5 Dangerous Network Security Threats to Be Aware of in 2023

As we move into a new year, it’s time to revamp your organization’s cybersecurity strategy. If supply chain issues, long lead times, and global economic uncertainties aren’t enough, cyber threats will likely become more sophisticated.
At least, that has been the trend for the past few years, with attack intensity and frequency both rising dramatically.
Enterprise networks are the most common targets of various cyber-attacks. Naturally, it’s your IT infrastructure’s most critical component to secure against such attacks. But knowing and understanding these threats is also important to take necessary preventative measures.
In this article, we will:
- Study the top network threats in 2023.
- Explain how to prepare for new threats.
- Suggest taking a holistic approach to network security.
Looking for more great articles? Try these out:
- Must-Have Port Security: Simple but Efficient Layer 2 Protection
- Your Best Security System: Cisco ASA vs. Fortinet FortiGate
- Configure Network Security Using an ACL in SVI Environments
Top Network Security Threats in 2023
Any security incident is terrible, but some may do irreversible damage. The thing about cyber attacks is that even if they don’t cause much financial harm, they can stain your reputation. Whether you’re a B2B or B2C business, news about attacks can hurt a business one way or the other.
So, what cyber threats do you need to be aware of to protect your networks? Here are the top five:
Ransomware
Unsurprisingly, ransomware attacks are likely to be expected next year as well.
According to the Verizon 2022 Data Breach Investigations Report, ransomware attacks were up by 13 percent in 2022 and were more than the attacks in the last five years combined.
Ransomware is malware that typically blocks access to networks and data, and attackers demand a ransom to release access. They use sophisticated malware to creep into the network by exploiting vulnerabilities and gaining authorization for data access.
What is more dangerous now is that there is ransomware-as-a-service (RaaS) that malicious parties online are selling to third parties that then use to carry out attacks on their enemies. These attacks would create even more menace as more bad actors, who otherwise may not have the resources to make such an attack, can breach networks.
Cloud Breaches
Six out of ten businesses are using the cloud for their work. More companies are following suit and relying on the cloud for applications and data storage. While the cloud offers tremendous business benefits, it’s not entirely immune to cyber attacks, including ransomware.
Cloud breaches are on the rise as attackers exploit security loopholes of cloud providers and gain access to their client's data. As per one report by Check Point, 27 percent of organizations experienced cloud breaches in 2021.
Cloud breaches can also result from your errors, such as not using multi-factor authentication, configuration errors, or weak access control.
IoT Attacks
Would you believe an IoT device is under attack within five minutes of connecting to the Internet? That’s what the 2018 NETSCOUT Threat Intelligence Report says.
Attackers are ready to exploit these Internet connectivity-enabled intelligent devices that are now common in today’s enterprises. From a smart refrigerator in the break room to thermostats on the floor, these devices may be connected to the same network as other critical devices in your organization.
Any security vulnerability in connection with IoT devices can expose your entire network.
Human Errors
More often than not, cyberattacks are a direct result of human errors. From weak passwords to misconfigurations in security settings, bad actors can easily exploit human-created vulnerabilities online. The Cost of a Data Breach 2022 report by IBM says human errors cause 23 percent of breaches.
No matter how comprehensive your network security strategy is, not training your employees on security, especially those who access critical parts of the infrastructure, is a grave mistake.
Social engineering attacks like phishing and spoofing can also count as human errors to some extent, as people fall prey to these tactics. Again, such attacks will continue to be a problem, especially for large organizations with hundreds or thousands of employees.
Political Attacks
The political situation going into 2023 is quite sensitive. In any future conflict, much like present conflicts, cyberattacks will play a key role. So it would be naive to discount the possibility of a politically-driven attack to hamper your networks.
Even though such malicious parties (often state actors) target government infrastructure, it’s not unusual for organizations to become victims. They want to cause maximum damage, and hacking or damaging networks of revenue-generating enterprises can easily make it to their agenda.
________________
Let PivIT handle your firewall installation and configuration with EXTEND, a seamless and confidential extension of your IT teams. Consider us your feet on the street, working to cost-effectively extend your reach and complete your projects.
________________
How to Prepare for Security Threats in 2023?
You can safeguard your network and organization from the above threats by taking measurable actions. Here are some recommendations:
Next-Generation Firewall (NGFW)
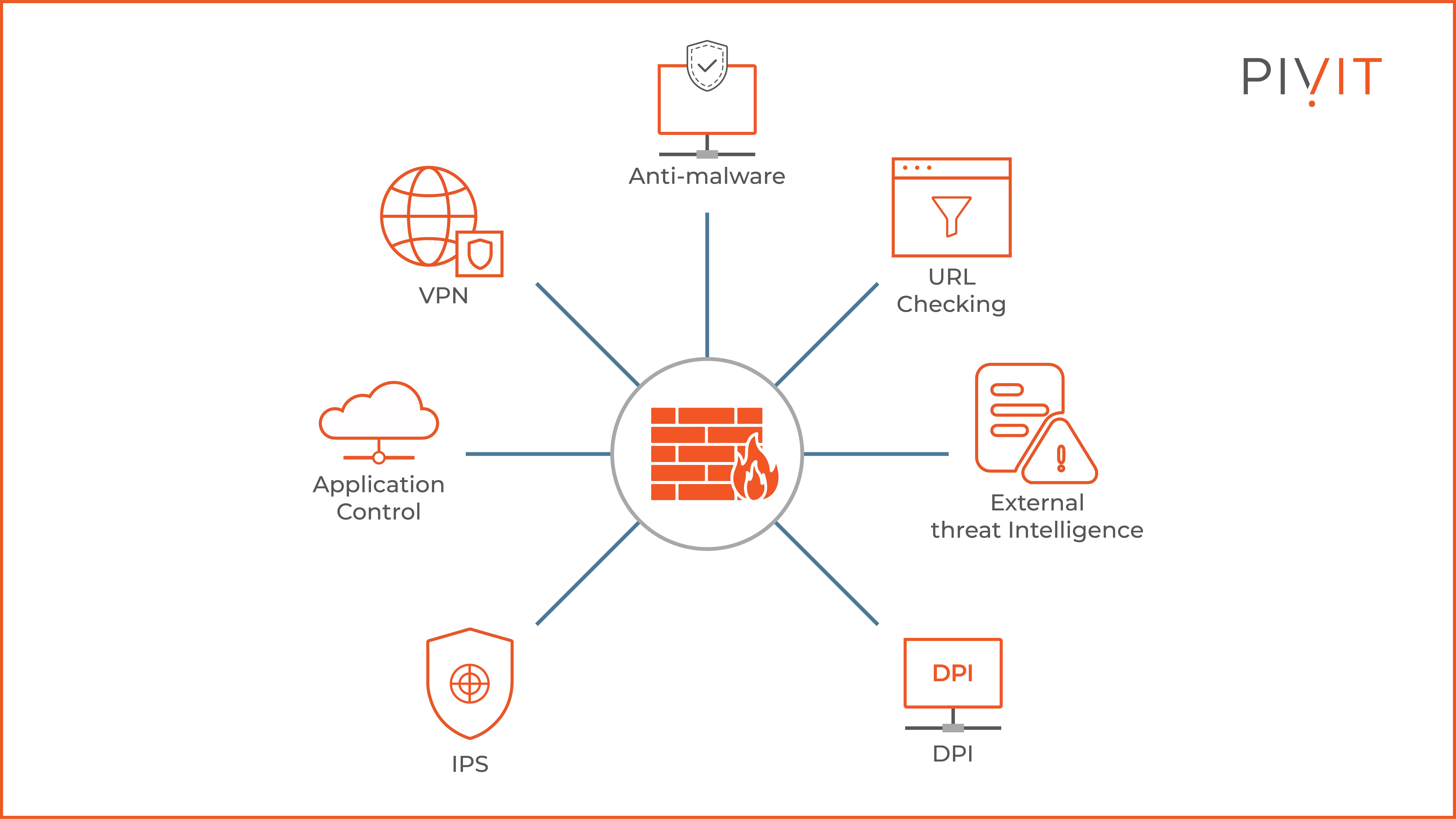
Your standard stateful firewall device may work well, but a next-generation firewall (NGFW) is a better option for more robust security. An NGFW adds additional layers of protection in addition to monitoring traffic in and out of the network.
But organizations should also select the firewalls according to their performance needs. For instance, Cisco Firepower 9300 Series firewalls are ideal for data centers requiring higher throughput and lower latency.
Threat management and mitigation are also vital, which sophisticated firewalls by Fortinet can provide.
Timely Network Maintenance
Maintaining your network, especially legacy components, is vital for preventing attacks. Typically outdated or unsupported legacy hardware exposes the entire network to threat. At the same time, it’s sometimes difficult to let go of such systems because of budgetary issues or the sheer complexity of upgrading.
And in the case of legacy equipment, there’s simply no OEM maintenance, or it’s too expensive. That doesn’t mean that you should leave it without proper coverage. Having third-party care like that by OneCall can help keep legacy equipment running beyond its service life.
Network Security Monitoring
The most crucial part of network security is monitoring. You need to actively monitor the state of the network to detect vulnerabilities before attackers stumble upon them. It may include using network management software with monitoring tools that monitor user behavior and hardware configurations.
With round-the-clock security monitoring, you can also monitor access and privileges. For instance, the network should promptly update permissions as soon as someone's role changes, which also impacts their access privileges.
In addition to monitoring, adopting better security architecture such as Zero Trust can also help.
Cyber Security Training
Human errors are also a significant threat to your network’s security, so it’s imperative to provide regular security training. From technical experts like hardware engineers to end users who connect to the network with their devices, it’s critical to provide education about known threats and the best security practices.
Many organizations make the mistake of spending too much time and effort implementing technological security measures and ignoring the human factor behind common cyber attacks.
Take a Holistic Approach to Network Security!
Improving network security should be one of your top priorities going into 2023. With cyber threats becoming ever more common (and devastating), investing in better hardware and software for security and maintaining existing infrastructure well is essential.
PivIT can provide the latest network hardware, including firewalls critical for security. Firewalls can enhance security by preventing malicious requests from entering the network. The NGFWs from Cisco, Palo Alto, and Fortinet provide advanced traffic monitoring, a cornerstone of network monitoring.
That said, your hardware provisions for security should be combined with robust security software solutions and adequate training — only then can you expect your network to withstand common cybersecurity threats.



