Lock It Down: Your Introduction to Securing Data with VPN Technology
.png)
The internet as we know it today provides the most efficient way for communication and data exchange between millions of people worldwide.
However, the internet, in its nature, is considered to be an untrusted network. This can easily lead to information theft, data loss, manipulation, and cyber-attacks, among other side effects. Cybercrime alone is projected to cost $10.5 trillion by 2025, according to Cybersecurity Ventures.
For those reasons, it’s important to implement an additional layer of security for your important data. The best way to do this in terms of cost and flexibility is by using a Virtual Private Network (VPN).
This technology provides privacy for the data traffic exchanged publicly on the internet using cryptography to satisfy modern-day security requirements for confidentiality, integrity, authentication, and anti-reply protection.
Today in this article, we will:
- Provide an overview of VPN technology.
- Outline the components included and the benefits they provide.
- Explain the various VPN types that are supported.
Not the security tips you’re looking for? Try these articles:
- Configure Network Security Using an ACL in SVI Environments
- Must-Have Port Security: Simple but Efficient Layer 2 Protection
- Your Best Security System: Cisco ASA vs. Fortinet FortiGate
Understanding VPN Technology
The main goal of VPN technology is to protect data that is transmitted over untrusted internal or external networks, such as the internet, from various threats, especially man-in-the-middle attacks.
In other words, a VPN provides a way to extend a private network between two or more entities or sites located in different remote locations over an untrusted medium.
On top of that, VPNs disguise your online identity, making it more difficult for third parties to track your activities, and preventing unauthorized people from eavesdropping on the traffic exchanged.
To better understand VPNs, let’s first find out more about the meaning of each word in the acronym itself. Then, we will dive into more technical details about the technology:
- Virtual: This part represents a logical network independent of the physical infrastructure through which the VPN is deployed.
- Private: This word means that privacy can be provided using two approaches: non-cryptographic and cryptographic. The non-cryptographic approach does not depend on the IP addressing and routing schemes applied. On the other hand, the cryptographic approach provides three key services: confidentiality, integrity, and authentication. That’s why the cryptographic approach is de facto the default approach with VPNs.
- Network: The interconnected computers, devices, appliances, and resources that are grouped to share all sorts of information.
Enjoying the Benefits of VPN Technology
Using VPNs provides many benefits to enterprises and anyone using them as a service for securely transferring data from one site to another. These benefits are:
- Security: The security “features” that come with the VPNs are not fixed and very much depend on your requirements and what you want to implement, as well as the support for the various encryption and hashing algorithms on your equipment. In the end, whatever you select will protect the exchanged data on one level or another.
- Flexibility: Although high-speed internet connections nowadays provide a cost-effective solution for connecting sites, they are not secure. This is when VPNs come to play. They allow mobile workers, people working from home, and branch offices to take advantage of low-cost, high-speed broadband technologies such as fiber optics, DSL, and cable while gaining access to their corporate networks in the headquarters.
- Scalability: When enterprises use VPNs, they generally depend on the internet infrastructure of the ISPs. This allows them to easily add new users without extending the corporate’s infrastructure.
- Cost: This is probably the biggest benefit of using VPNs. It allows secure connections to be established between different entities (remote users, branch offices, HQs) and exchange data in the most protected ways while at the same time using relatively cheap high-speed broadband technologies instead of dedicated WAN links. As a result, this leads to reduced connectivity costs and increased connection bandwidth.
The Important Components of VPN
VPN implementation is not a simple procedure and supports several important components that might or might not be included in the VPN implementation process. The selection and involvement of those components heavily depend on the requirements.
As a result, only the necessary components needed to meet the security policy requirements are enabled. VPN implementation may include all or some of the following components:
- Encryption: By using an encryption algorithm, the data is encrypted before it is sent through the VPN tunnel to avoid eavesdropping issues. Without the key, the data cannot be retrieved from “gibberish” into cleartext readable format.
- Authentication: This process verifies the entity's identity before the VPN is allowed to be established and access to the internal resources is provided. There are two types of authentication: user authentication, where the user usually provides a combination of username and password or a digital certificate, and device authentication, where the device is authenticated by using a pre-shared key, digital signature, or certificate.
- Integrity: With the help of hashing functions, the integrity of the data is kept, meaning the receiver can verify by the hash received that the data has not been altered in any way during transit and that the data received is in the original form.
- Nonrepudiation: This process proves that a certain communication took place between two entities in the past. This is accomplished when the receiver saves the digital signature of the sender and keeps it as proof.
- Encapsulation: This defines how the data should be encapsulated and transported across a network. In some VPN implementations, only the application layer information is encapsulated, while in others entire Layer 3 packets or Layer 2 frames get encapsulated.
- Key management: Some key management responsibilities are how keys are configured (manually or randomly generated) and derived, and how often they should be regenerated for increased security.
- Application and protocol support: The process of determining which types of traffic need to be protected with the VPN.
- Address management: Assigning internal addresses to remote clients.
Implementing Different VPN Deployment Types
VPNs can be implemented in many different shapes and forms. It is a common mistake and big paradox that implementing a VPN always produces the same protection “result” — meaning it provides the same type of connectivity, security, and other related matter.
In other words, the VPN is not a single security feature that is either on or off but a combination of many different components that define the VPN itself.
Based on the criteria, VPNs can be classified into different types. For example, based on the underlying technology, there are IPsec VPNs, SSL VPNs, and MPLS VPNs, among others.
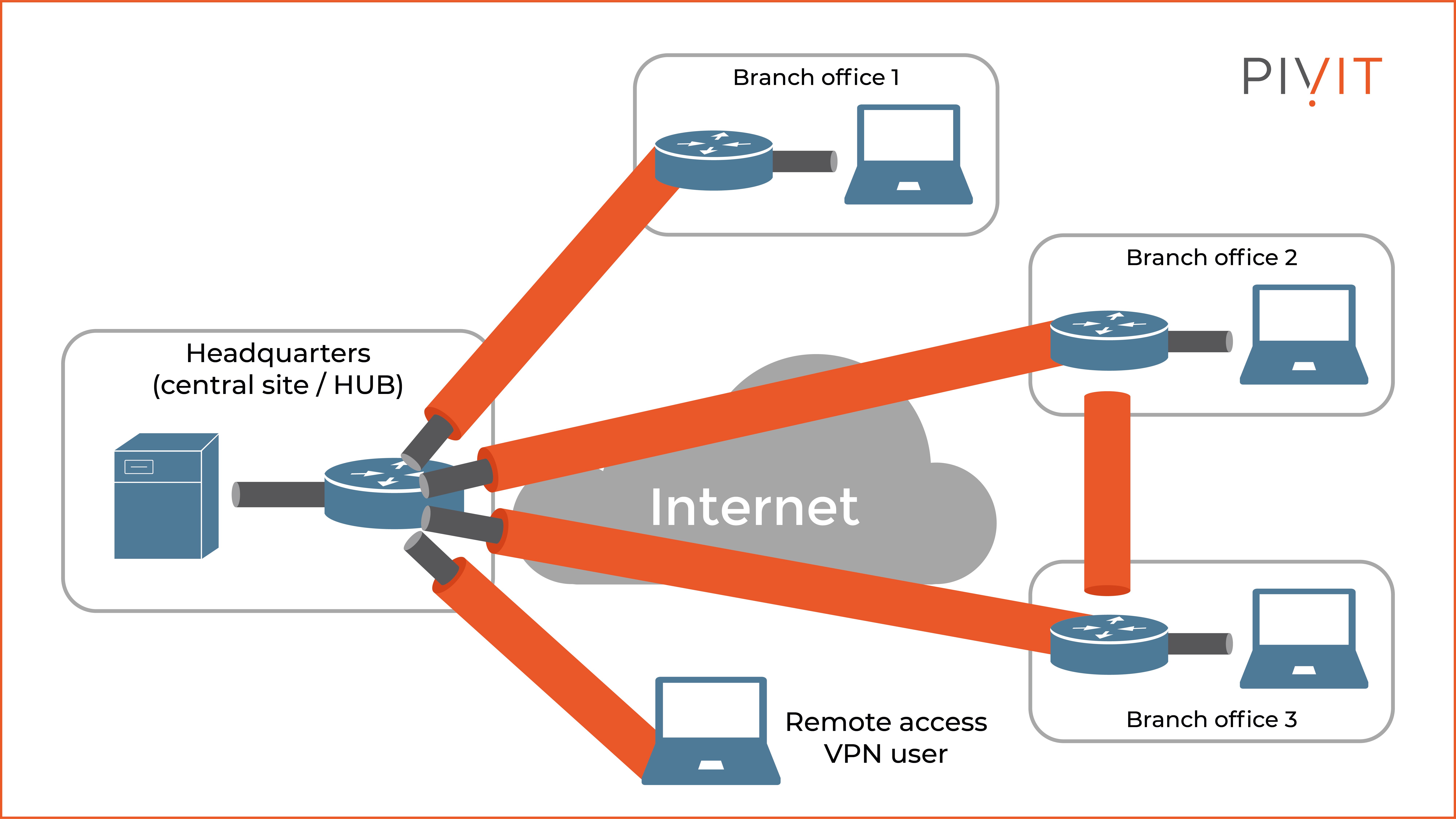
Based on the OSI layer, you can implement Layer 2 MPLS VPNs and Layer 3 MPLS VPNs. Based on deployment mode, the most commonly used criteria, we have site-to-site VPNs and remote access VPNs.
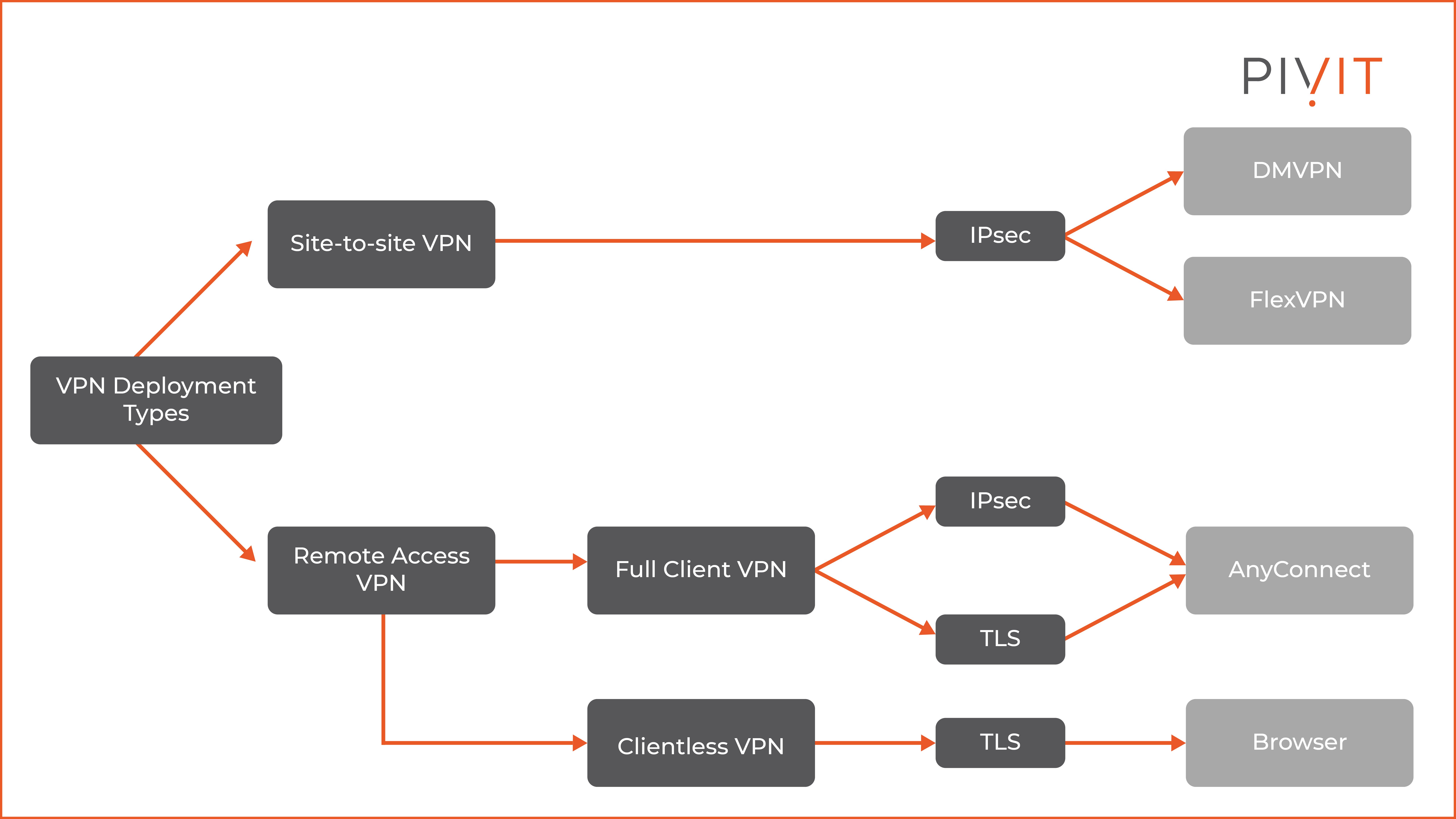
These two VPN deployment types typically use IPsec or TLS (commonly known as SSL) technology to protect the data sent across the VPN tunnels. As you can notice from the figure above, site-to-site VPNs always use IPsec as the underlying security framework, while the remote access VPNs use either IPsec or TLS, based on the remote access VPN type.
Additionally, appropriate access options are available based on the VPN deployment type, such as browser-based access, client-based access, and so on, but more on that later in the article.
All About Site-to-Site VPNs
A site-to-site VPN is an extension of a classic WAN network. They connect entire networks, such as connecting branch offices to the company headquarters or perhaps one branch to another.
In the past, the same deployment was accomplished through leased lines or Frame Relay connections. However, they are considered slow and obsolete according to today’s standards and have been replaced with high-speed internet connections over which the site-to-site VPNs are established.
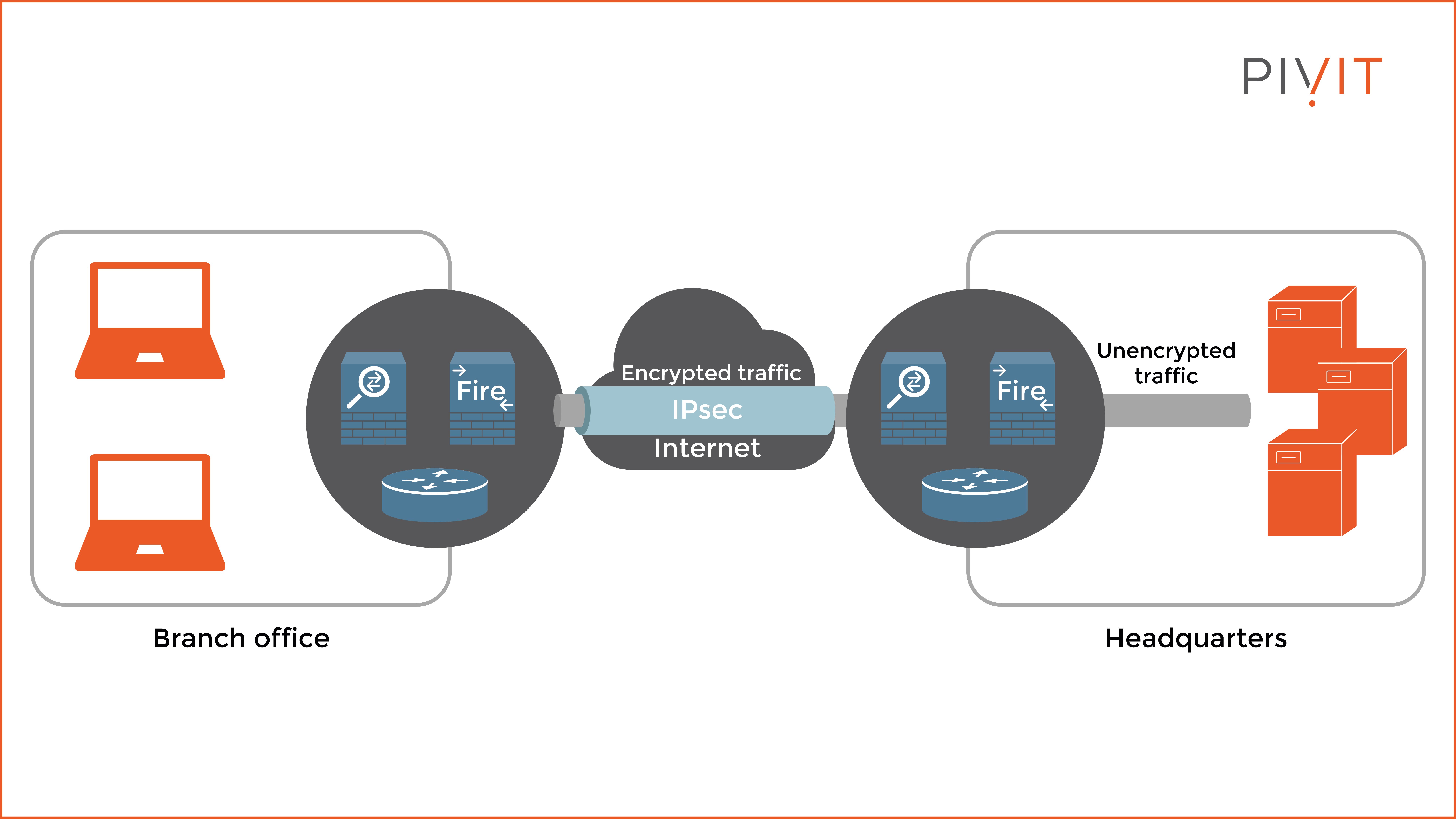
The site-to-site VPNs use the IPsec framework for protecting data, and the concept does not rely on any client software. The VPN connection is established between two devices, also known as VPN gateways. When using Cisco equipment, they can be either a Cisco IOS router or a firewall such as Cisco ASA and Cisco Firepower NGFW firewall.
Any of these devices operating as VPN gateways are responsible for encapsulating and encrypting outbound traffic and sending it through the VPN tunnel to the VPN gateway on the target site, where upon receipt, the content is decrypted, decapsulated, and forwarded to the destination host (internal resources) inside the network. In other words, site-to-site VPNs provide an always-on secure connection between two sites.
Deploying Remote Access VPNs
Remote access VPN is an evolution of dial-up connection that used to be the mainstream secure communication method in the past.
This VPN type supports the needs of telecommuters and mobile users for secure connectivity access to the company headquarters or branch office. All these types of users need is access to a high-speed broadband connection such as DSL, cable, or fiber optics, through which they can establish a remote access VPN on-demand and securely transfer data to the remote site.
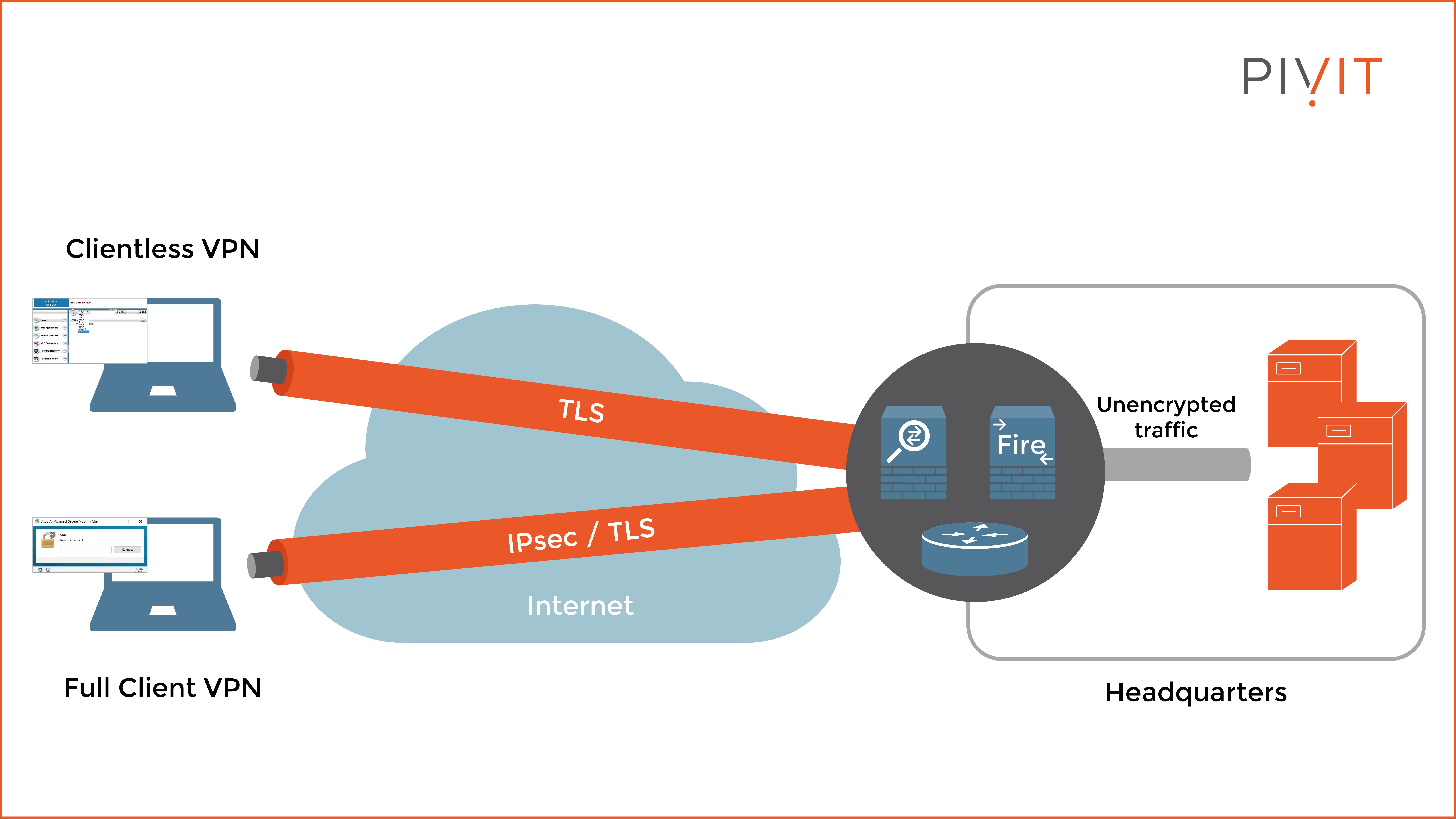
In a remote access VPN, each host usually has a VPN client installed, such as Cisco AnyConnect Secure Mobility Client. As an alternative, the user can use only a browser instead of a VPN client to access the resources behind the VPN tunnel.
The difference between these two options is that using a VPN client allows full remote access to the remote site without any limitation whatsoever, just like site-to-site VPNs. Using just a browser provides more flexibility and does not depend on a VPN client to be installed but allows only limited access based on the allowance policy applied.
The full client remote access VPN, also known as Cisco AnyConnect VPN, can use either IPsec or TLS as a framework for data protection, while the Cisco clientless SSL VPN is based on TLS technology.
__________________
Whether trying to protect a small or large data center of varying complexity, a breach in your network can cause a catastrophe. At PivIT, our certified engineers are ready to perform a site survey and provide you with the best firewall (or VPN suggestions) for your network, using a mixture of new and legacy units. Let our professionals take care of your network security needs with our EXTEND service.
__________________
Understanding Additional IPsec VPN Types
Traditional IPsec-based site-to-site VPN deployments fit perfectly as solutions only in small to medium-sized networks. However, they do not scale well, which is a great disadvantage for implementation in large networks.
Because of the direction of how IT technologies develop nowadays, the demand for IPsec-based VPNs grows rapidly among large enterprises. They not only need scalable and dynamic IPsec solutions but also as much as possible optimized network performance and bandwidth utilization through the VPNs, with as low latency as possible.
Because of the limitations of the IPsec-based site-to-site VPNs, especially with the hub-to-spoke and spoke-to-spoke topologies, today’s modern optimization requirements cannot be satisfied, so alternative solutions must be applied.
They come in the form of more flexible VPN implementations and can easily adapt to corporations' large and complex networks. These VPN solutions are called Dynamic Multipoint VPN (DMVPN) and Cisco IOS FlexVPN.
Overcoming Issues With Dynamic Multipoint VPN
The DMVPN technology from Cisco offers a large-scale IPsec VPN deployment model that overcomes the common site-to-site VPN scalability issues while allowing networks to expand and reach their full potential easily.
At the same time, the DMVPN solution supports zero-touch deployment, which optimizes the implementation and minimizes the human resources involved.
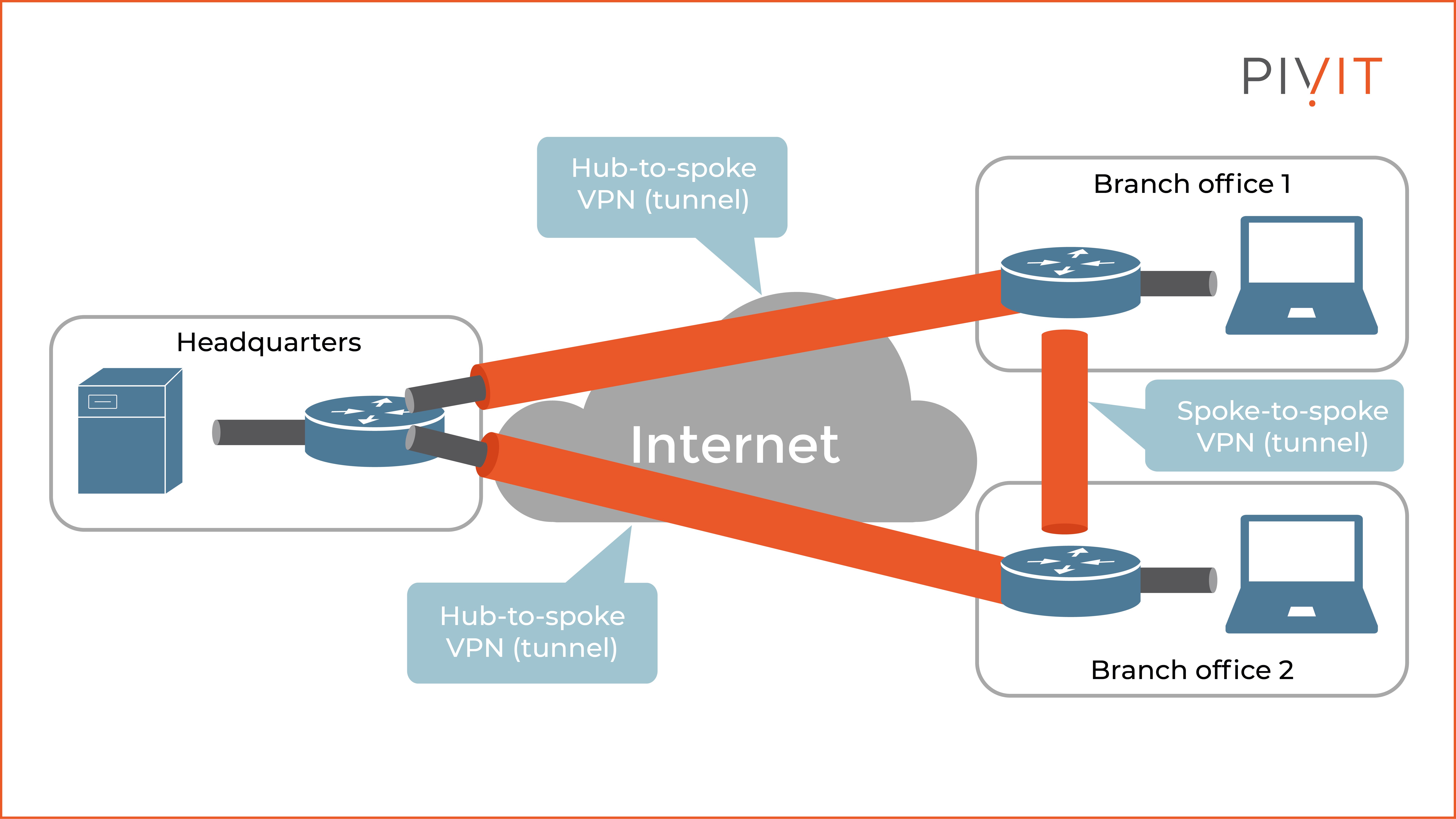
One of the biggest advantages of DMVPN is the support for IPsec VPN networks to better scale hub-to-spoke and spoke-to-spoke topologies, which are most commonly used today. As a result, the communications between the connected sites experience more optimized performance and reduced latency and jitter while optimizing bandwidth utilization.
The way the DMVPN works is quite unique. It is based on a centralized architecture that provides easier implementation than standard VPN implementations and management for deployments in which different types of VPN entities might be involved.
Because of this concept, a DMVPN deployment allows branch locations to communicate directly with each other over the internet on-demand, without any permanent VPN connection between them. The best part is that these on-demand VPNs between the branch offices are established without any involvement of the central site (the VPN hub).
As a result of this approach, the Cisco DMVPN provides many benefits, such as:
- Reducing deployment complexity through a simpler hub device (usually a router) configuration.
- Simplifying the overall intercommunications between branch offices.
- Lowering capital and operational expenses.
The Advantages of Flex VPN Technology
VPN requirements of large organizations are usually quite complex when needing to satisfy different types of connectivity requirements, and this negatively reflects high complexity and high cost when deploying various types of IPsec VPNs.
On top of that, network engineers must also learn how to implement all these different types of VPNs to easily manage and operate all those VPN connections over the internet.
The worst part is the limited support and difficulty level of migrating from one VPN type to another after the initial VPN deployment or adding extra functionalities to enhance the existing VPN implementation.
As a solution, Cisco developed the FlexVPN technology to overcome these common VPN limitations in the networks today. The Cisco FlexVPN is a unified VPN solution that simplifies the overall deployment of VPNs within large enterprises that allows all types of VPNs, such as remote access VPNs and site-to-site VPNs, among others, to coexist in a single VPN deployment.
In other words, FlexVPN allows large organizations to securely connect branch offices and remote users to each other or to the headquarters, while at the same time providing significant cost savings compared to supporting several different VPN types in parallel.
Cisco FlexVPN, as a modern VPN solution, provides many benefits, such as an easy deployment style, compatibility with third-party devices, failover redundancy, outstanding support for QoS, and support for IP multicast traffic, among many other additional benefits.
Moving Ahead With Your VPN Technology
Now that you are familiar with the backbone of the VPN technologies, the different VPN types supported, and their functionalities and benefits, you can easily start implementing the most appropriate VPN deployment type in your network.
As we all know, the internet is here to stay, connecting millions of people worldwide as a communication and data exchange. But we must all be cognizant of the risks involved, such as data loss, manipulation, and cyber-attacks.
Luckily, with such VPN technology, you can put those worries aside — and get well on your way to securely transferring data over cheap high-speed internet broadband connections.


