Fundamental Firewall Technology Principles: What Is a Firewall?
.png)
According to the Identity Theft Resource Center's Report, data breaches in 2021 increased by 68 percent, which equated to a record-breaking 1862 breaches. There's no wonder network security is top of mind across all business sectors.
The best defense against a network breach is a well-configured firewall appliance. These firewalls are essential for everyday policy routing and providing advanced security functionalities. Additionally, it is beneficial in filtering different types of traffic, such as email messages, web traffic, or other data that might contain malware and harm a network.
In this article, we will walk you through:
- various firewall technologies, their functionalities, and the numerous features supported,
- other security systems you can use to filter out specific types of traffic in a more productive way, and
- how to protect your network from hidden malware.
Let PivIT handle your firewall installation and configuration with EXTEND, a seamless and confidential extension of your IT teams. Consider us your feet on the street, working to cost-effectively extend your reach and complete your projects.
What Is a Firewall?
A firewall is a security device used to prevent unauthorized access to private networks connected to the Internet. The traffic allowed on the network is defined by firewall policies, where all other traffic attempting to access the network is blocked.
Networks are usually divided into "zones". A "zone" is a portion of a network with specific security requirements and consists of a single interface or a group of interfaces to which a security policy is applied.
As you see from the image below, three zones have been defined: an inside, outside, and DMZ zone. The firewall controls the traffic that passes from one security zone to another.
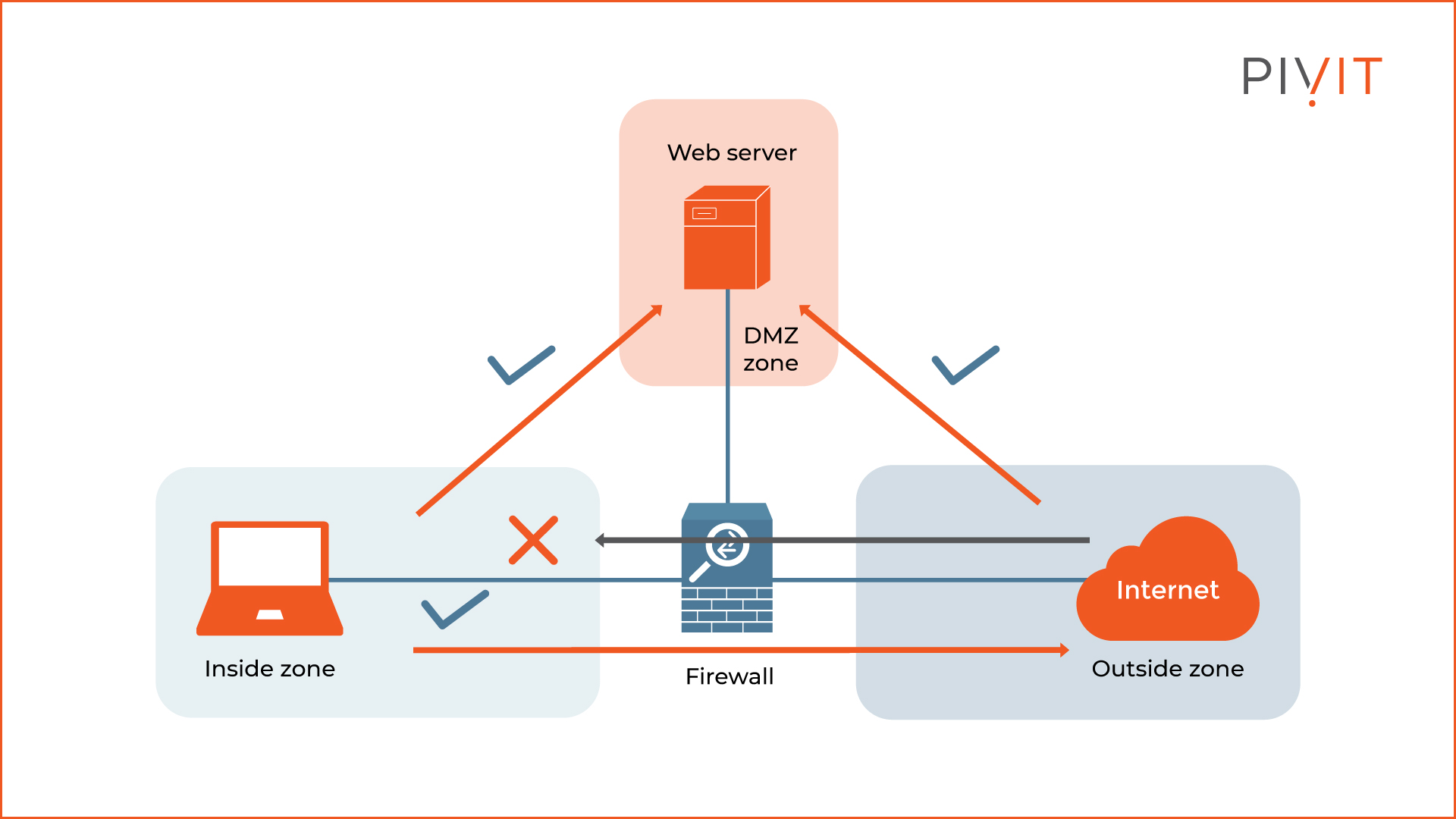
Based on the configured policies, the firewall classifies the traffic accordingly and makes the appropriate decision on whether to forward or deny it. This can be internal communication between departments, geographic locations, data centers, or everyday communications to the public Internet.
When one zone gets compromised, the firewall contains the attack within that zone and stops it from spreading within the enterprise network.
The firewall can be a hardware appliance, a virtual appliance, or software that runs on other network devices, such as a router or a switch. A properly designed firewall solution is simple and scalable but can also be robust and complex, depending on the requirements.
Although firewalls can be placed anywhere in a network, they are typically deployed at the internet edge, where they mainly protect from external threats.
Ensure your network is protected from even the most harmful attacks. View some of our selection guides below:
- Palo Alto vs. Fortinet in a Next-Generation Firewall Comparison
- Build Your Security Strategy with the FortiGate 200F NGFW Firewall
- Your Best Security System: Cisco ASA vs. Fortinet FortiGate
Stateless Firewall
The simplest type of firewall operates in stateless mode, commonly known as a "packet filter". This approach controls access on a packet-by-packet basis by looking at each packet received. So, you might wonder how this differs from the filtering capability commonly implemented on Cisco routers and switches?
It is basically the same thing. A device, whether a firewall, a router, or a switch, makes a permit or deny decision based on a statically configured policy, usually through access control lists.
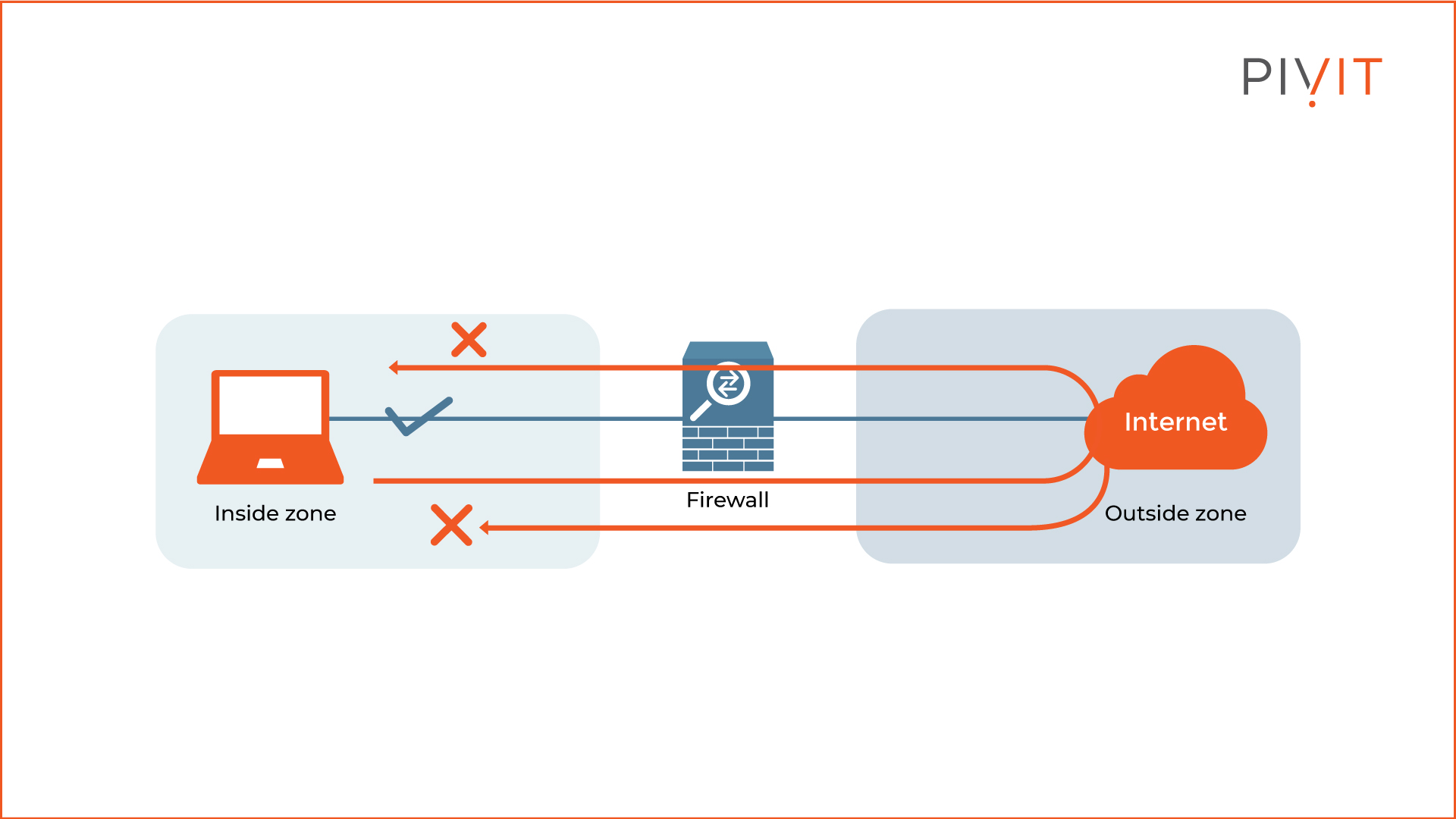
Although this is a straightforward approach, there are some limitations to it. The firewall never permits traffic from outside by default, even though this behavior can be changed when required.
Look at the example topology above. The firewall permits traffic inside the network to be directed to the Internet. However, the returning traffic from the same session is always blocked by default.
Because of this, you will need to explicitly permit all returning traffic from the outside, which is not ideal when dealing with high volumes of network traffic. Since flexibility is almost nonexistent with this method, packet filtering is almost always avoided on firewalls.
Stateful Firewall
A stateful firewall controls access on a session-by-session basis. This approach is much more flexible and provides the same results by applying fewer configurations.
So, why the name "stateful firewall"? When you use this approach, the firewall builds a state table that keeps data associated with what has happened previously within the network sessions.
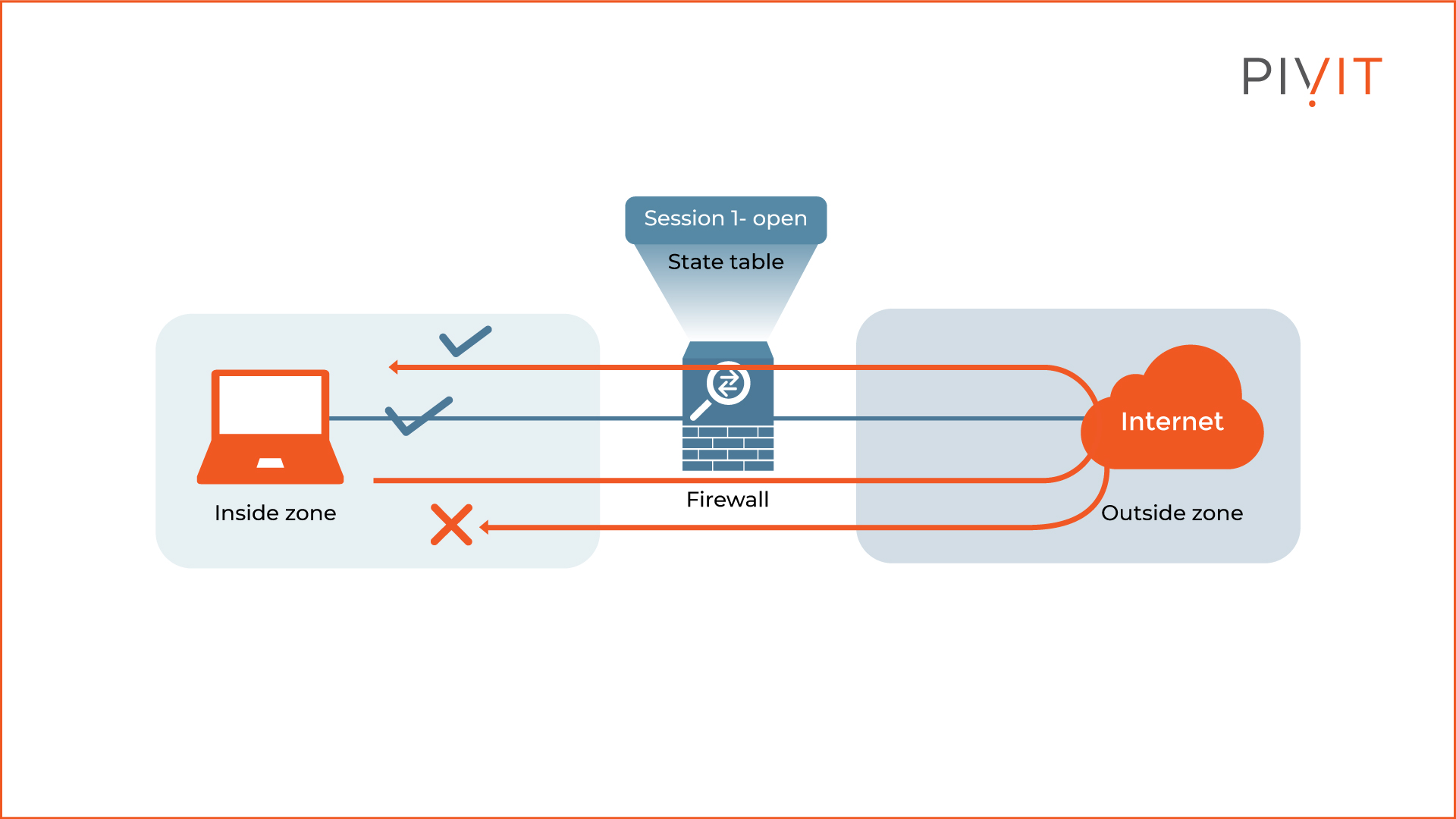
In the image above, you will notice that the stateful firewall allows the returning traffic from the outside (i.e., from the Internet toward the internal parts of the enterprise network).
However, this works only for sessions initiated inside and in the state table. Traffic initiated from outside is denied by default (just like the default behavior of stateless mode) unless explicitly permitted by an access policy.
Next-Generation Firewalls
Firewalls have been around since the 1980s. They started as simple devices using only access control lists based on IP addresses and ports. Over the years, firewalls have evolved into advanced security systems offering new features to meet the needs of today's borderless networks.
The term "next-generation firewall" is used by many vendors that offer the same new features that provide better overall network protection and policy-based filtering.
The Cisco Secure Firewalls, formerly known as Cisco Next-Generation Firewalls, add new capabilities to the standard first-generation firewalls and includes:
- URL Filtering provides the functionality of a web proxy through which all web traffic passes and gets filtered out based on the URL classification settings or other parameters configured.
- Application Visibility and Control (AVC) recognizes applications by analyzing data streams instead of looking at the well-known port numbers for the applications. As a result, you can permit or deny applications and micro-applications. For example, with the AVC feature, you can block Facebook games while at the same time allowing the Facebook application and other micro applications, such as chat, tag, and post.
- Advanced Malware Protection (AMP) provides next-level protection against all variants of malware that you can get along with the traffic.
- The Intrusion Prevention System (IPS) protects against malicious traffic.
- Context Awareness allows you to define policies based on different requirements and filter the traffic based on those.
Long lead times getting you down and making deadlines impossible to meet? What if there's a simple solution and more?
- Get a single source for your IT needs.
- Get hardware options to match your budget.
- Get speedy fast lead times.
Complimentary Security Appliances
Although so-called next-generation firewalls support most, if not all, of the features you might need to provide everyday protection within your enterprise, using a dedicated appliance for such purposes is a better and more productive method.
By implementing Cisco Secure Web Appliance, formerly known as Cisco Web Security Appliance, you can filter out web traffic in a more advanced way by using additional features unavailable on the next-generation firewalls.
The same applies to email traffic. Cisco Secure Email Gateway, formerly known as Cisco Email Security Appliance, can filter email messages entering or leaving your enterprise network. It can also scan for malicious attachments and message content that is against your corporate policy.
Browse Our Extensive Hardware Options
Without a firewall, a network is left open for attack. The consequences can include the destruction or corruption of databases, the leaking of confidential information, and intellectual property theft.
Destructive network attacks can threaten the ability of a company to continue business, which can result in a significant loss of profit. Therefore, companies need to identify these threats by implementing the appropriate firewall.
If you are having trouble selecting a firewall that will suit your requirements, send PivIT a request or connect with our Team in real-time using our chat feature. Know how to configure everything already, but you require new hardware? Click below to view your options!


