Step-by-Step Deployment of Remote Access VPNs on Cisco ASA

Internal communications within enterprise networks bring new and more complex challenges nowadays, compared to how simpler it was 10-plus years ago. In today's modern networks, most of the services and resources required by remote users for daily operations are typically spread out to many locations instead of being hosted in a single place.
As a result, transferring data securely from one remote location to another over an untrusted network, such as the internet, has never been more challenging. The solution comes in the form of a remote access VPN deployment, which provides users with on-demand flexible and secure access to sensitive resources behind a VPN gateway.
In this article, we will provide the following:
- A quick overview of Cisco AnyConnect and Clientless Remote Access VPN types,
- how the benefits fulfill user demands, and
- configure Cisco AnyConnect and Clientless VPNs on a Cisco ASA firewall through the Adaptive Security Device Manager (ASDM) management tool.
Looking for other Cisco ASA articles? Look no further!
- Cisco ASA Firewall Active/Standby Configuration Guide (Part 1 – Overview)
- Cisco ASA Firewall Active/Standby Configuration Guide (Part 2 – Deployment)
- Back to the Basics: Cisco ASA Firewall Configuration Guide
Deploying Cisco AnyConnect VPN
The Cisco AnyConnect VPN solution is usually the most commonly used method by mobile users, telecommuters, and business partners for secure remote access to protected resources inside headquarters or branch offices.
As the name suggests, this VPN deployment depends on a VPN client software installed on the user's machine to establish a secure connection to the VPN gateway on the other side of the VPN tunnel and exchange data securely.
.jpg?width=1920&name=1%20(12).jpg)
As you can see in the image above, several devices, such as a Cisco ASA firewall, Cisco Firepower NGFW firewall, or a Cisco router, can be deployed as a VPN gateway where all remote sessions terminate.
After both entities successfully authenticate through an exchange of an identity certificate, and username and password by the VPN gateway and the remote user, respectively, access to protected internal resources is provided.
Download the guide and refer back to it at any time!
In addition, an external server can be used for authenticating the user credentials. Typically, this is a solution suited for more complex enterprise networks in which an existing user repository, such as Active Directory or Cisco ISE, is available.
Configuring Cisco AnyConnect VPN Through VPN Wizard
Configuring Cisco AnyConnect VPN on Cisco ASA can be done using one of two options: Command-Line Interface (CLI) or Adaptive Security Device Manager (ASDM). When using the CLI, you must know the exact commands to configure Cisco ASA to support AnyConnect VPNs.
On the other hand, the ASDM allows Cisco ASA to be managed through a Graphical User Interface (GUI). In this case, we will use the ASDM manager and cover the configuration process step-by-step.
Three different approaches can be used with the ASDM:
- Approach 1 and 2: These approaches are based on a manual configuration. You can use the advanced menus or the connection profiles menus. Typically, using the connection profiles menus is the preferred method.
- Approach 3: This approach offers an automated deployment to get the same result as approaches 1 and 2, simply by using the AnyConnect VPN wizard from the ASDM manager.
Keep in mind that for data protection, Cisco AnyConnect VPN supports both the IPsec and TLS (SSL in the configuration) technologies. However, TLS VPNs are preferred over IPsec VPNs because they can bypass most firewalls and NAT-enabled devices in the routing path.
________________
Hardware Options For You
Here at PivIT, we know the importance doesn't stop with the device itself. It stretches to what is available today, financing options, and more. We make it easy for you to find the hardware to build your network on your terms.
________________
AnyConnect VPN Wizard Overview
The deployment of a basic AnyConnect VPN on a Cisco ASA consists of several steps that must be correctly configured so that remote VPN users can successfully establish VPN sessions to Cisco ASA.
As you can see in the image below, the goal is to allow the remote user to establish a VPN tunnel to Cisco ASA using the public IP 203.0.113.1 and get access to internal resources in the 10.10.10.0/24 network.
.jpg?width=1920&name=2%20(11).jpg)
Step 1:
Start the AnyConnect VPN wizard.
.jpg?width=1920&name=3%20(9).jpg)
Step 2:
Define the name of the connection profile and the interface that remote users will access for VPN connections. In our case, the connection profile is named "Remote Users," and the outside interface is selected as a VPN access interface.
.jpg?width=1920&name=4%20(5).jpg)
Step 3:
Define the VPN protocols supported by the connection profile required to protect the data traffic. Although SSL (TLS) is generally used, in the example, both SSL and IPsec protocols are selected. Also, you need to define the identity certificate that the ASA will present to remote users.
.jpg?width=1920&name=5%20(5).jpg)
Step 4:
Select the AnyConnect image that ASA will automatically upload to the client's device when necessary.
.jpg?width=1920&name=6%20(2).jpg)
Step 5:
Define the authentication methods for authenticating the remote users before allowing them VPN access. In the example configuration, the local database of Cisco ASA is used for storing the credentials.
.jpg?width=1920&name=7%20(2).jpg)
Step 6:
Define the IP address pool from which IP addresses will be assigned to remote users to access internal protected resources. In the example, the pool's name is "IP_remotepool" and contains IP addresses in the range 10.10.10.10 – 10.10.10.20 /24.
.jpg?width=1920&name=8%20(1).jpg)
Step 7:
Additionally, define DNS servers, WINS servers, and Domain names that specify how domain names are resolved for the remote users when accessing the internal network. In our example, 8.8.8.8 is the DNS server, and "cisco.com" is the domain name.
.jpg?width=1920&name=9%20(1).jpg)
Step 8:
Exempt VPN traffic from translation when NAT is enabled on the ASA. In our case, the local network is named "Server" and exempted from NAT.
.jpg?width=1920&name=10%20(1).jpg)
Step 9:
Enable the Web Launch option (if desired), which allows the AnyConnect client to be installed on a remote client's device.
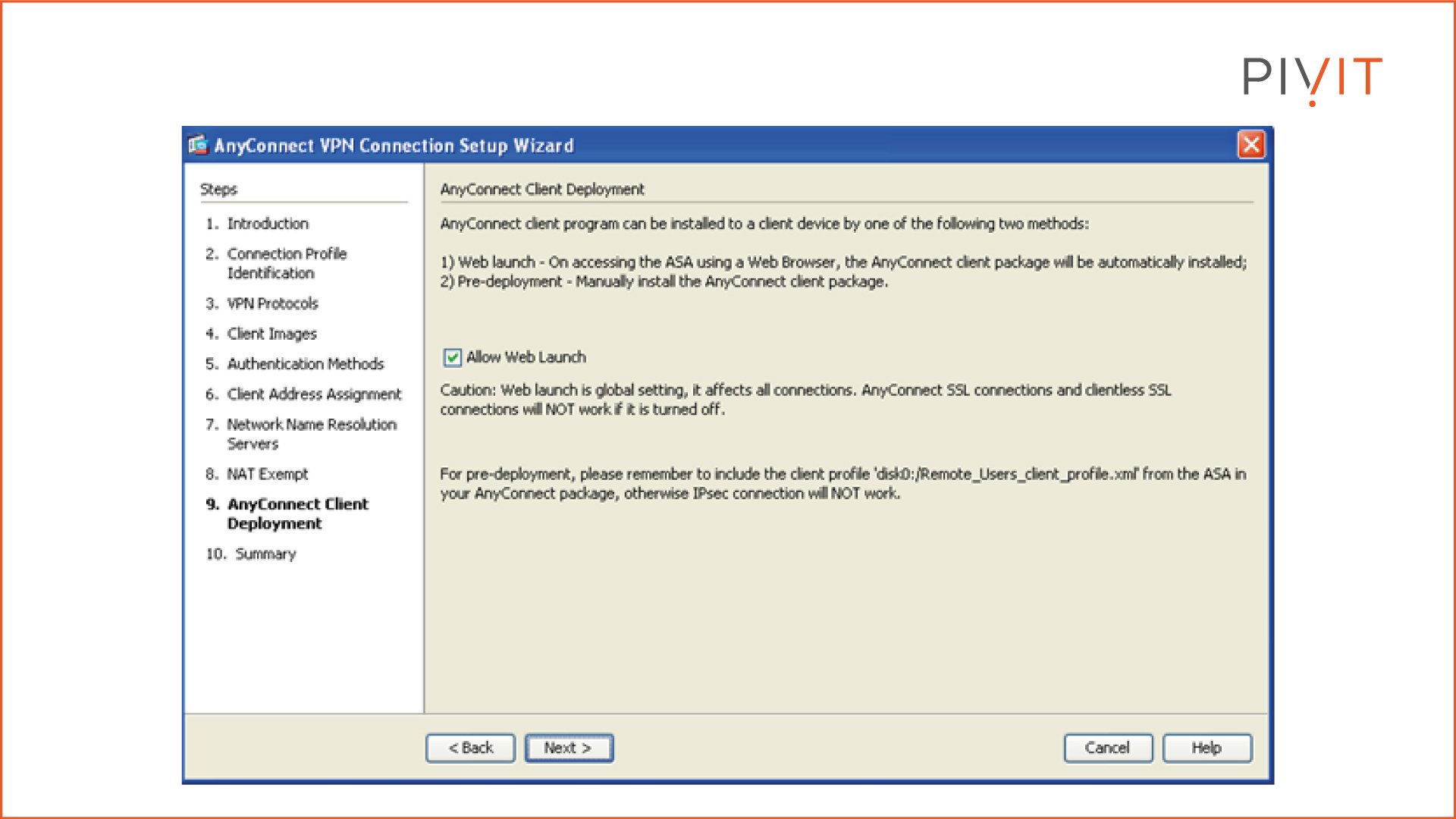
Step 10:
In the last step, you get a summary of the configuration settings specified in the previous steps that ASDM will push to Cisco ASA.
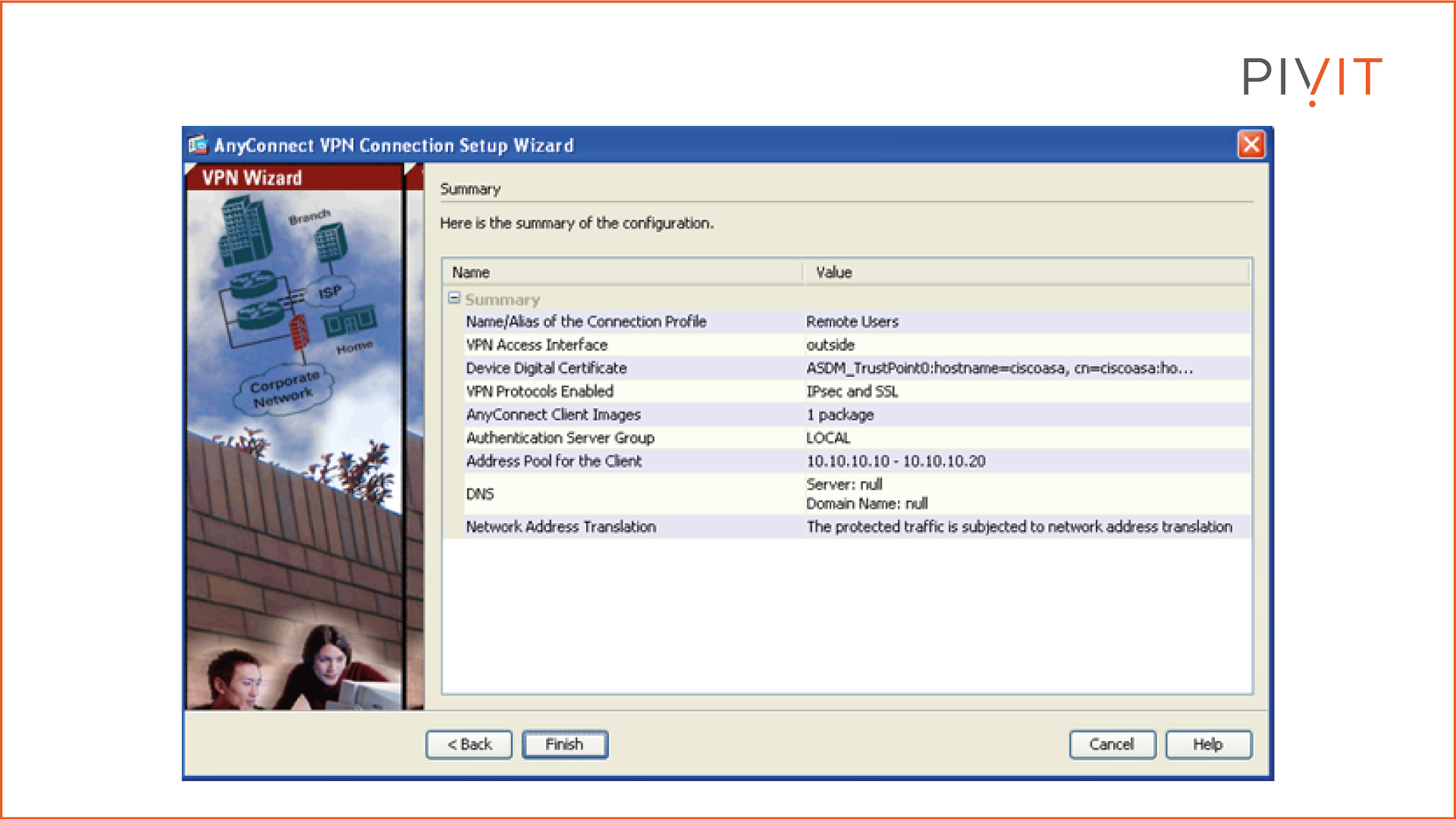
Deploying Cisco's Clientless VPN
Cisco's Clientless VPN solution provides browser-based access to resources located behind the VPN gateway on the other side of the protected tunnel. Instead of using a pre-installed VPN client such as Cisco AnyConnect on the host device, users can access web-based applications, FTP servers, and CIFS file shares only using a TLS-enabled browser.
On top of that, by using application plug-ins, smart tunnels, and port forwarding, users can access almost any application and service that uses static TCP ports. However, although the Cisco Clientless VPN solution is easier to deploy, it provides only limited access to protected resources instead of full access, like the Cisco AnyConnect VPN solution.
Therefore, is it a perfect fit for internet kiosks and business partners when access only to a specific set of services and resources is required.
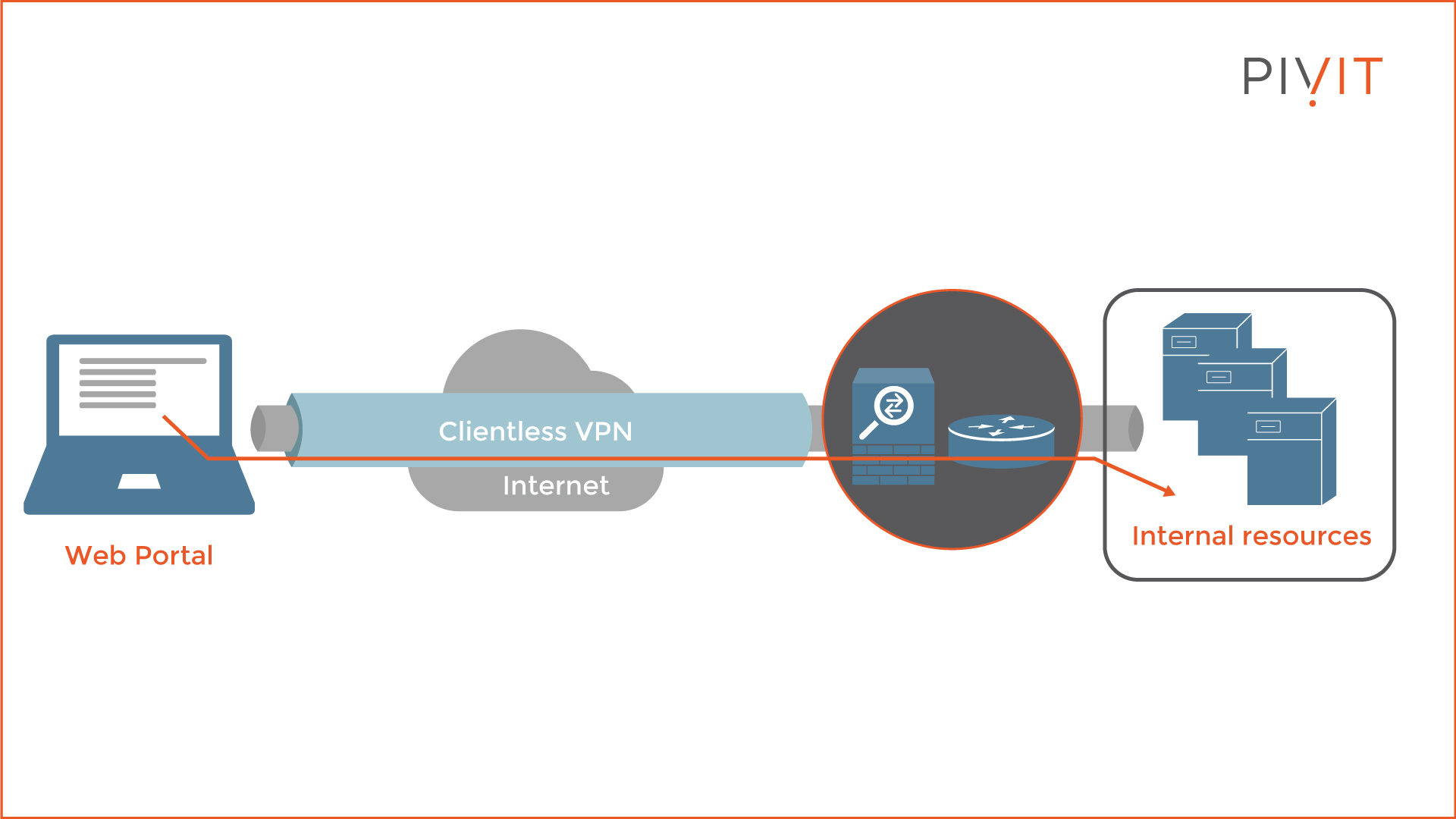
As you can see in the image above, either Cisco ASA or a Cisco router can be deployed as a VPN gateway where all remote sessions terminate. After successful bidirectional authentication, the VPN gateway presents the user with a web portal through which the user can access only those services for which permissions are granted.
Clientless SSL VPN Wizard Overview
The deployment of a Cisco Clientless VPN on Cisco ASA through the Clientless SSL VPN wizard consists of several steps.
As you can see in the image below, the goal is to allow the remote user through a web browser to establish a VPN tunnel to Cisco ASA using the public IP 203.0.113.1 and access internal resources in the 10.10.10.0/24 network.
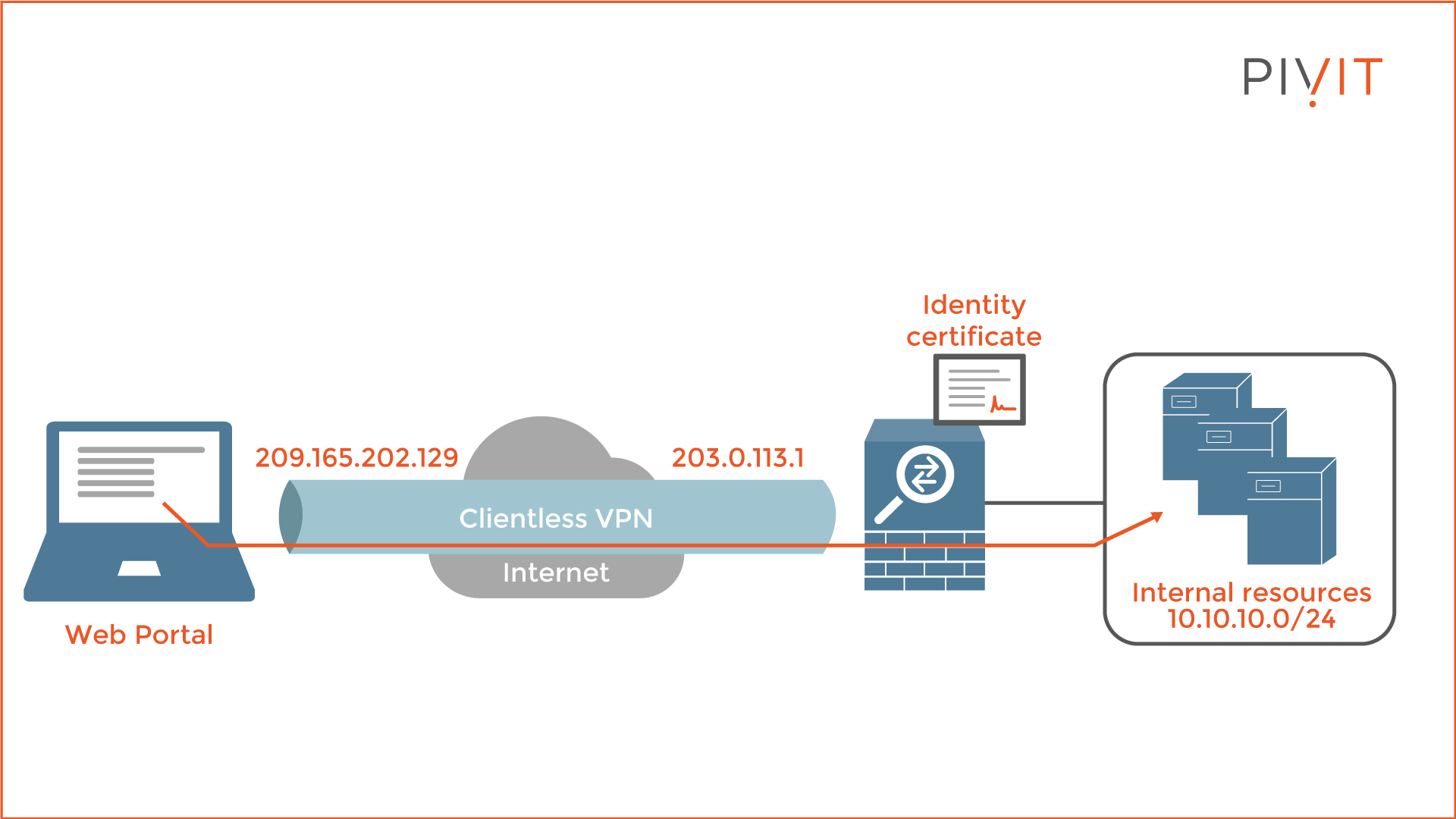
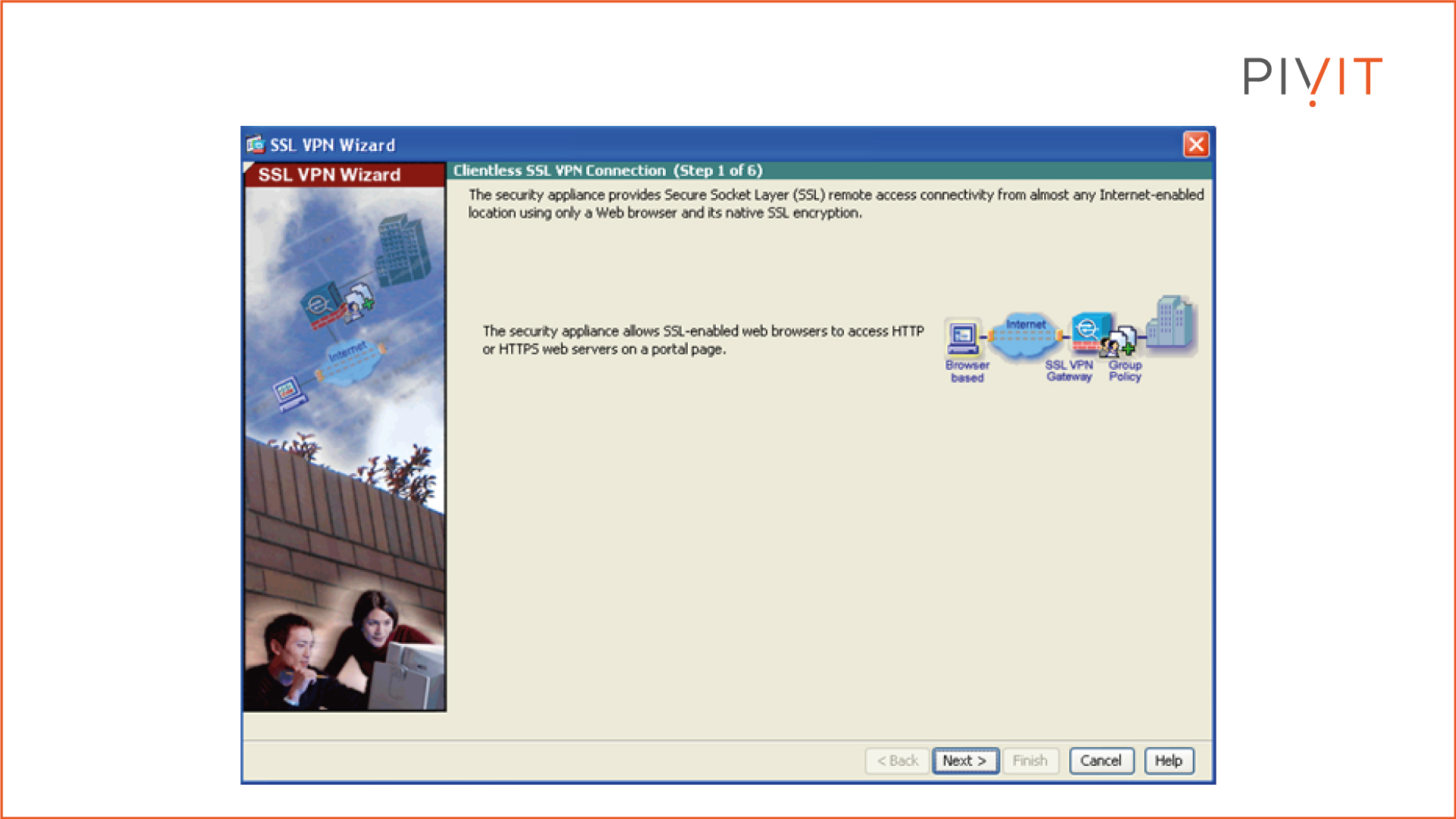
Step 1:
Start the Clientless SSL VPN wizard.
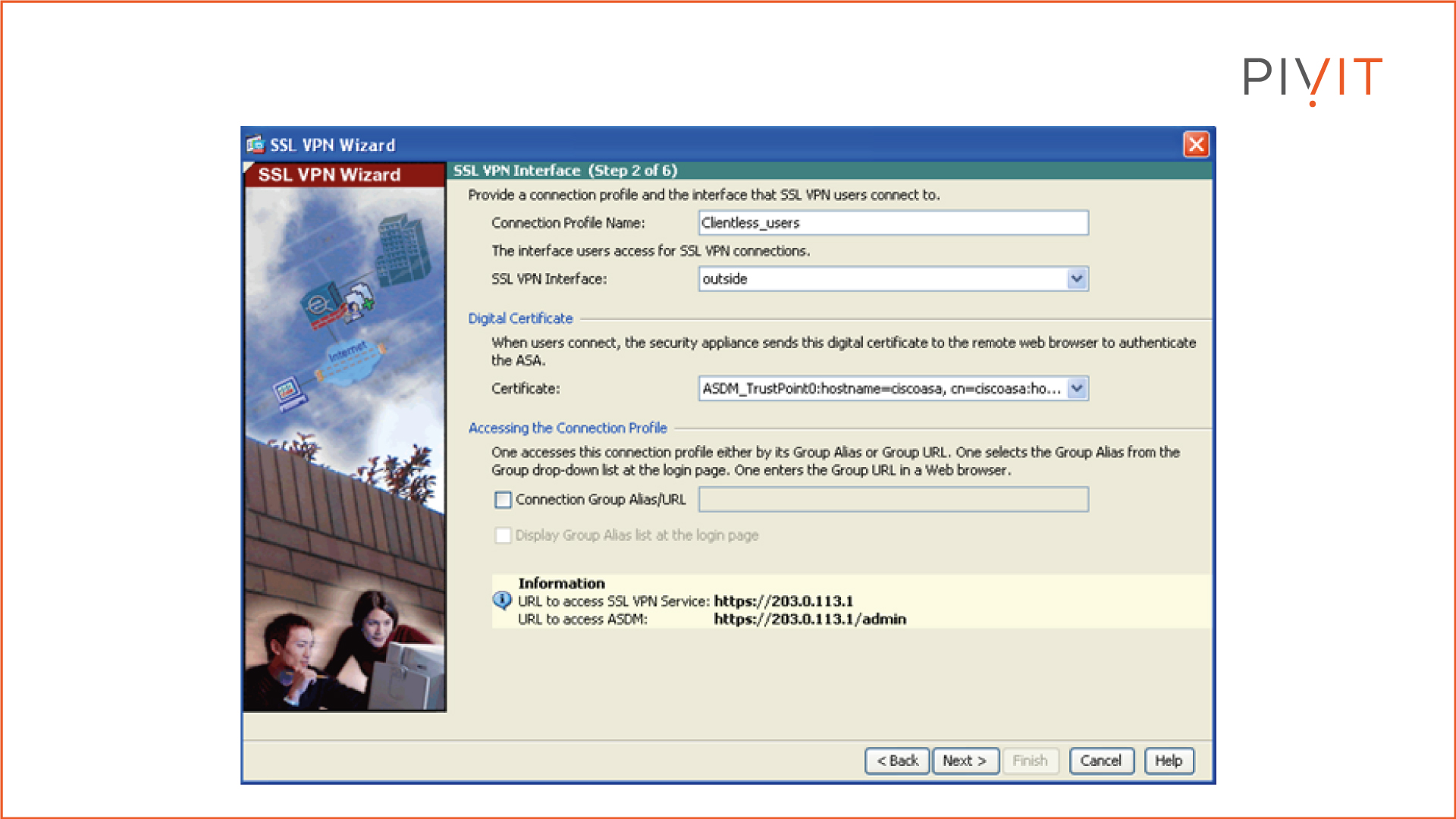
Step 2:
Define the name of the connection profile and the interface that remote users will access for SSL VPN connections. In our case, the connection profile is named "Clientless_users," and the outside interface is selected as a VPN access interface.
Also, define the identity certificate the ASA will present to remote users. Optionally, you can define how the user accesses the connection profile by its group alias or URL.
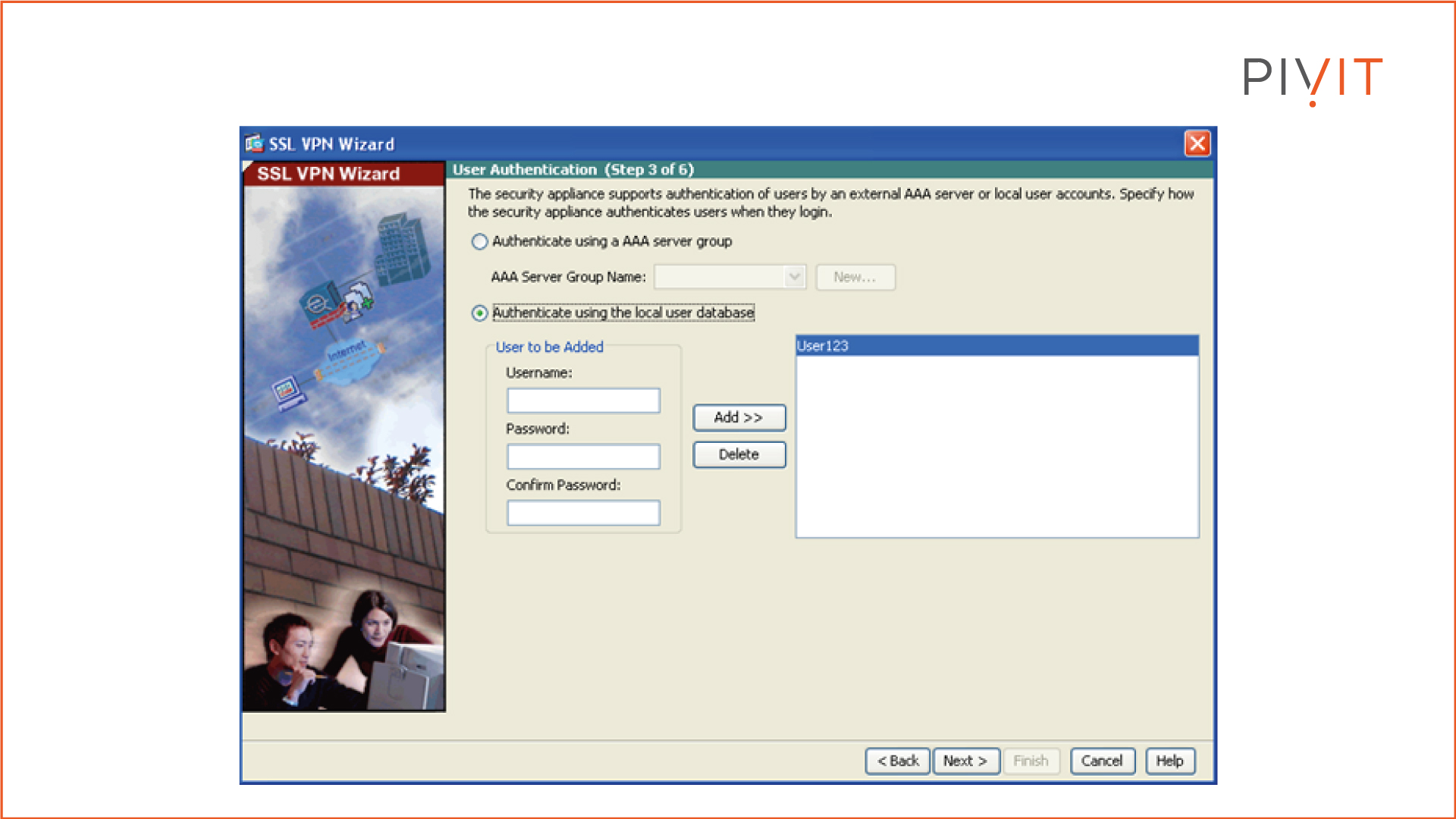
Step 3:
Define the authentication methods for authenticating the remote users before allowing them VPN access. In the example configuration, the local database of Cisco ASA is used for storing the credentials.
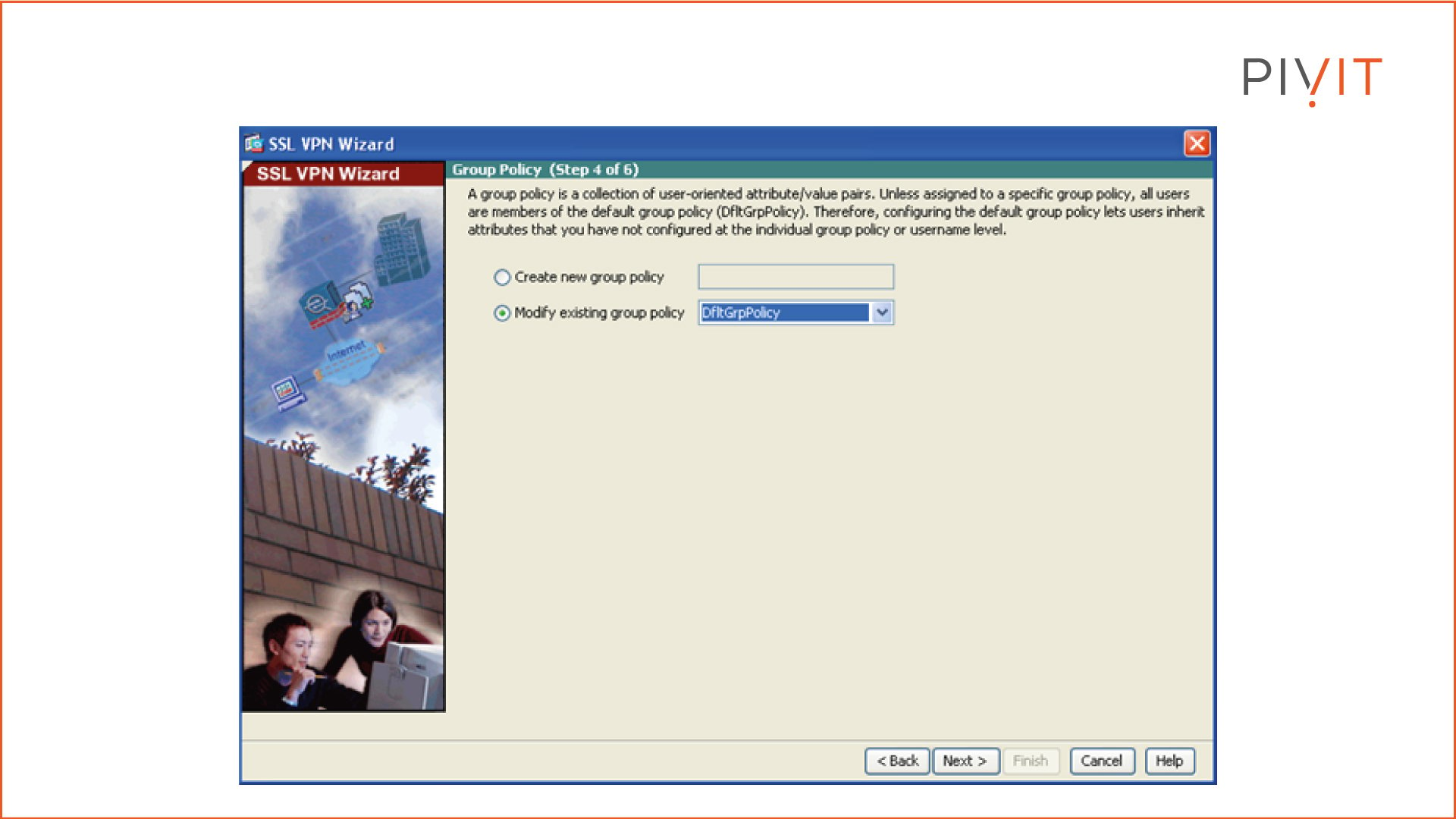
Step 4:
Define which attributes the remote users will inherit. You can either create a new group policy or select one of the existing ones on the ASA. In our case, the default group policy is selected.
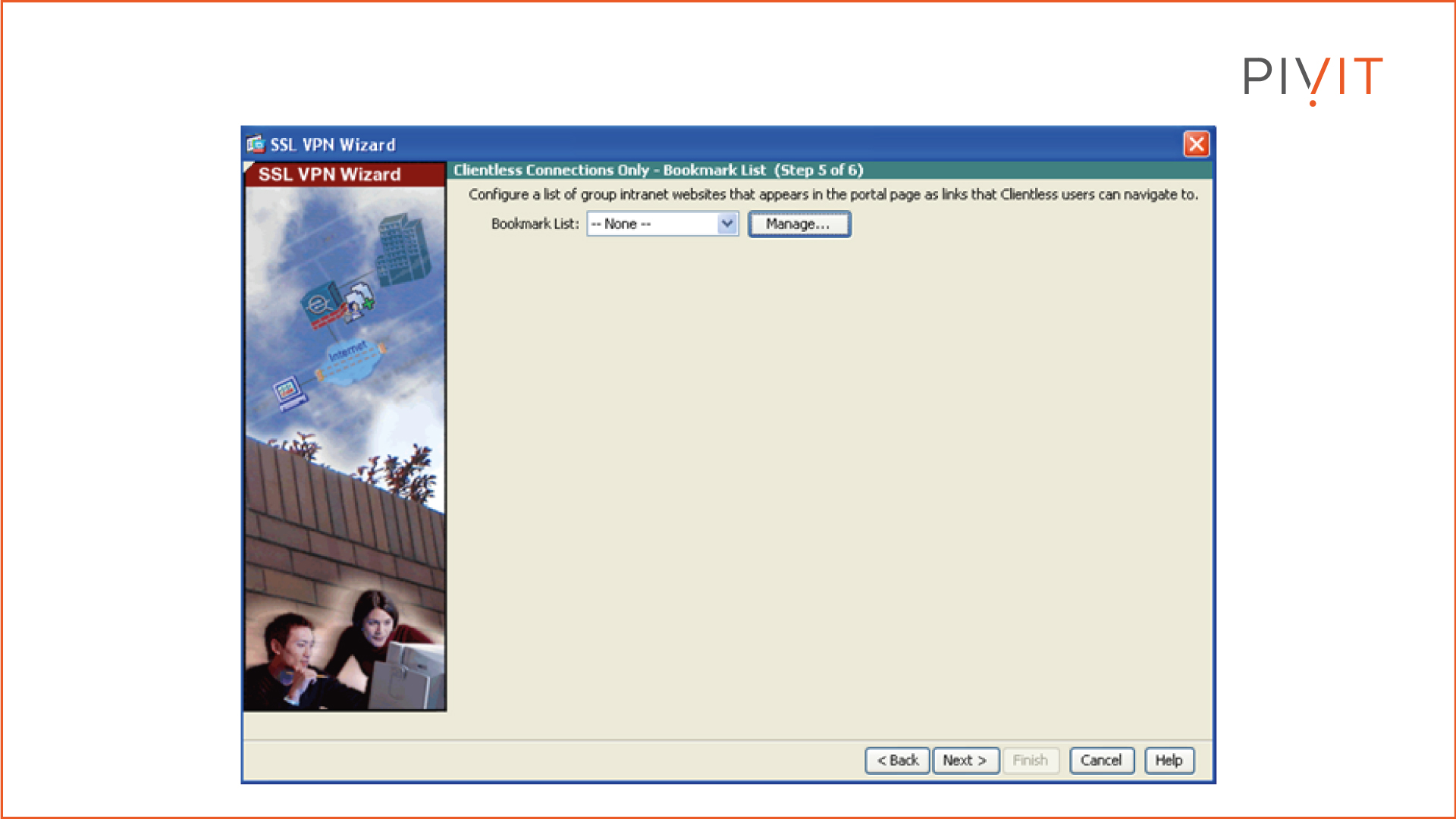
Step 5:
Optionally, configure a list of group intranet websites that will appear on the portal page as links that clientless users can navigate to.
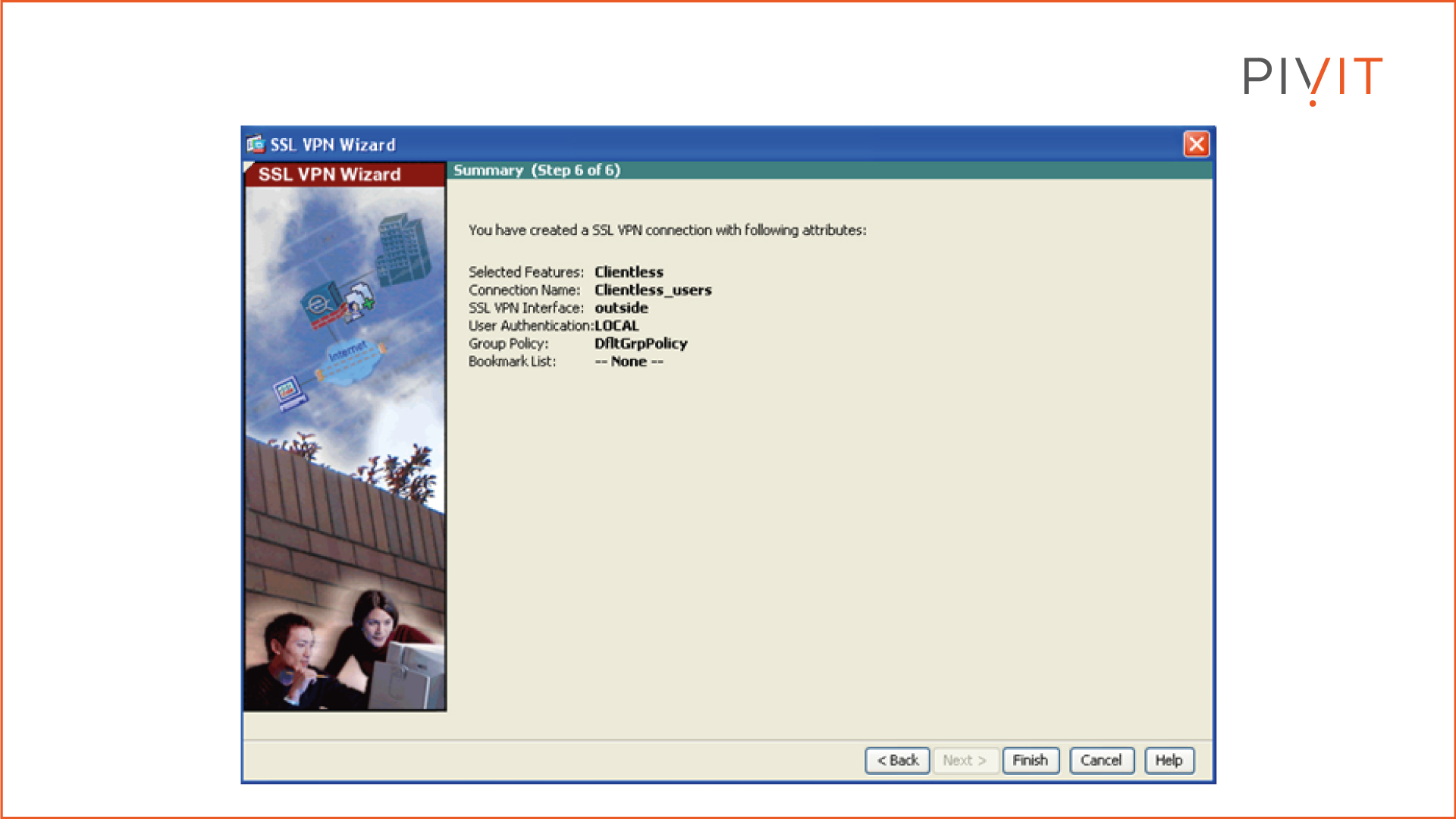
Step 6:
In this step, you get a summary of the configuration settings specified in the previous steps that ASDM will push to Cisco ASA.
Done and Dusted!
Once the basics of the VPN technologies are known and the network and business requirements are well established, both Cisco AnyConnect and Cisco Clientless remote access VPNs can easily be deployed on Cisco ASA. Although several configuration methods can be used, the VPN wizards supported on the ASDM offer the easiest approach, especially for network engineers with limited VPN knowledge.
With an extensive list of Cisco models, PivIT has a comprehensive portfolio of security hardware solutions—for an average of 65% savings.
PivIT also offers OneCall, which gives you top-to-bottom, all-inclusive support of new and legacy hardware. And with PivIT’s EXTEND, you have certified pros at your disposal for everything from installation to troubleshooting and beyond (including VPN configurations!).

