Your Handy Guide to Configuring ACLs on Cisco ASA

Controlling internal communications within enterprise networks is one of the essential tasks that network engineers need to do.
Although you can use many different methods to achieve policy-based communications between other parts of the network, access control lists (ACLs) are the standard feature among those.
As simple as ACLs are, they provide suitable options to filter out data traffic and routing and management traffic. Since they have been around for ages, they have been accepted as the first choice for providing filtering services on switches, routers, and firewalls, unless there are more complex requirements that they cannot satisfy.
This article will provide the following:
- An overview of interface ACLs on a Cisco ASA.
- An overview of global ACLs on a Cisco ASA.
- An explanation of the benefits they provide.
- An outline of the configuration steps for applying interface and global ACLs on a Cisco ASA.
Not what you were looking for today? View some of our popular articles:
- The Importance of Layer 3 Redundancy: Understanding HSRP – Pt. 1
- Must-Have Port Security: Simple but Efficient Layer 2 Protection
- Back to the Basics: Cisco ASA Firewall Configuration Guide
The Fundamentals of ACLs
When ACLs were developed back in the day, their primary purpose was to filter data traffic that hosts and servers were exchanging daily within networks.
However, in time, their use has expanded. Today ACLs are also used for controlling updates from routing protocols, filtering management traffic, and specifying interesting traffic for VPNs, among other services.
An ACL is a basic tool that filters out incoming and outgoing traffic on the device interfaces based on the Layer 3 and Layer 4 header information inside the packets. It is a sequential list of rules that define a permit or deny action upon which the packets' processing is based. Once configured, these statements operate in sequential logical order from top to bottom.
Remember that configuring the correct entries does not mean they will perform as expected. If the order in which the entries are placed is wrong, you might get different results. Therefore, you should always place the more specific entries at the top and the more general ones at the bottom.
Check out this article to learn more about ACLs in general, including their functionalities and uses cases.
_________________
Hardware Options For You
We make it easy for you to find the routers or switches you need to configure ACLs. Click below for hardware options or reach out to us and share the project you are currently working on.

_________________
ASA Interface ACLs Overview
Although applying interface ACLs on Cisco ASA interfaces is optional, it is the most commonly used access control mechanism.
Once the interface access control rules are configured, they permit or deny applications to establish their sessions through the ASA firewall based on criteria such as input and output interfaces, source and destination IP addresses, and source and destination ports.
When you configure interface access control rules, they control only transit traffic, meaning they only filter traffic that passes through the appliance. All other traffic destined for the appliance, such as management and ICMP traffic or VPN tunnels, cannot be controlled by the interface access control rules. The same applies to traffic initiated by the Cisco appliance.
Access control rules are configured on an interface and evaluated sequentially from top to bottom. When a rule is matched, the corresponding action is applied, and the matching does not continue to the next rules. The last rule is always an implicit deny and drops the traffic that is not explicitly allowed by any previous access rules.
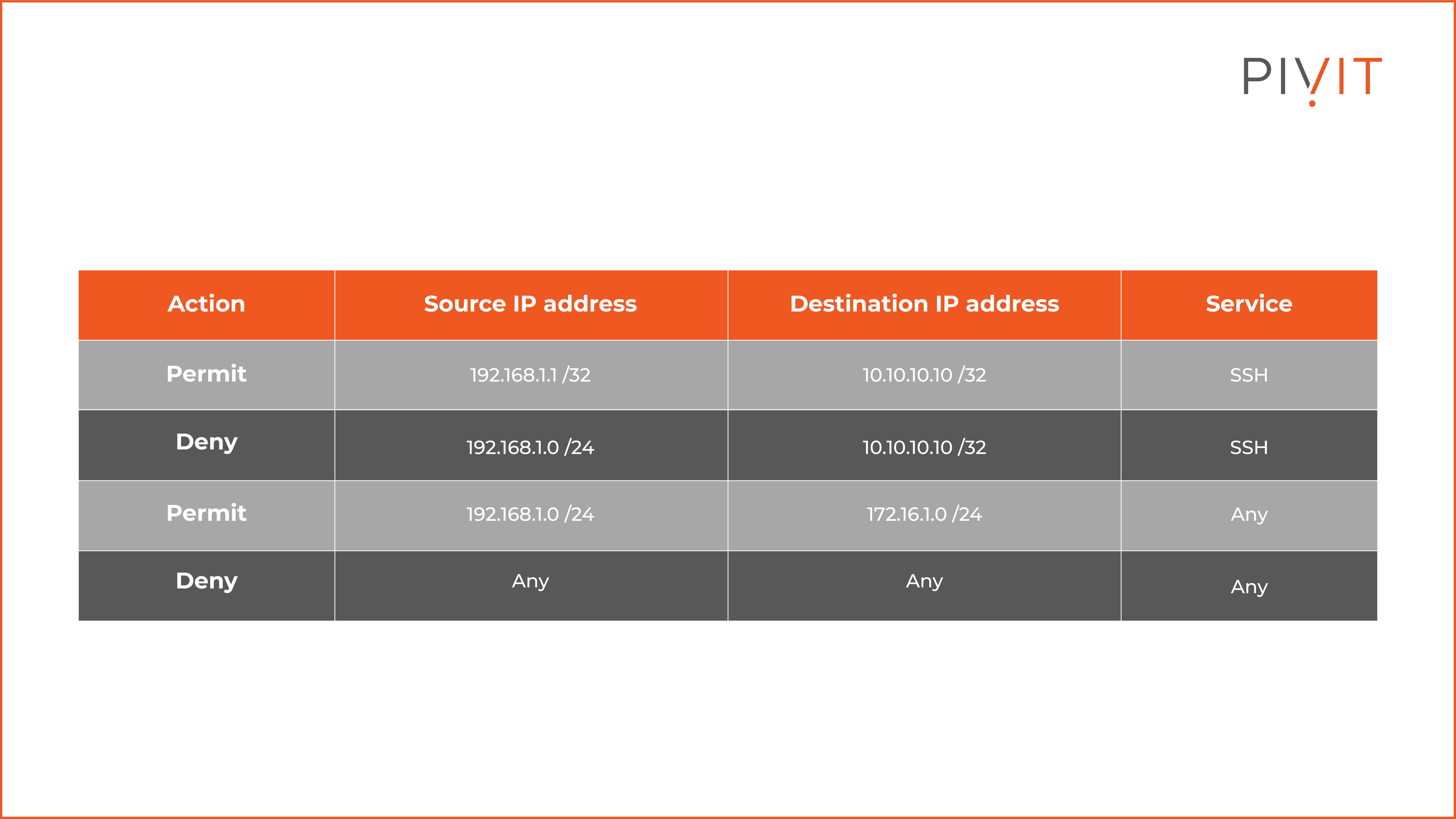
The table above represents an interface ACL consisting of several rules.
As you can see, the first rule permits the host with an IP address 192.168.1.1 to establish an SSH session to the 10.10.10.10 IP address, while the second rule denies the rest of the hosts in the same 192.168.1.0/24 subnet to establish SSH to the same destination IP address.
The third rule allows the same subnet to make any type of connection to the 172.16.1.0/24 subnet. The fourth rule is the default implicit deny rule and denies everything else.
You can apply the interface access control rules on a Cisco ASA interface's input and output direction. When applied in the input direction, the rules filter the incoming traffic accepted on that interface.
On the other hand, when access rules are applied in the output direction, they filter the traffic that should be sent out from that interface.
For data traffic to pass through the Cisco appliance, it must be permitted by all interface access rules applied in the direction of the traffic flow across the appliance. A common strategy is to use only input access rules on all interfaces.
This guarantees that the traffic will pass through interface access rules only once. Regardless of this recommendation, it is sometimes easier and more optimized to apply output rules instead of input ones on the interfaces.
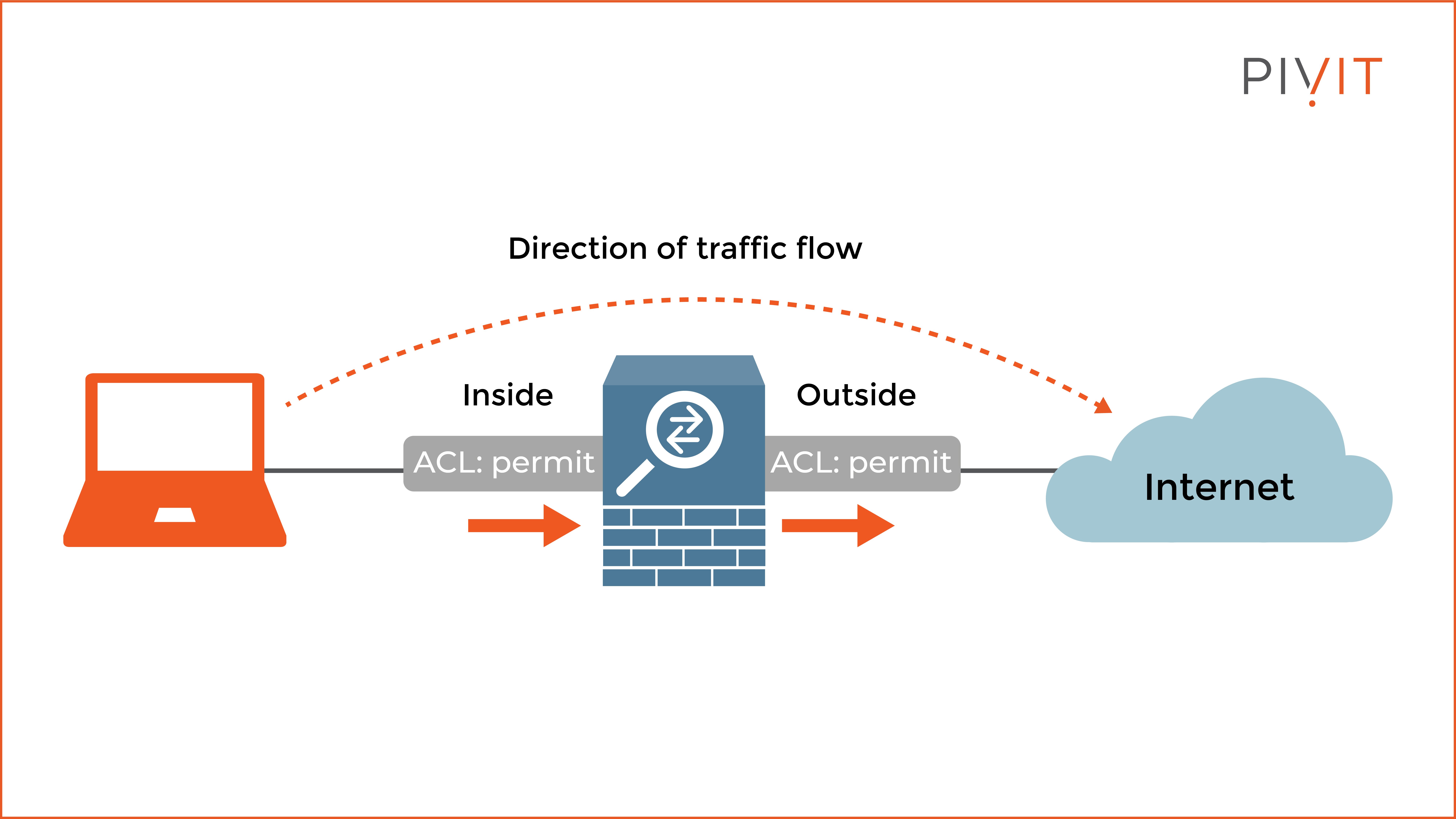
As you can see in the image above, all access rules applied on the Inside and Outside interfaces on the appliance in the input and output direction, respectively, must permit the traffic so that the computer can communicate on the internet.
Remember that if you do not apply interface access rules on the ASA appliance, all interface default policies stay in charge. This means all outbound connections will be permitted on the appliance while all inbound connections are denied.
Another essential thing to remember is that the ASA appliance is a stateful packet filtering device. Hence, an access rule must permit only the initial packet of a traffic flow for the appliance to inspect the application statefully.
Learn more about the Cisco ASA appliance and its functionalities.
Configuring Interface Access Rules
The configuration process of interface access rules on the Cisco ASA appliance is quite simple and can be done through the CLI or ASDM tool. Since ASDM is always a preferred approach, we will use this management tool to define several interface rules.
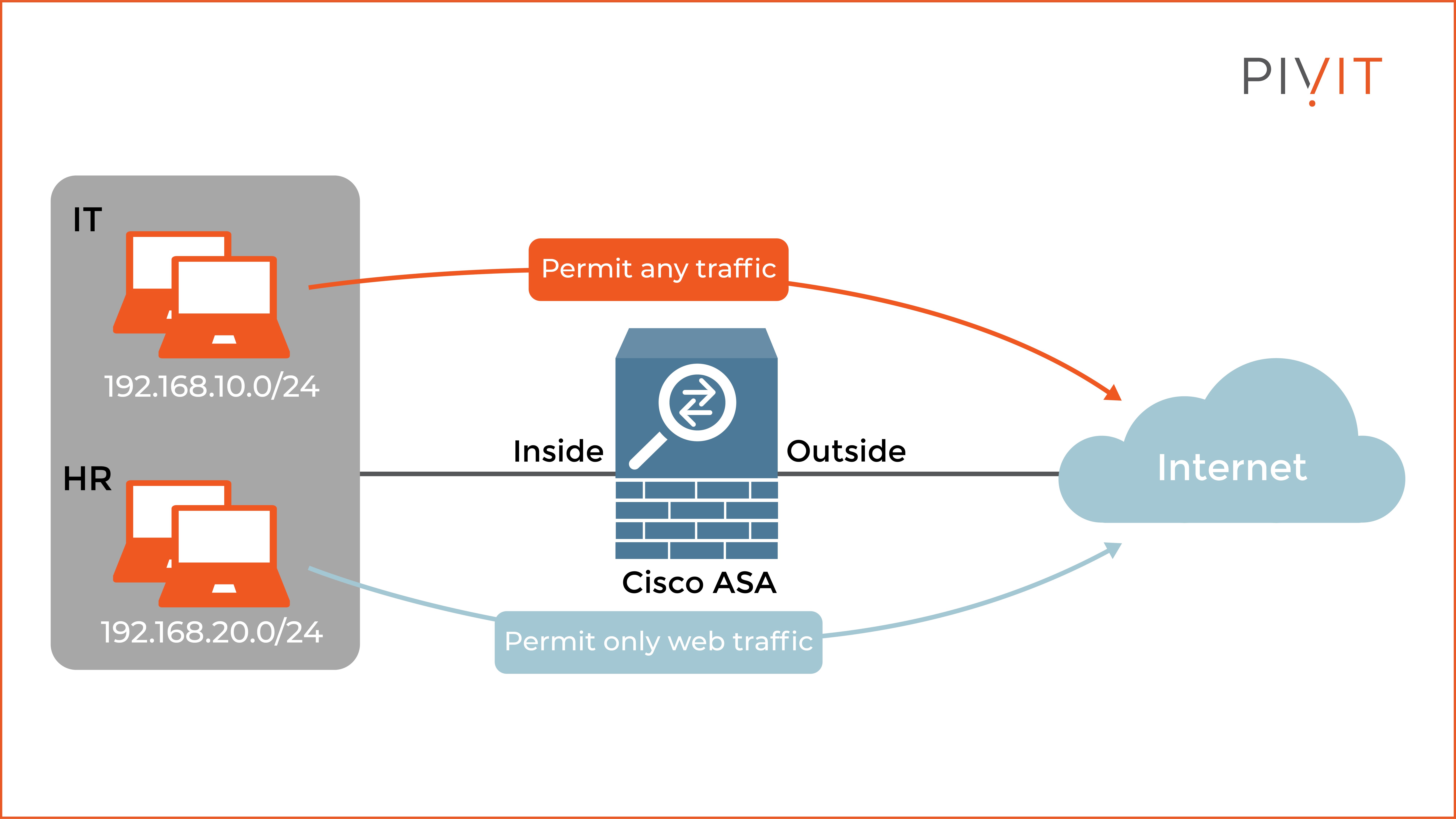
As you can see in the image above, the goal in the scenario is for the IT department to be allowed to use any service when communicating on the internet.
In contrast, the HR department is limited to web traffic only. To accomplish this requirement, you must configure two rules and apply them on the Inside interface in the inbound direction.
To permit the HR department to use web communications on the internet, you should make the following configuration:
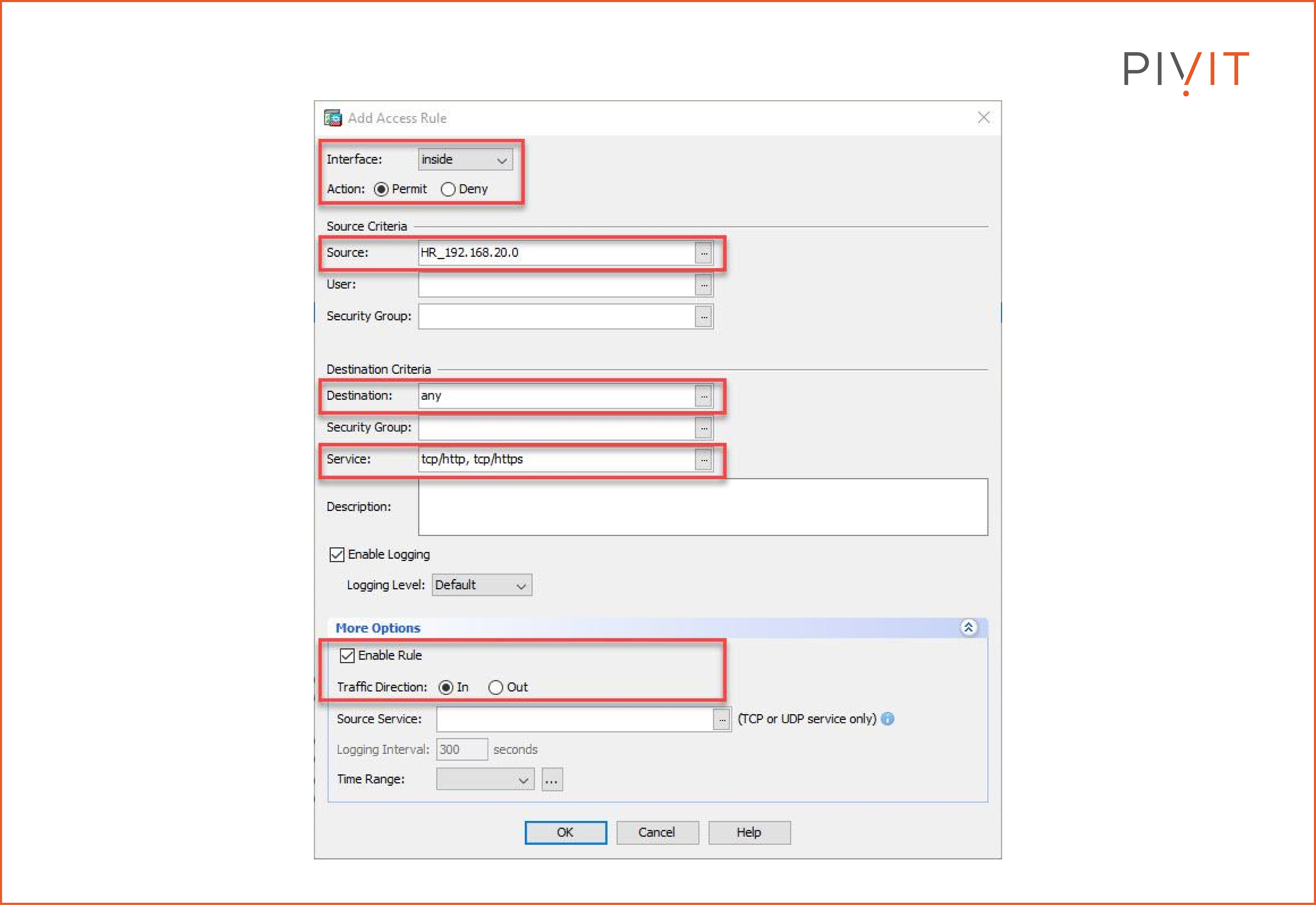
To permit the IT department to use any service on the internet, you should make the following configuration:
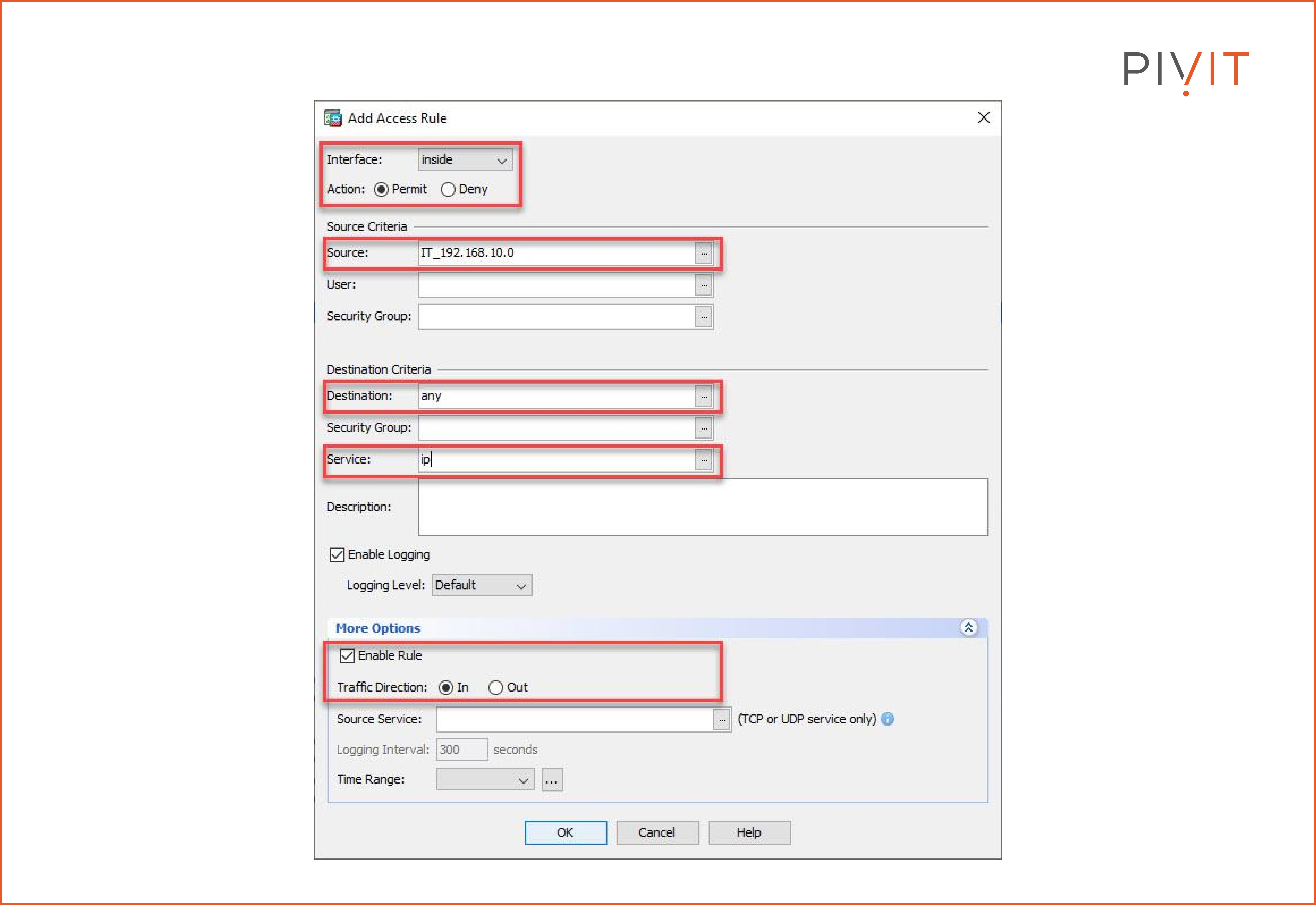
The implicit deny rule will deny the rest of the traffic not permitted by the access rules above.
If you run into any issues when configuring an ACL or simply need an extra set of hands to help in the configuration, we have a team ready to step in to configure your network through our SmartHands offering.
ASA Global ACLs Overview
Global access rules were primarily designed to simplify the management of access rule configurations on the appliance. Although global ACL applies to all interfaces only in the inbound direction, the entries are defined in the same way as interface access rules.
When you configure a global ACL, it is always used as a last resort — meaning traffic that does not match an input interface ACL gets compared against the global ACL rules. However, if you want to define specific interface access policies that differ from those in the global policy, you must configure interface access rules on those interfaces.
Remember that the global ACL overrides all implicit interface access policies on the appliance. At the same time, the implicit deny interface rules are replaced with an implicit deny rule in the global ACL. Regardless, if the goal is to permit specific traffic through the appliance, a permit statement is needed either in the interface input access rules or in the global ACL rules.
When both interface and global ACLs are configured, the Cisco ASA uses the following order to match access rules:
- Interface access rules are matched first.
- Global access rules are matched only when no interface access rules are matched.
- The implicit deny rule in the global ACL is used.
Configuring Global Access Rules
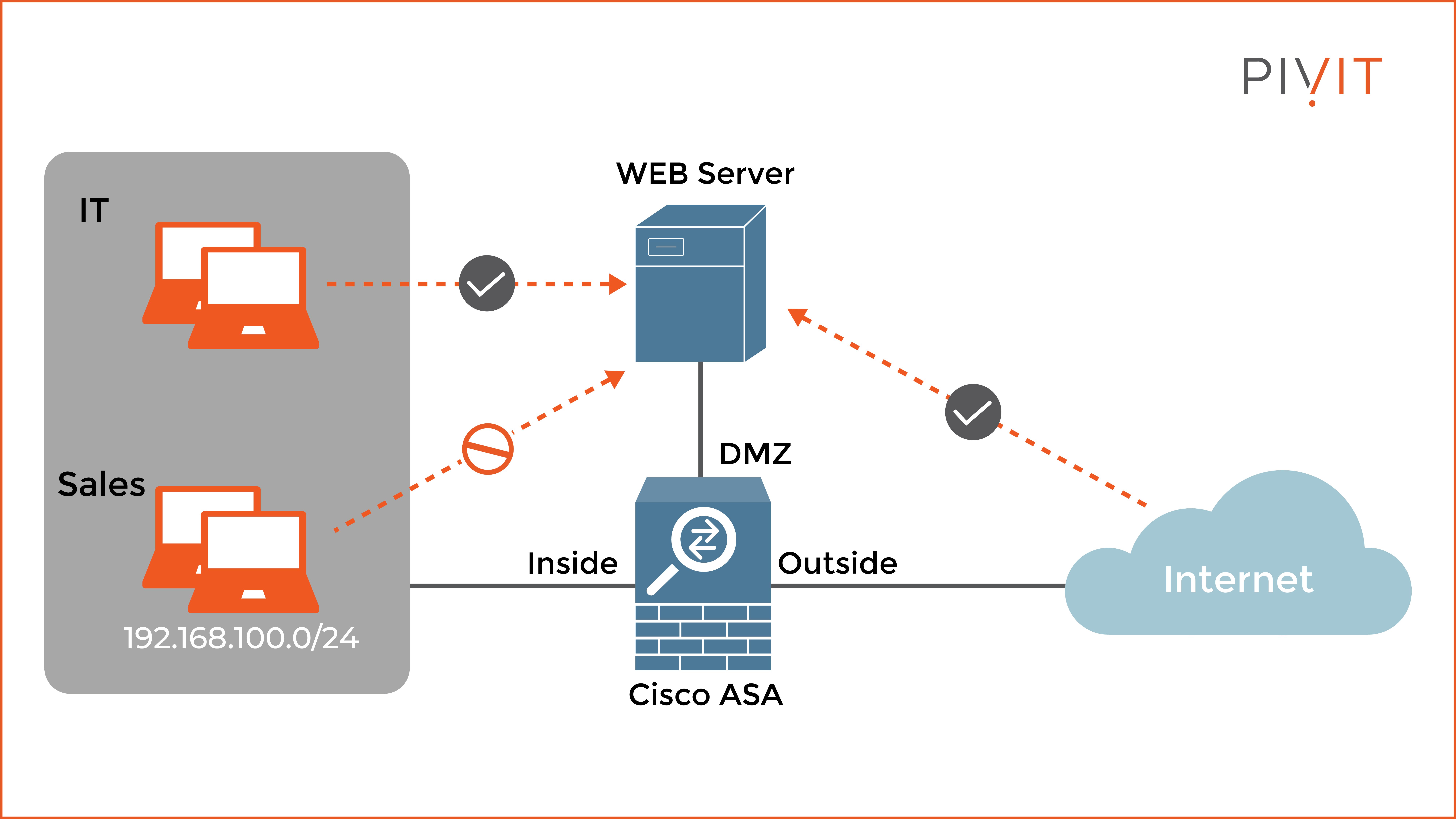
The configuration process of global access rules on the Cisco ASA appliance is similar to the configuration of interface access rules. To better understand the configuration of the global ACL, we will have the following use case.
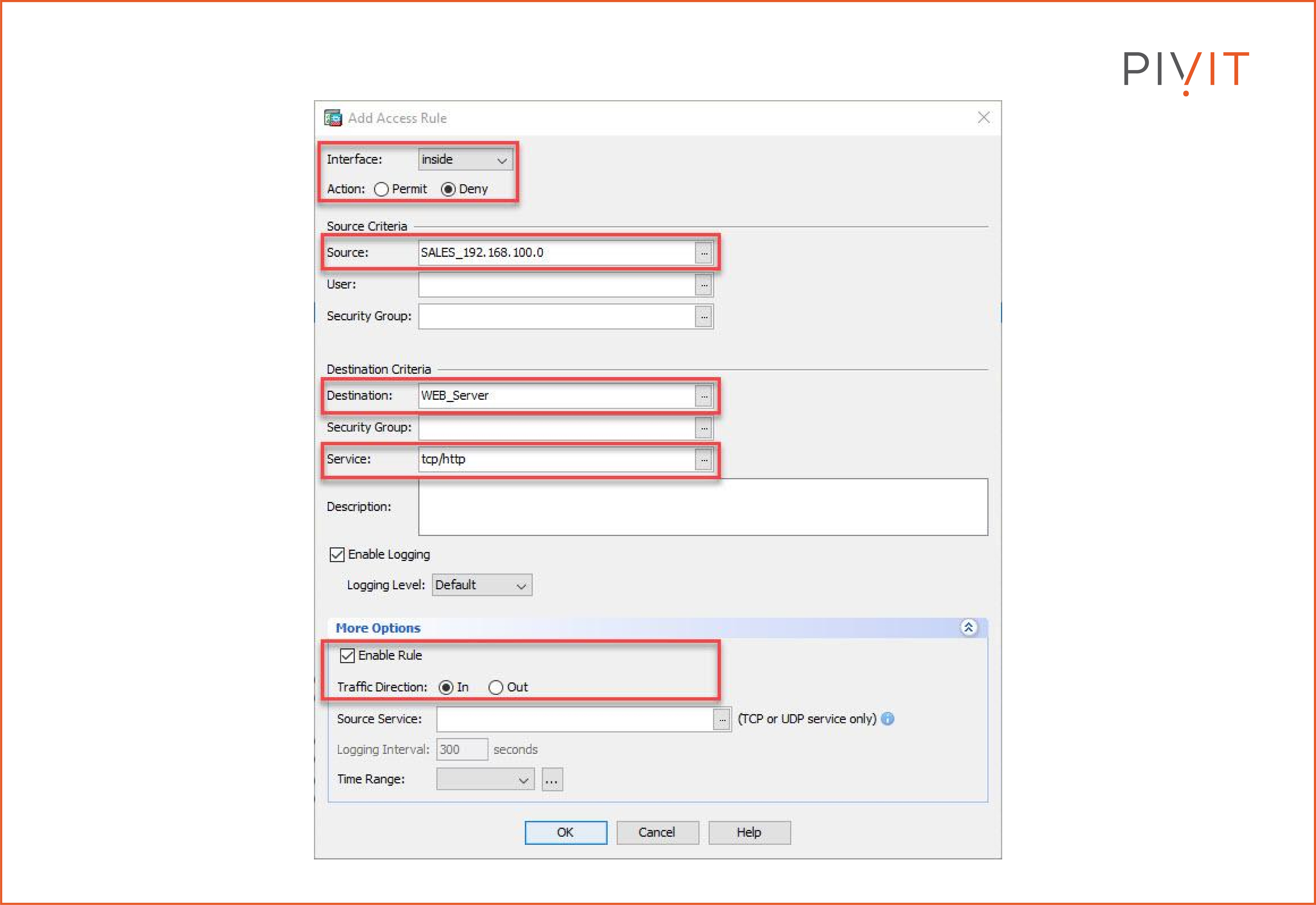
As you can see in the image below, it is required to permit all HTTP traffic to the server globally while denying HTTP traffic from the internal 192.168.100.0/24 subnet at the inside interface representing the Sales department.
To deny the Sales department HTTP communications with the web server, you should make the following configuration:
To permit HTTP communications with the web server from all the other sources, you should make the following configuration:
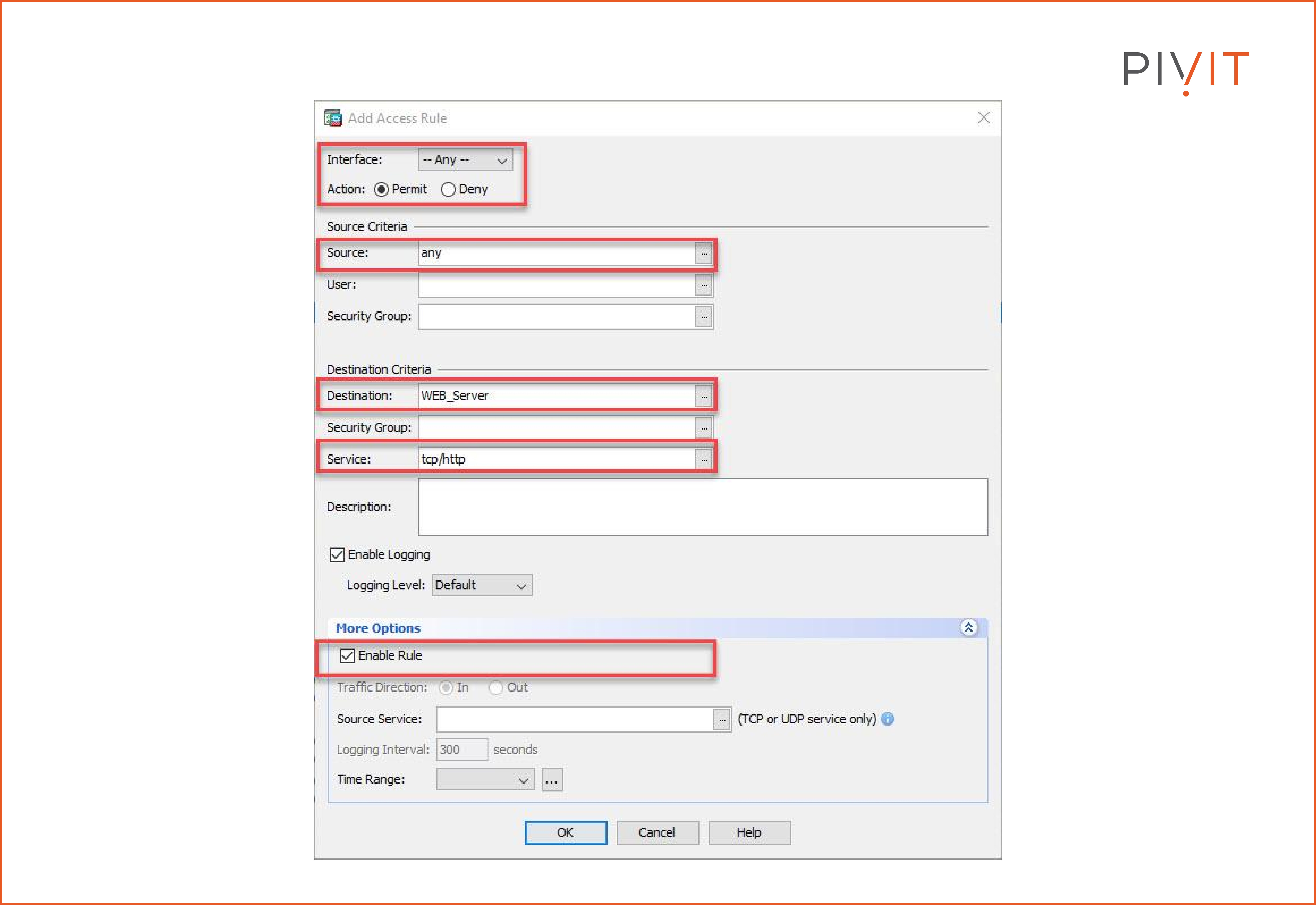
The global access rules are not applied on a specific interface but are used only on all interfaces in the inbound direction. That is why, in the configuration steps, “Any” is selected for the interface.
A Simple Yet Efficient Filtering Method
Although more advanced filtering features are supported on network devices, nothing beats the access rules that can be applied globally or on a specific interface.
Implementing ACLs does not require you to have special knowledge about them, which makes them always the first choice when specific traffic needs to be filtered when passing through the appliance.
After all, as simple as they can be, the ACLs always get the job done.

