What You Need to Know About Virtual Router Redundancy Protocol
.jpg)
In 2021, an unprecedented outage cost Facebook somewhere in the neighborhood of $79 million, proving that even the world’s biggest companies can face challenging periods of downtime.
But take it as a learning experience: you need uninterrupted communications within your enterprise network. The costs of downtime are just too high.
Implementing Layer 3 redundancy is an optimal solution for enterprise networks. It not only provides hardware redundancy but also offers various alternative routing paths throughout the network and non-stop support for default gateway services to end devices.
Virtual Router Redundancy Protocol (VRRP) is a standard redundancy protocol that allows several Layer 3 devices from the same or different vendors to operate together in a group as a single virtual router.
This way, regardless of the participating Layer 3 devices, endpoints always have an active default gateway.
This article will provide the following:
- An overview of VRRP, along with its functionalities and benefits.
- A description of the differences compared to HSRP.
- An explanation of the importance of applying authentication.
- An outline of the configuration steps for enabling VRRP.
Not the networking information you need? View some of our popular articles:
- Learn the Packet Delivery Process (Default Gateway and ARP) - Pt 1
- A Complete Guide To Improving Redundancy with EtherChannel Technology
- The Ultimate Comparison Guide - FHRP Shootout: HSRP vs. VRRP vs. GLBP
The Need for Default Gateway Redundancy
One of the most significant limitations of end devices such as computers, servers, and printers is that they do not support dynamic routing protocols, so they rely heavily on using a default gateway when communicating outside the network.
Therefore, the network design must guarantee that there will always be an active default gateway in the network for them.
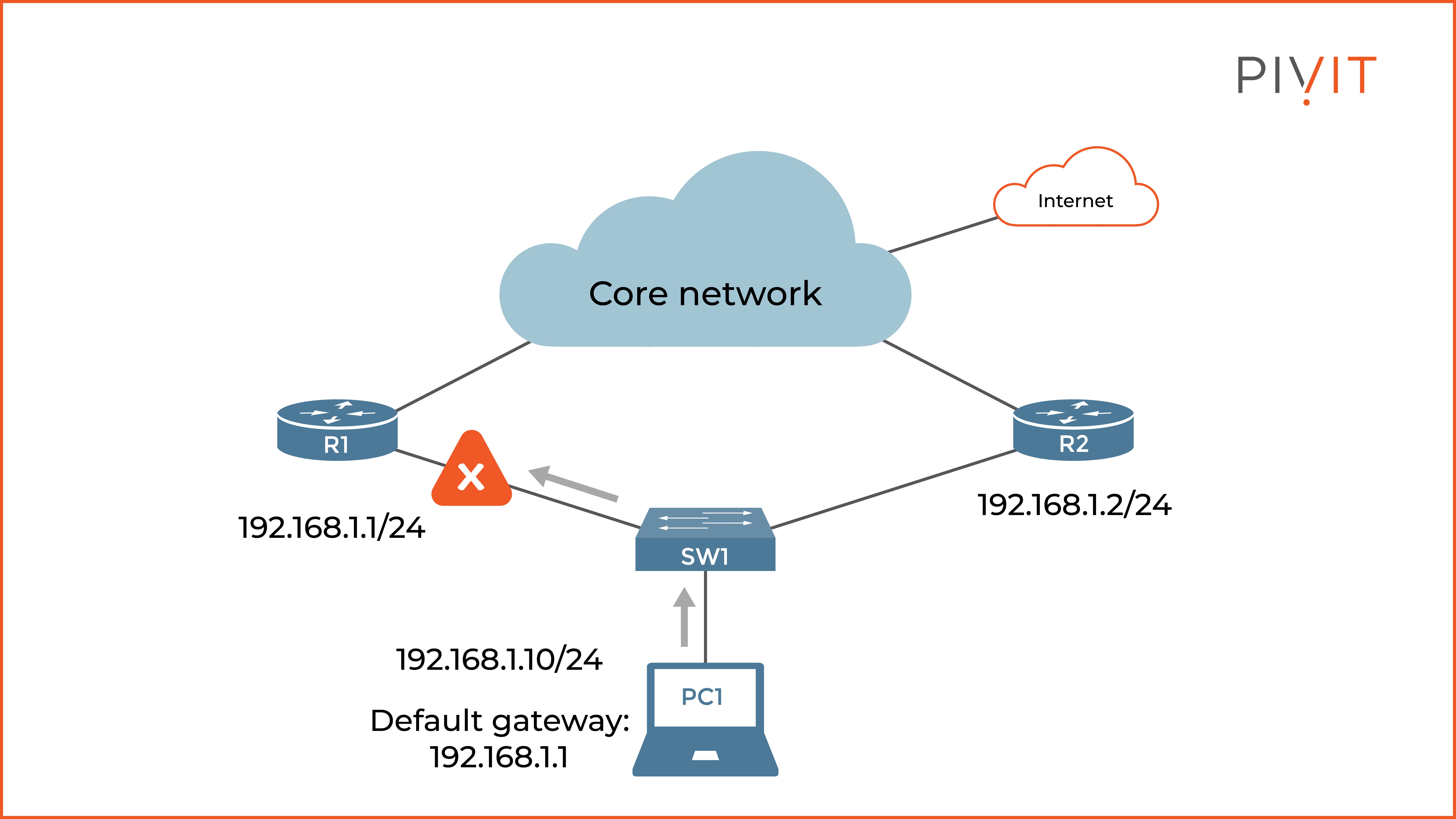
This image shows how PC1 uses R1 as a default gateway. It does so to reach the core of the network or exit the internet. However, when R1 fails, PC1 can no longer exit the local network, even though there is another link through R2.
Only one default gateway can be configured on PC1, posing a problem. It also cannot be dynamically replaced with another. The best option for default gateway redundancy is implementing Layer 3 redundancy protocols such as HSRP, VRRP, and GLBP.
HSRP and GLBP are Cisco proprietary protocols, and because it is an open standard, only multivendor implementations can use VRRP. The best part is that VRRP is similar to HSRP, in operation and configuration.
Learn more about HSRP from our two-part series:
- The Importance of Layer 3 Redundancy: Understanding HSRP – Pt. 1
- The Importance of Layer 3 Redundancy: Understanding HSRP – Pt. 2
What You Need to Know About VRRP
The VRRP concept is straightforward. All you have to do is group two or more routers or L3 switches in a VRRP group so one of the devices will operate as an active unit while the rest will function as backup devices.
All devices must share the same virtual IP address and virtual MAC address to allow such behavior, where you will use the virtual IP as a default gateway by the end devices.
Even though no such virtual device exists in reality, the physical devices (either routers or L3 switches) are aware of these two virtual parameters and use them when they have the active role.
This process allows only one device to be active at a time while the rest of the devices in the group monitor the active device and take over the active role when the active device fails.
In VRRP, we call the active device the master, while the standby devices are known as backup devices. As a result, when end devices send data to the default gateway (the virtual IP address), only the master device in charge of the virtual IP and MAC addresses processes the traffic data.
A device with the highest priority is always elected as the master of the group. The priority can be a number between 0 and 255, where 100 is the default, and the priority value 0 has a special meaning. It indicates that the current device is not participating in the master selection process and allows the backup devices to transition faster to the master role.
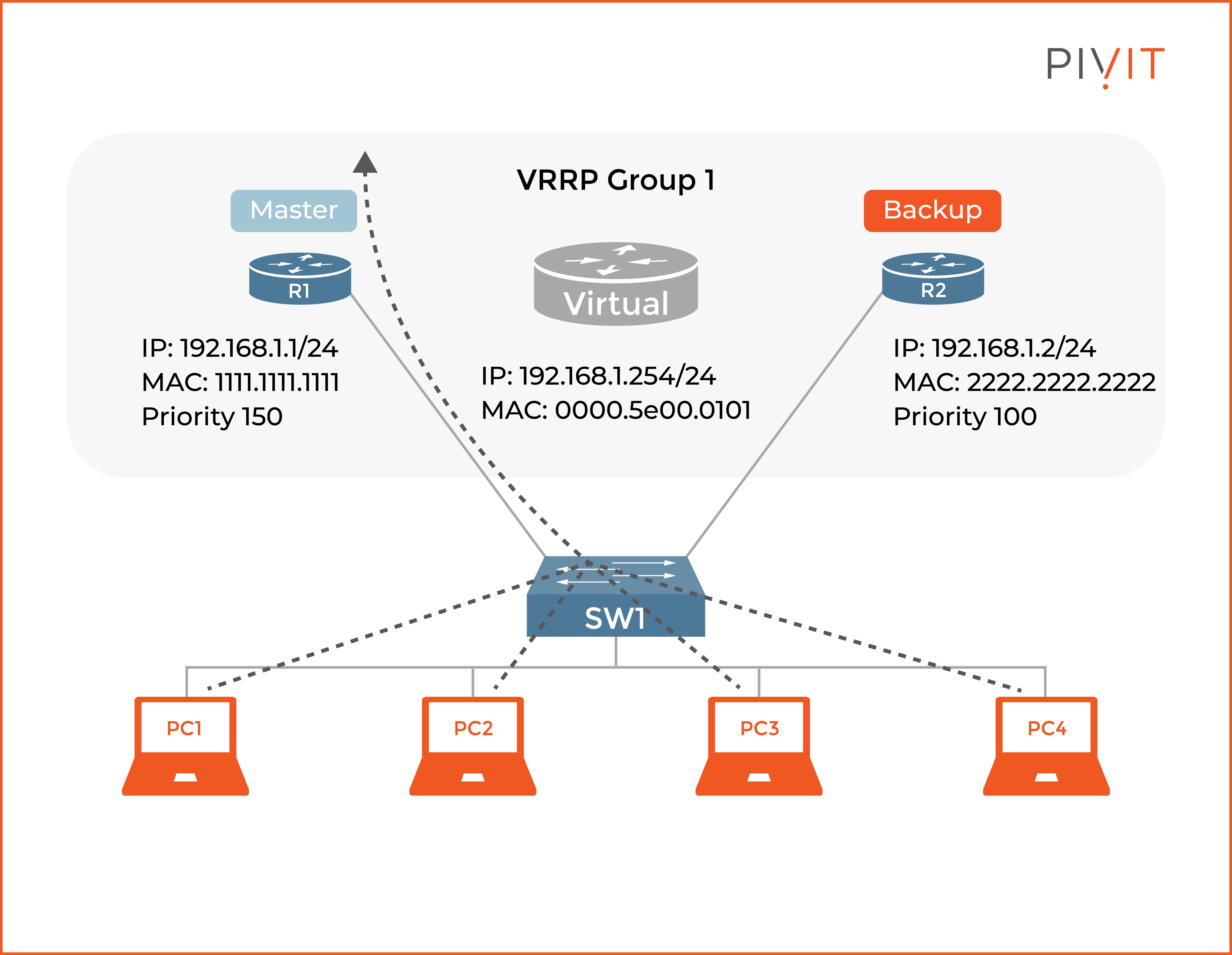
As shown in the image above, R1 is elected as the master in VRRP group 1 because of the higher priority. Therefore, when computers send data to their default gateway 192.168.1.254, R1 will process the data and forward it outside the network.
Remember that you can also provide load-sharing if you configure two VRRP groups in which both R1 and R2 can participate but have opposite roles.
For example, R1 can be master in group 1 and backup in group 2, while R2 be master in group 2 and backup in group 1. This way, you can configure PC1 and PC2 to use different gateways than PC3 and PC4 and spread the traffic more equally among the routers.
_________________
Tired of your maintenance creating new problems instead of solving them? Try PivIT’s OneHub software to aggregate all your IT assets and maintenance contracts – for free – to make management simple.
_________________
The Differences With the HSRP Protocol
HSRP does not allow the use of IP addresses of the physical devices as virtual IP addresses in an HSRP group. In contrast, VRRP allows that approach.
This approach means that on top of the support for using any IP address as a virtual IP address, a physical IP address can also be used as a virtual IP address by some of the group members.
This approach always allows that specific device to be the VRRP master when available in the VRRP group.
Another difference with HSRP is that in VRRP, the master is the only device that sends advertisements (the same as HSRP hello messages in HSRP), sent to the 224.0.0.18 multicast IP address. The default timers are shorter than in HSRP, which allows the VRRP to converge faster.
The default advertisement interval is one second, while the master down interval is three times the advertisement interval and skew time. The skew time is calculated in milliseconds (256 – priority / 256) and ensures that the backup router with the highest priority in the group always becomes the new master.
Remember that Cisco supports millisecond timer values, so you can change the default interval when you want to speed up the convergence process. But be very careful because such an approach in an unstable network can easily result in flapping.
Last but not least, VRRP offers tracking capabilities only through tracking objects. That means if you want to track the status of an interface, you cannot do it directly like with HSRP, but must do it through a tracking object.
The Configuration Process for VRRP
The configuration process for VRRP is quite simple and consists of only several commands for providing basic functionality.
In this example, based on the topology in the image below, we will focus only on configuring R1, but keep in mind that the configuration of R2 would be identical, with differences to locally unique settings only.
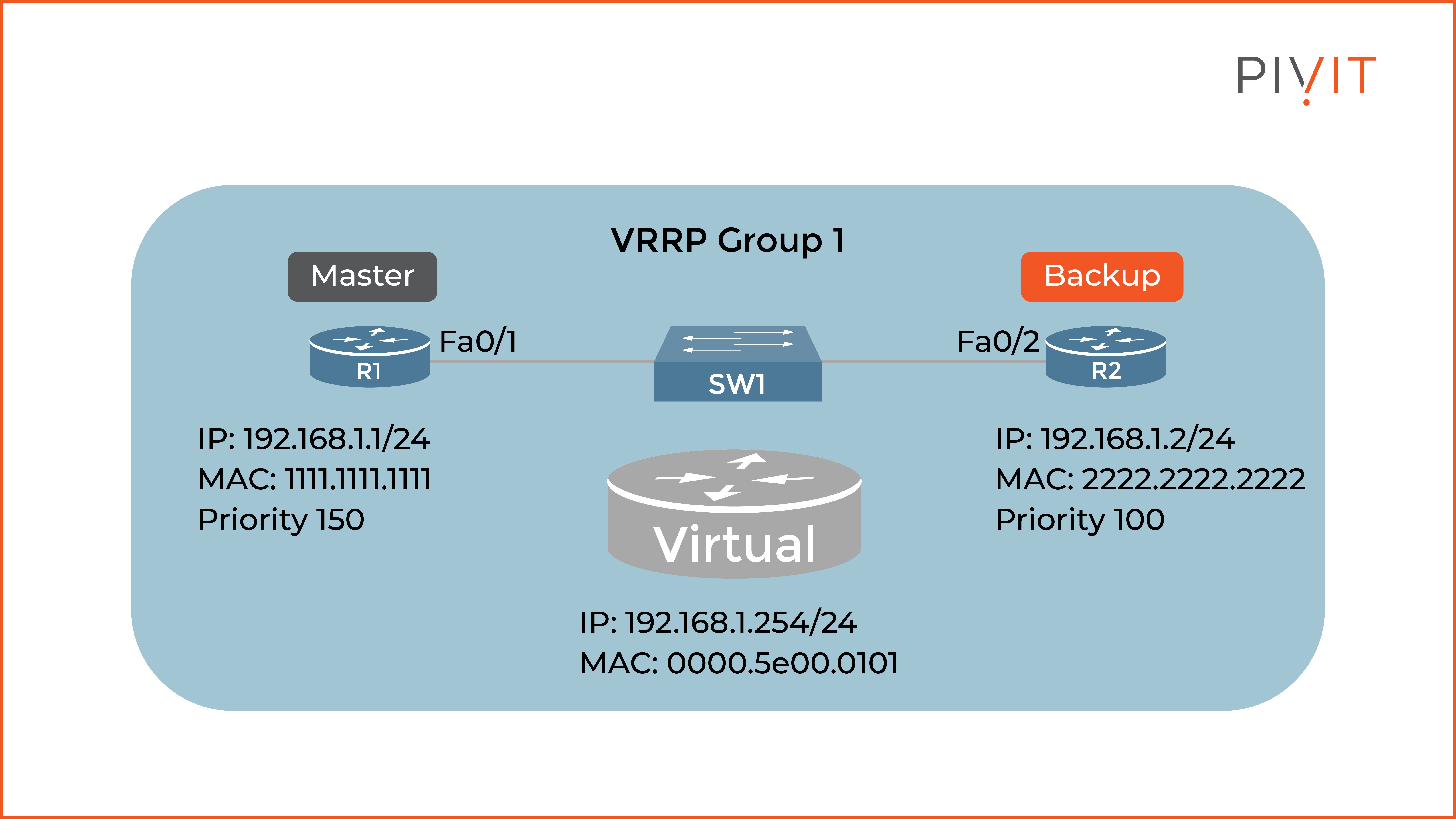
The following commands enable VRRP on R1:
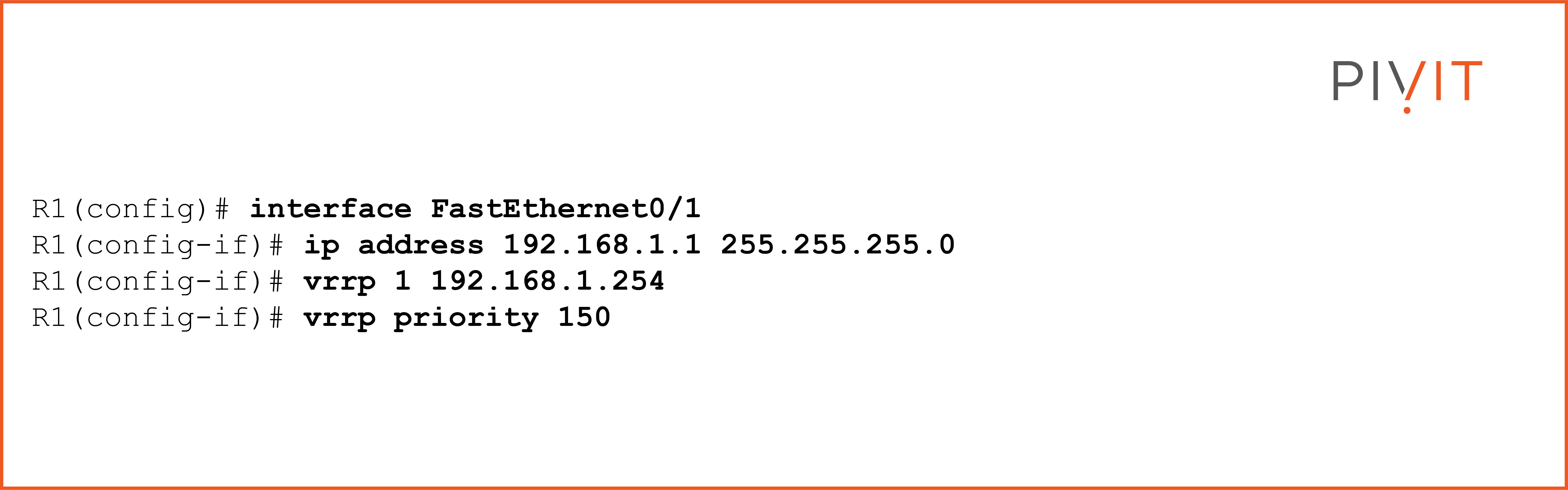
The VRRP configuration is done inside the mode of the interface that connects to the other group member (R2). It does not matter if the link is direct or through a switch as long as they belong in the same subnet.
The essential parameters to be configured are the IP address on the physical interface, the virtual IP address, and in this case, the new priority of 150 that would make R1 the master in group 1.
By default, the preempt feature is enabled with VRRP, so the member with the highest priority will always be the master of the group. In our example, if R1 fails and R2 becomes the new master when R1 becomes active again, it will immediately reclaim the master role from R2.
How to Configure Authentication for VRRP
Implementing authentication when using VRRP protects rogue members joining the VRRP group with the potential to take over the master role of the current master. To secure the VRRP group from such events, you must implement authentication. You can do it in a couple of ways.
However, before starting with the configuration, you should remember that although the VRRP standard supported plaintext and MD5 authentication at the beginning of its existence, that is no longer the case.
On the other hand, Cisco devices still support authentication mechanisms, and recommendations state that you use MD5 instead of plaintext authentication because it is more secure.
The following commands enable plaintext and MD5 authentication on R1:

The Unpopular (Yet Only) Standard Protocol
When using Cisco devices, HSRP is the obvious choice. Though it is the oldest among the redundancy protocols, it is still the most commonly used.
GLBP, on the other hand, is the much more optimized and preferred option for situations when traffic and resource balancing is the primary goal.
With that in mind, this leads us to VRRP. As we mentioned at the start of this article, you need uninterrupted communications within your enterprise network.
Though VRRP is never the first option, it is the only one when implementing Layer 3 redundancy in multivendor networks. Keep this guide handy when you’re ready to get started.
_________________
Still unsure of how all of this works? PivIT's EXTEND offering can step in to augment your team and remote in to configure your gear with expert-level engineers (SmartHands | EXTEND). If you need someone on-site, we have field services ready at a moment's notice.
_________________


