versions of Cisco firewalls lack support for most plug-ins.
- Smart tunnels: This option is recommended for all applications that lack a plug-in, providing users with native application client access to enterprise resources.
- Port forwarding: This option is an older technology that, similar to smart tunnels, provides users with native application client access to enterprise resources. It should be used only when using smart tunnels is impossible.
Clientless VPN Authentication
The basic clientless TLS VPN solution uses bidirectional authentication in which both the user and the VPN gateway authenticate with each other.
The VPN gateway (usually a firewall) identifies itself to the remote user by providing an identity certificate, usually signed by a third-party CA such as GoDaddy. It can also be signed by a local enterprise CA.
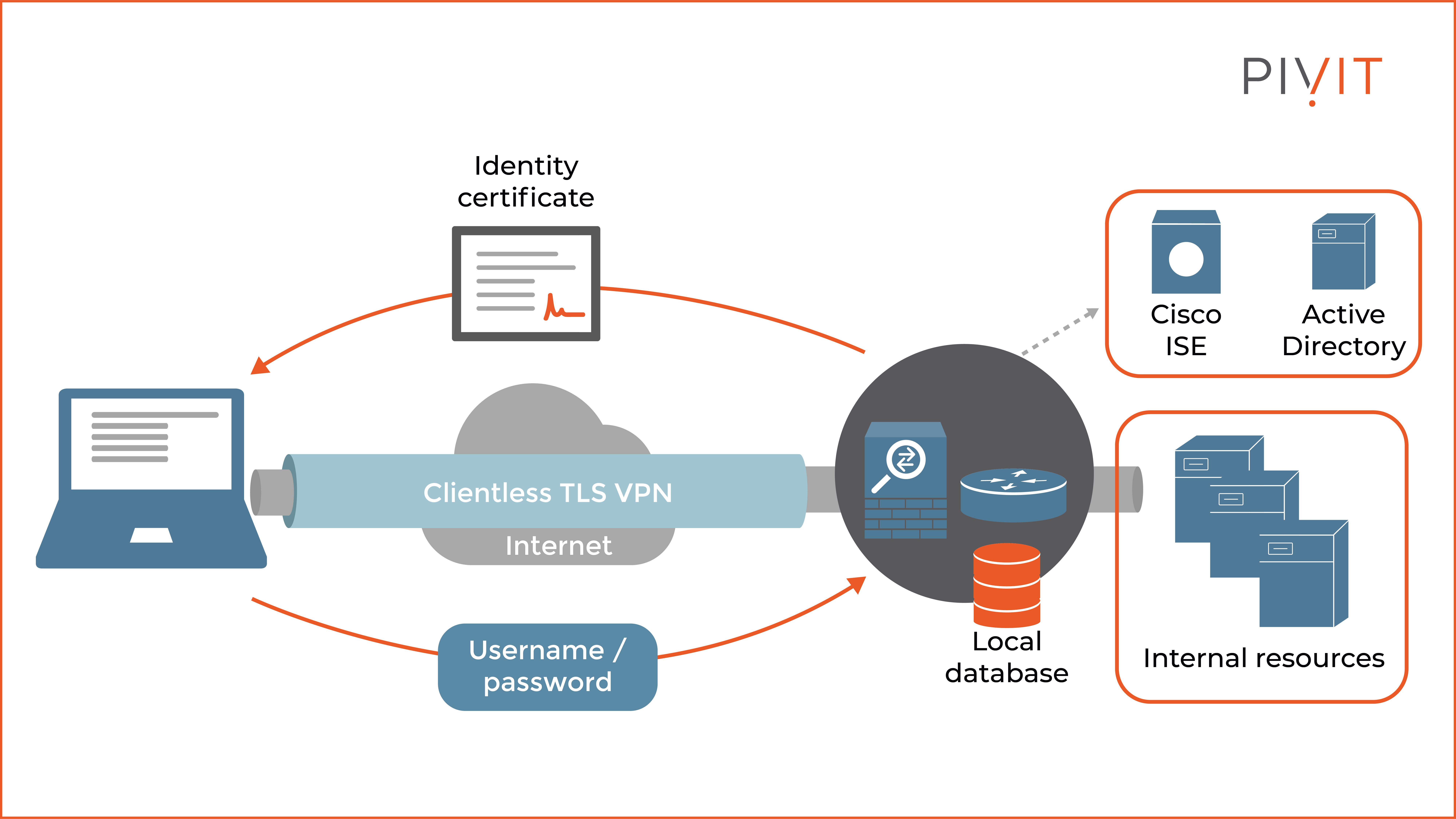
On the other side, the remote user provides a username and password combination, which can be compared against the stored credentials in the local database or against an external server, such as Cisco ISE. The first option is preferred for small deployments, while the second is recommended for large enterprise networks.
Web Portals
After successful authentication, the remote users are presented with a web portal through which they can navigate the protected resources behind the VPN gateway. This way, they can easily access various web resources, such as HTTP and HTTPS pages, FTP and CIFS file shares, and many other supported applications.
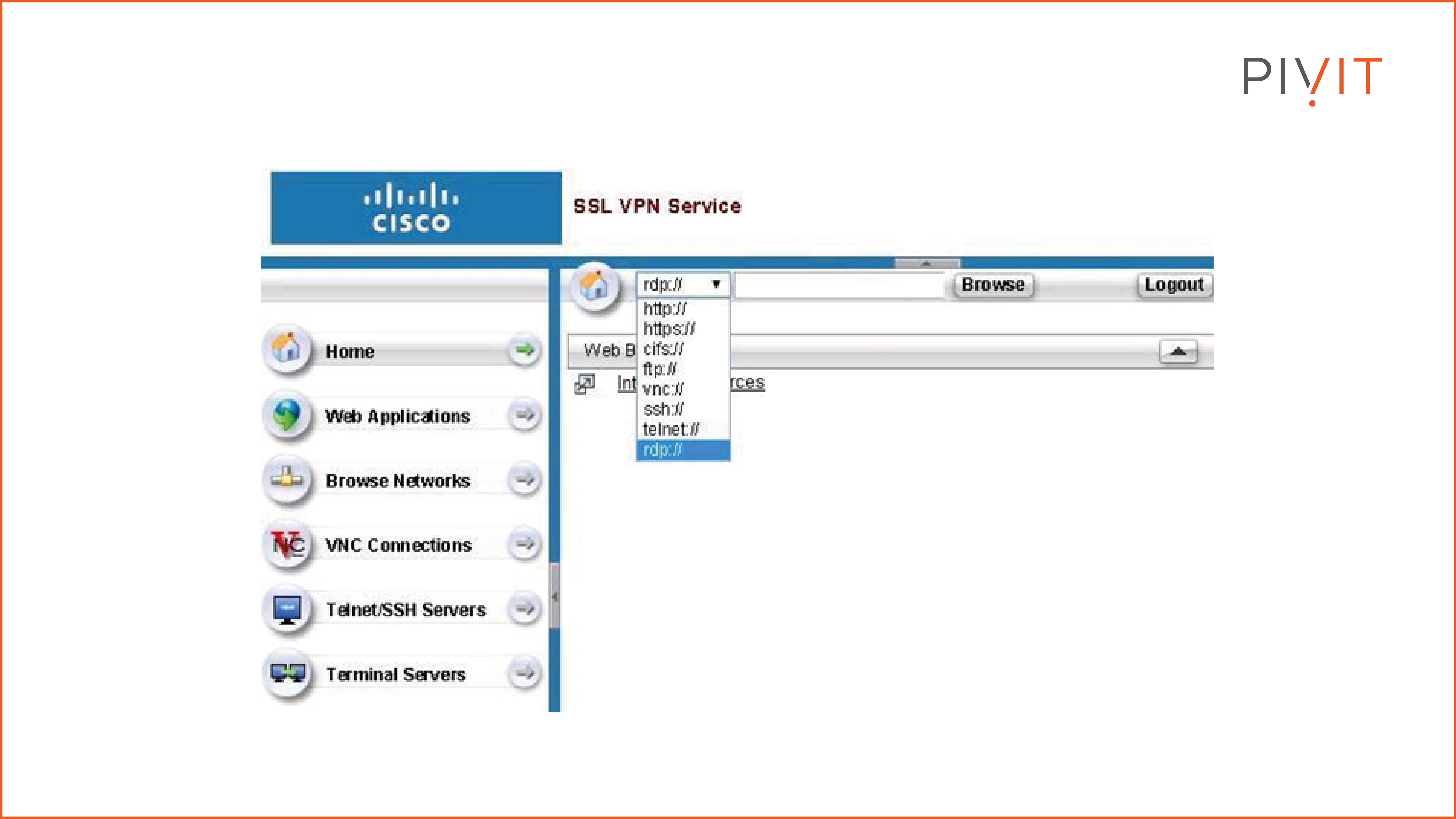
As you can see from the figure above, the web portal is a very user-friendly and straightforward web page.
Based on the remote user's permissions after authentication, certain bookmarks and applications are available on the portal to access the corresponding protected resources. On top of that, you can also edit (redesign) the web portal, so that the overall outlook better fits your organization’s style.
Keep in mind that when implementing clientless VPN on Cisco ASA, by default the firewall permits all portal traffic to all resources. However, you can use a web ACL to permit or deny access to certain resources on the other side of the tunnel when requirements demand that.
Pros and Cons of Clientless VPN
Like all VPN technology today, the clientless VPN solution brings various benefits but also has some limitations.
The clientless TLS VPN solution is very simple and doesn’t require any rights on the user’s side to use it. It relies on the native TLS protocol to protect the data exchanged between the web browser and the VPN gateway when navigating resources through the web portal. Because of that, there is no need for a pre-installed VPN client on the host.
The clientless VPN solution easily traverses most firewalls and NAT-enabled devices in the routing path toward the protected resources in the enterprise network.
However, the clientless TLS VPN solution has some limitations. Because everything is done through the web portal, it may require user training so that users can learn how to use the navigation portal before they begin using it.
Furthermore, due to its proxying nature, real-time applications often experience latency and delay, which makes them unusable at times.
Finally, since this VPN solution doesn’t support all IP applications, sometimes you have to choose a different option.
________________
Hardware Options For You
Here at PivIT, we know the importance doesn't stop with the device itself. It stretches to what is available today, financing options, and more. We make it easy for you to find the hardware to build your network on your terms.

________________
5 Steps to Configure Clientless TLS VPN on a Cisco ASA
The deployment of a basic clientless TLS VPN on a Cisco ASA consists of several steps that must be correctly approached so that the remote VPN users can successfully establish VPN sessions to the VPN gateway and access the protected resources of the organization:
- Enable clientless TLS VPN traffic termination on Cisco ASA’s interface where the remote sessions will arrive.
- Install an identity certificate to identify remote users.
- Configure user authentication by defining the necessary settings in the connection profiles and group policies.
- Optionally, configure basic portal features and access control by creating bookmarks, defining a web ACL for special access permissions, and disabling URL entries or file-share access.
- Optionally, enable split-tunneling.
Clientless VPN That Is Easy To Use
Based on everything we discussed in this article, it’s clear that the clientless VPN solution is a perfect choice for remote users who need on-demand, on-the-fly, secure access to corporate resources.
While there are various limitations to keep in mind, there are also clear benefits that could solve several pain points for your organization as the world of work continues to evolve.
After all, it is easy to implement and even easier to use from the client’s point of view while at the same time providing great flexibility. Keep it in mind the next time you require an added remote access tool to suit your users’ needs.


