Your Crash Course in Client-Based Remote Access VPN You Can Trust
.png)
Client-based remote access VPNs come in handy when entities from remote locations must access company services over an untrusted network, such as the internet.
Those entities — whether they be mobile users, telecommuters or business partners — need secure access on demand to protect the sensitive data exchanged between them and the VPN gateway located on the other side of the tunnel.
In today’s information age, it’s crucial to keep your company’s sensitive data safe and secured: nearly 8 in 10 consumers choose to do business with organizations based on their reputation for information security, according to Security Magazine.
But where to start, and how best to implement a client-based remote access VPN that you can trust?
In this article, we will:
- Make an overview of the client-based remote access VPN technology.
- Go through the basics and benefits it provides.
- Take a look at the Cisco AnyConnect client.
- Find out more about how to approach VPN implementation on a Cisco ASA firewall by using the ASDM management tool.
Looking for other ways to protect your company’s sensitive information? Try these articles:
- Configure Network Security Using an ACL in SVI Environments
- The Ultimate Guide to DHCP Spoofing and Starvation Attacks
- Palo Alto vs. Fortinet in a Next-Generation Firewall Comparison
An Overview of Types of Client-Based Remote Access VPN
Remote access VPNs are divided into two different categories (or types) of VPNs: full client VPNs — also known as client-based remote access VPNs — and clientless VPNs.
Clientless VPNs are also known as Cisco clientless SSL VPNs when using Cisco equipment. They require users to use only a web browser to access the protected company resources behind the VPN gateway. As a result, this approach provides flexibility but lacks support for full access.
In contrast, the client-based remote VPN (also known as Cisco AnyConnect VPN) requires users to install a Cisco VPN client to establish a VPN to the other side. This VPN client is called Cisco AnyConnect and is the most commonly used VPN client when deploying remote access VPNs.
For data protection, it supports both the IPsec and SSL technologies, even though SSL VPNs are preferred over IPsec VPNs because they can easily bypass most firewalls and NAT-enabled devices in the routing path.
Keep in mind that even though the SSL name is used when discussing security in general, it is an obsolete technology and replaced with TLS. So in reality, we always use TLS instead of SSL.
The Cisco AnyConnect VPN solution can be implemented on both the Cisco ASA firewall and the Cisco Firepower NGFW firewall.
Although the Cisco Firepower NGFW firewall is a newer firewall system, it lacks some features and services supported on the ASA firewall. However, this limitation is actually software-based instead of hardware-based, so it is only a matter of time until those limitations are overcome.
The Features of Cisco AnyConnect
Since our focus is on client-based VPN, the Cisco AnyConnect client plays a key role and it is extremely important to understand how it functions.
- First, it must always be available on the host side, so that the VPN negotiation can begin between the client and the VPN gateway — usually a firewall — on the other side.
- When installed, the Cisco AnyConnect client uses a virtual network adapter that is automatically enabled in the host computer. After being assigned an IP address from the VPN gateway, it starts sending traffic to the other side of the VPN tunnel.
Several methods can be used to deploy the Cisco AnyConnect client to remote users:
- Pre-deploy: The installation or any upgrades are performed manually by the end user. With this approach, Cisco AnyConnect is permanently installed and the user enables it when it needs to create a VPN connection. This is also known as standalone mode.
- Web-deploy: With this approach, the user first connects to the clientless portal on Cisco ASA or Cisco Firepower Threat Defense (FTD) and chooses to download Cisco AnyConnect. Once the Cisco AnyConnect downloader is downloaded on the host, it downloads the VPN client, installs it, and starts the VPN connection. Keep in mind that web-deploy can also be done by using Cisco ISE.
- Cisco Cloud Upgrader: With this approach, the software upgrades are obtained automatically from the Umbrella cloud infrastructure.
Deploying Cisco AnyConnect TLS VPN
A typical remote access VPN solution consists of several components — the user, the VPN gateway (or the headend) and possibly an external authentication server. Each remote user must have a copy of the Cisco AnyConnect client installed on the endpoint required for the VPN deployment process.
On the headquarters or the branch office on the other side, there is typically a firewall, also known as a “headend”, that functions as a VPN gateway and terminates connections from remote clients. A Cisco router can also be used.
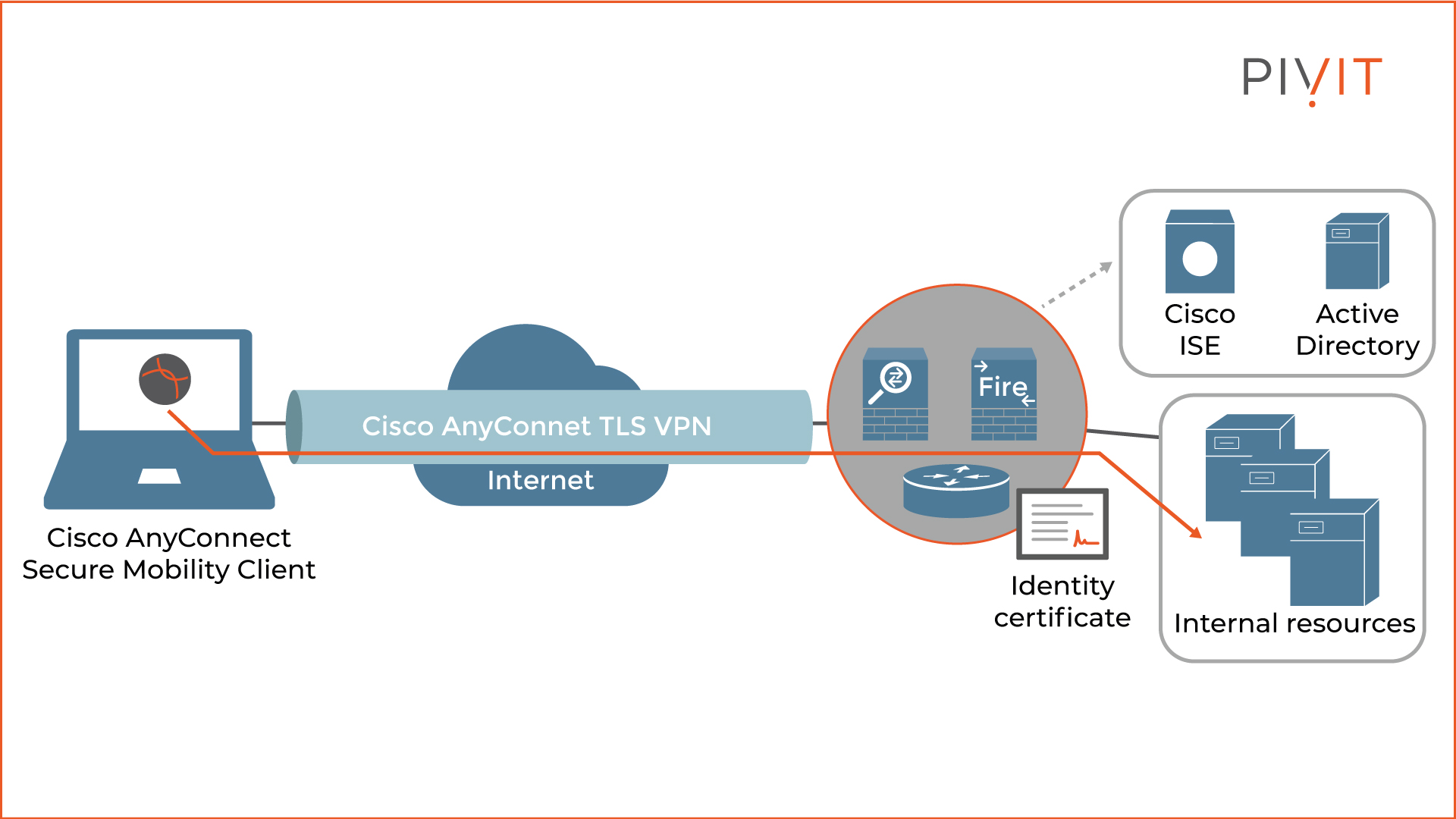
During the VPN establishment phase, both the client and the VPN gateway authenticate to each other. Based on the figure above, Cisco ASA proves its identity to the client with an identity certificate while the users authenticate by providing username and password credentials. Additionally, Cisco ASA can also authenticate the machine. This is done by providing a digital certificate.
After the authentication is successfully finished, Cisco ASA applies a set of authorization and accounting rules to the user session, so the user can start securely sending data through the TLS tunnel and be protected from outside threats.
_________________
If you're having any issues with the configuration of your Cisco ASA firewall or AnyConnect TLS VPN, be sure to contact us for immediate assistance.
_________________
TLS Server Authentication
Because the VPN gateway must identify itself to the remote user, Cisco ASA must own an identity certificate that will be presented during the authentication process. This identity certificate can be created in two different ways.
The first option is a self-signed certificate, meaning Cisco ASA will sign its own certificate. Although this is the fastest and cheapest solution, a general recommendation is for this approach to be avoided because the user will not be able to verify the signature in the certificate and will need to blindly accept the identity certificate provided by Cisco ASA.
Additionally, the ASA can generate a permanent self-signed certificate, so it won’t change after a reboot. As a result, the certificate needs to be accepted as trusted only once by the remote user instead of every single time Cisco ASA identifies itself. This approach is suitable for smaller deployments with only a few remote users in play.
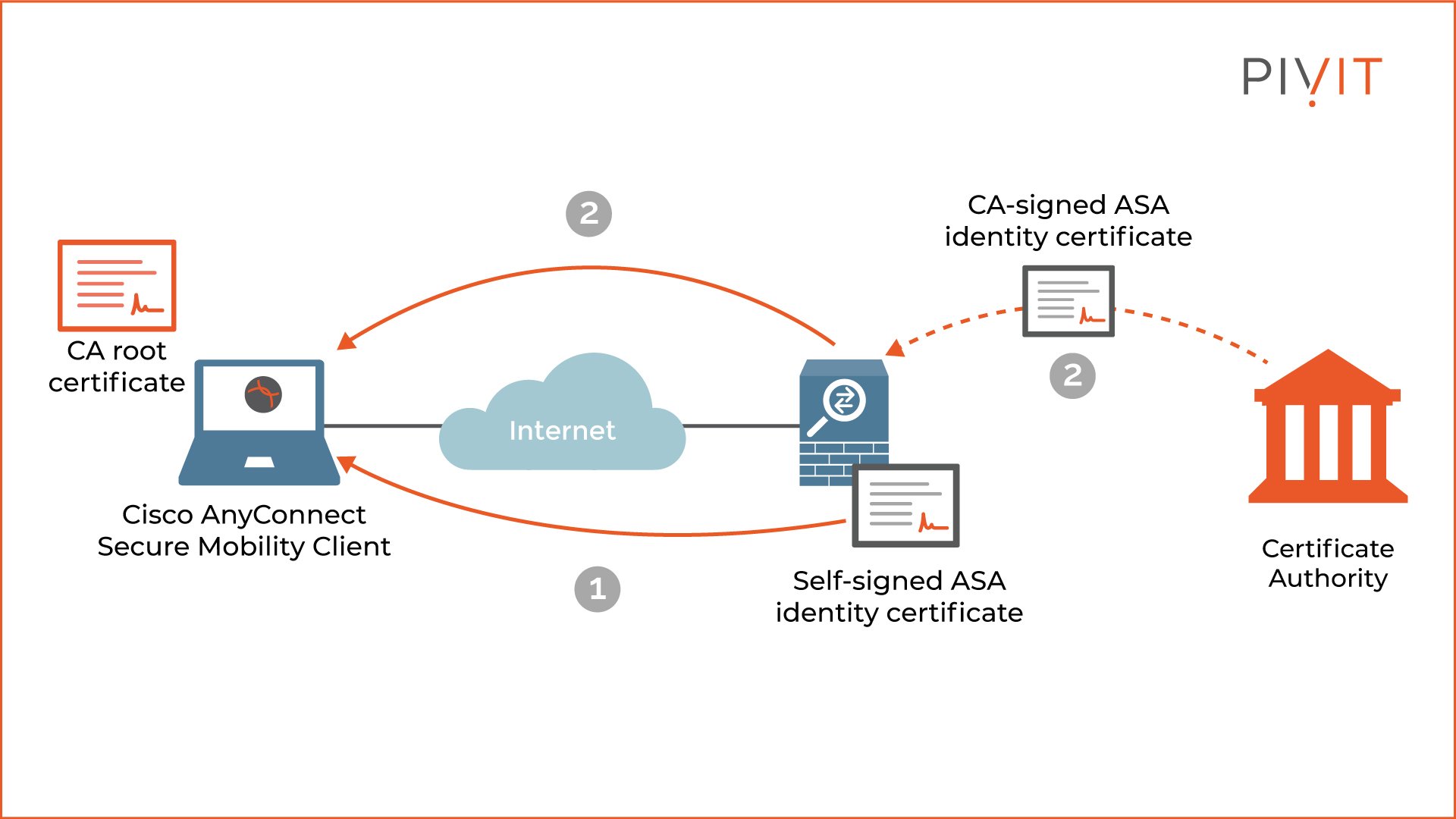
The second and preferred option is for Cisco ASA to use an identity certificate signed by a trusted third-party Certificate Authority (CA), such as GoDaddy or any other public CA. This allows the remote user to easily verify the signature of the ASA’s identity certificate without getting any warning messages about trust-related issues.
TLS VPN Client Authentication
The way the remote user is authenticated against Cisco ASA depends on the firewall’s configuration. The default approach is to prompt the user for a username and password, which after being provided, are compared against the credentials stored in the local database. When there is a match, the authentication passes. Otherwise, the VPN deployment process stops.
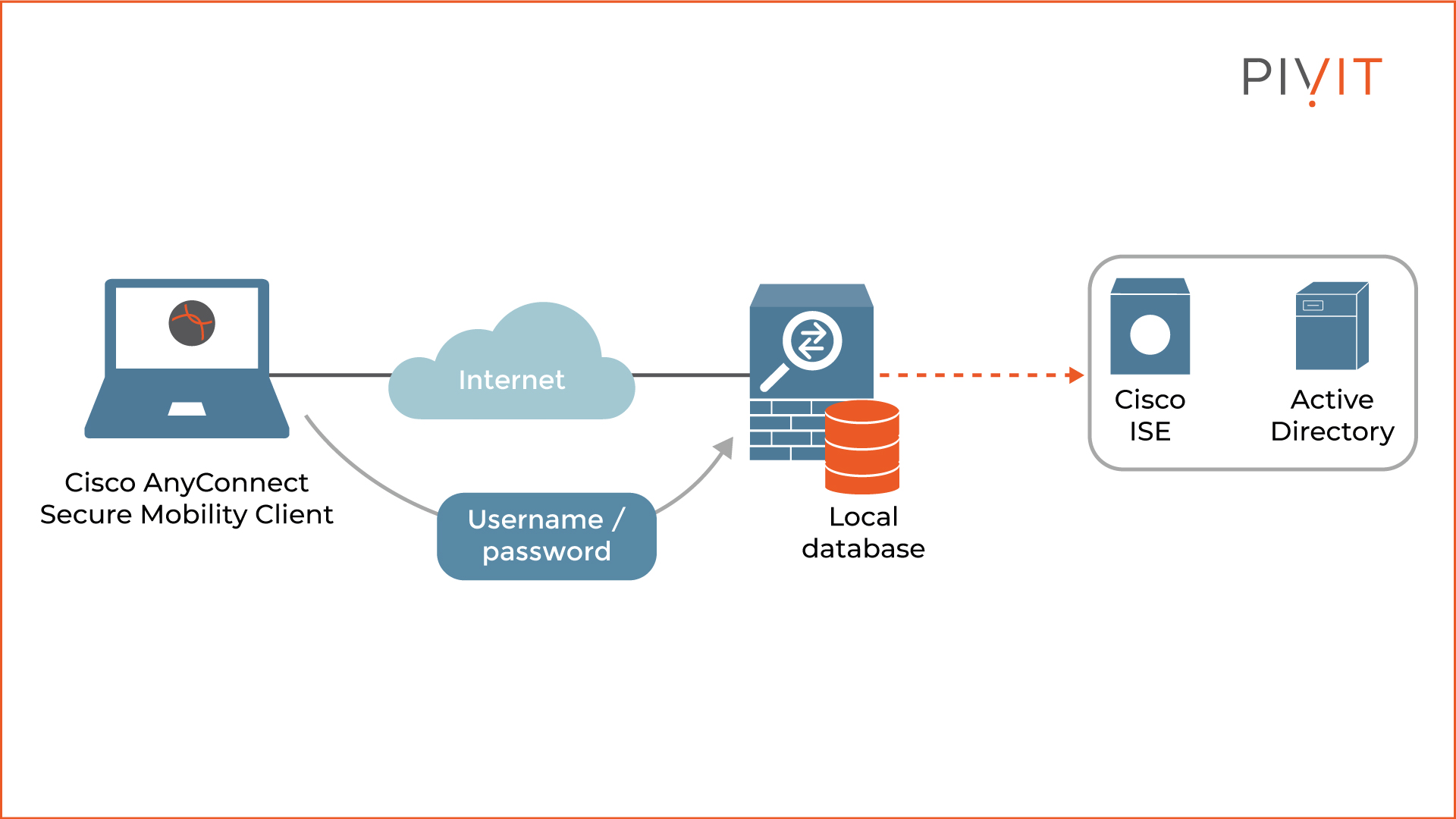
Additionally, an external authentication server such as Cisco ISE or Active Directory can be used to verify the provided credentials. This is a more suitable solution for large and complex deployments, such as in enterprises with many employees, or when a user database already exists in the system.
VPN Client IP Address Assignment
For the remote user to be able to access resources beyond the VPN gateway, it must be assigned an IP address. It is used on the virtual network interface adapter of the client endpoint. This IP address provided by Cisco ASA is private and allows the user to access any segments of the internal network behind the VPN gateway.
This part of the VPN deployment can be done in several different ways on Cisco ASA, but the most common one is by configuring an IP address pool and assigning it to the default or custom connection profile that will be applied to the remote user’s session.
Basic AnyConnect TLS VPN Configuration Steps on Cisco ASA
The deployment of a basic AnyConnect TLS VPN on a Cisco ASA consists of several steps that must be correctly approached so that the remote VPN users can successfully establish VPN sessions to the VPN gateway:
- Installing a copy of the Cisco AnyConnect client image on Cisco ASA, which will be pushed to the clients in case they use an outdated version.
- Enabling Cisco AnyConnect TLS VPN on Cisco ASA’s interface, where the remote sessions will terminate, and installing an identity certificate for identification.
- Defining an IP address pool for assigning IPs to remote users.
- Configuring identity NAT for bypassing common NAT-related issues in a VPN deployment.
- Editing the default and/or custom group policies and optionally enabling split tunneling for sending only selected traffic for protection through the VPN tunnel.
- Finally, editing the default and/or custom connection profiles and defining various parameters such as authentication method, IP addressing, and other related settings.
What About More Advanced Configurations?
The remote access VPN deployment process offers many additional features and tuning parameter settings. But what’s been covered above is more than enough to understand Cisco AnyConnect VPN and its benefits, as well as how to approach the configuration process on Cisco ASA.
If you're looking for more advanced configurations, let our team of engineers help you out with our EXTEND SmartHands offering. We offer you global access to engineers, to locally access your infrastructure. They take on a range of responsibilities to extend your IT team, without the added overhead of hiring a full-time engineer.
Our engineers are your ticket to global hands and feet as they collaborate with your engineering teams to resolve issues and take on projects, creating the most efficient and effective network that meets your business needs.